social engineering penetration testing
What is social engineering penetration testing?
Social engineering penetration testing is the practice of deliberately conducting typical social engineering scams on employees to ascertain the organization's level of vulnerability to this type of exploit.
What is social engineering?
Social engineering is a type of cyberattack where the attack vector relies heavily on human interaction. The attackers use human emotions and tendencies against their victims. One attacker might use fear to achieve their aims, another might use flattery and a third might use fake news.
In all these cases, they attempt to bypass an organization's technical security measures and exploit what's hard to predict and even harder to control: human vulnerabilities. The goal is usually to get the victim (or victims) to part with the organization's money or confidential information.
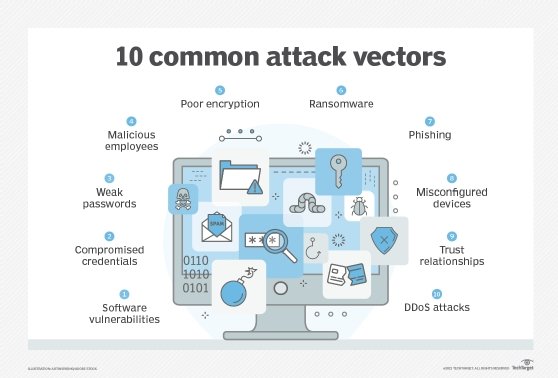
Some common and popular social engineering tactics are as follows:
- Phishing. With this tactic, fake emails are sent to victims to encourage them to click on malicious links or download malicious attachments.
- Scareware. Scareware is used to scare the victim into downloading malicious software.
- Baiting. This tactic makes false promises to lure a victim into a trap.
- Honeytrapping. The attacker sets up a fake online profile to build a relationship with the victim to trick them into parting with money or personal information.
- Business email compromise. Business email compromise allows one to pretend to be someone trustworthy to gain a victim's trust and get them to do something they wouldn't normally do, such as transfer large sums of money to an unknown bank account (that belongs to the attacker).
- Tailgating. Tailgating is a physical breach in which an attacker gains access to a physical facility by following an employee or asking them to grant them access (e.g., by holding the door or by swiping their electronic ID card).
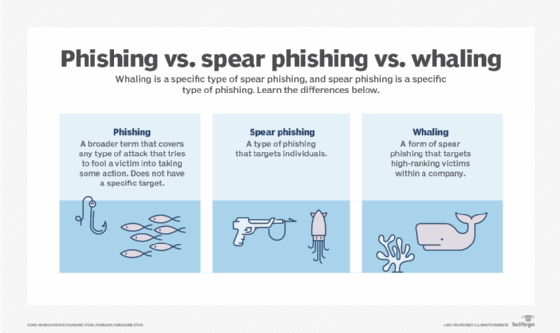
What is a social engineering penetration test?
A social engineering penetration test (or pen test) is a specific type of ethical hacking exercise that's aimed at testing people rather than systems. It assesses how vulnerable an organization's employees are to social engineering attacks. The pen tester might conduct different types of attacks to identify where people are susceptible and to design a remediation plan. It is aimed at minimizing the probability and risk of such attacks to the organization.
The exercise is also meant to test employees' adherence to the organization's security policies and practices, say, about not opening emails from unknown senders or always verifying the identity of unknown people who claim to be "colleagues" or "from the IT department" or a "vendor." A thorough social engineering pen test might reveal that employees are not adhering to these policies and are placing the organization at risk.
Social engineering penetration test process
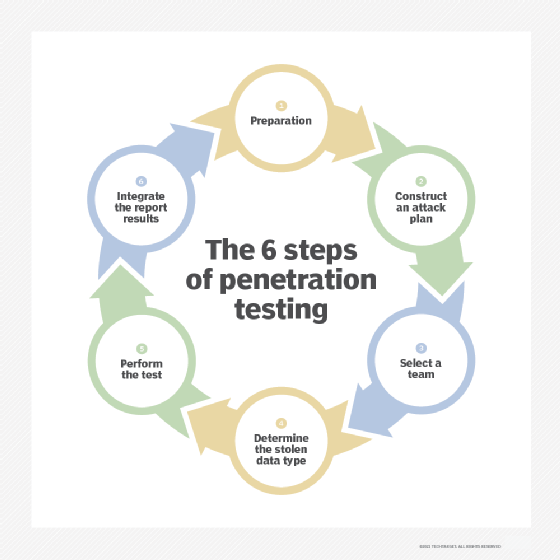
Social engineering pen testers follow a systematic method to author and execute social engineering attacks. They first gather information about the target, usually via active and passive reconnaissance and by using open source intelligence (OSINT). They also select their "victims" and then engage with them using many of the same methods and tools real attackers use.
