What is red teaming?
Red teaming is the practice of rigorously challenging plans, policies, systems and assumptions with an adversarial approach. A red team might be a contracted external party, an internal group or a combination of internal and external resources that uses strategies and tactics to encourage an outsider perspective.
The goal of red teaming is to overcome cognitive errors like groupthink and confirmation bias, which can impair the decision-making or critical thinking ability of an individual or organization. Another goal is to determine if existing detective, preventive and mitigation measures are effective for a wide range of attack vectors.
Often, a group of internal IT employees, a red team is used to simulate the actions of those who are malicious or adversarial. From a cybersecurity perspective, a red team's goal is to breach or compromise a company's digital security. A blue team, by contrast, is a group of internal IT employees used to simulate the preventative actions of individuals or departments responsible for security operations. The blue team's goal is to stop the red team from committing hypothetical cyberattacks, such as a data breach or phishing attack. Such interaction is what's called a red team-blue team simulation. Figure 1 depicts red and blue teaming for cybersecurity.
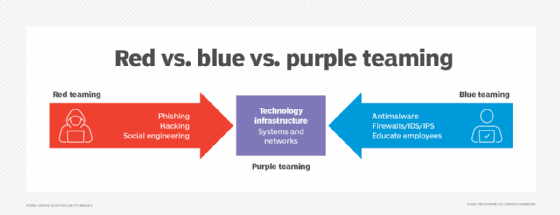
Red teaming does not require the existence of a blue team. An organization might seek to compare the active and passive systems of an agency.
Red teaming originated in the military to realistically evaluate the strength and quality of strategies. Since then, red teaming has become a common cybersecurity training exercise among public and private sector organizations. Other security testing methods include ethical hacking and penetration testing, or pen testing. While the red team shares the same goal and perspective of these strategies, their execution is often quite different.
Penetration testing vs. red teaming
Pen testing and red teaming are often used interchangeably to describe security testing techniques. Each uses an "outside" perspective but does so in a different way. Figure 2 compares the two activities.