Additionally, testers plan the test scope and identify the methods they will use during the test. They will execute the tests per the defined scope, document their findings and report the findings to management. The pen test report clearly highlights the discovered risks and the potential impact of each risk and includes the tester's recommendations to remediate those risks.
Benefits of social engineering penetration testing
Besides revealing how susceptible employees are to social engineering attempts, a social engineering pen test can help organizations with the following:
- Identify the information or assets an attacker could target.
- Develop (or improve) a security awareness training program.
- Evaluate the effectiveness of existing security controls at preventing social engineering attacks.
- Determine what kind of new controls are needed to strengthen the security infrastructure.
Types of social engineering penetration tests
Social engineering testing can be conducted as part of a more comprehensive pen test. As with other pen tests, social engineering pen testers use the same methods and tools real-world intruders would use to attack the organization.
On-site testing
On-site testing is usually physical testing. It might involve a tester trying to enter a secured building when many employees are entering to see if someone just holds the door open rather than adhering to the approved procedure of letting the door close after them so any person following must use an employee card or badge for entry.
Holding the door open increases the possibility of tailgating, which can allow the threat actor to do a host of things that can harm the organization, such as the following:
- Conduct reconnaissance.
- Install malware on employee systems.
- Steal unattended devices.
- Access online/physical confidential files lying unprotected on employees' computers or desks.
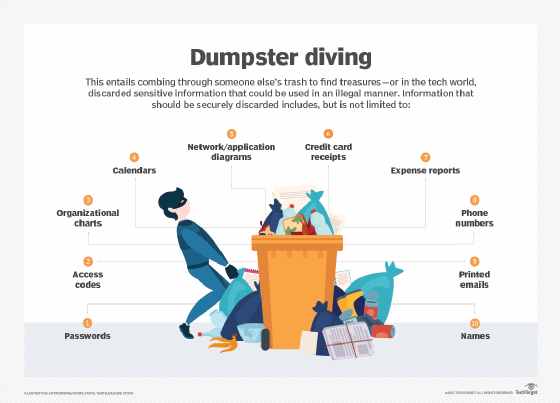
Besides tailgating, the tester might also use other on-site attack methods such as impersonation (pretending to be someone trustworthy or known to the victim), dumpster diving (go through trash or sticky notes to gain useful information about the organization), or USB drops (drop a malware-infected USB device in a common area to get a potential victim to pick it up and plug it into their own system, thereby infecting it).
Remote/off-site testing
Testers usually conduct off-site testing remotely and via electronic means.
Phishing exploits, a common off-site social engineering testing method, are used to test employee vulnerability to fake/malicious emails. Testers might send an email purportedly from someone in management asking the employee to open an unexpected attachment, provide sensitive information or visit an unapproved website. Or they might send the victim a test message to lure them into clicking on a malicious website link. When they do, they will be prompted to either download malicious software or provide sensitive data into an online form. This type of social engineering attack is known as smishing (SMS and phishing) and is increasingly used by pen testers to assess employees' vulnerability to such increasingly common scams.
Social engineering penetration tests best practices
Social engineering pen testing should provide a company with information about how easily an intruder could convince employees to break security rules or divulge (or provide access) to sensitive information. The test results should also provide a better understanding of how successful the company's security training is and how the organization stacks up, security-wise, compared to its peers. To promote this understanding, a detailed pen test report, written in audience-friendly language, is crucial.
But even before the test starts, it's important to perform thorough reconnaissance about the target and gather as much information as possible about them. This information helps to clarify the test scope and ensure it's executed correctly.
Finally, it's important to address all the vulnerabilities identified during the pen test and implement all required measures to plug the gaps and prevent an actual attack. Organizations can also prevent social engineering attacks by implementing these controls:
- Regular security awareness training.
- Clear password policies.
- Multifactor authentication (MFA).
- Incident response planning.
- Regular security assessments (including pen tests).
- Security monitoring systems.
- Identity and access management (IAM) controls.
- Zero trust security.
- Software and systems patching.
Social engineering attacks are becoming more sophisticated and more damaging. Penetration testing is one of the best ways to learn how to safeguard your systems against attack. Learn more on how to conduct a social engineering penetration test.
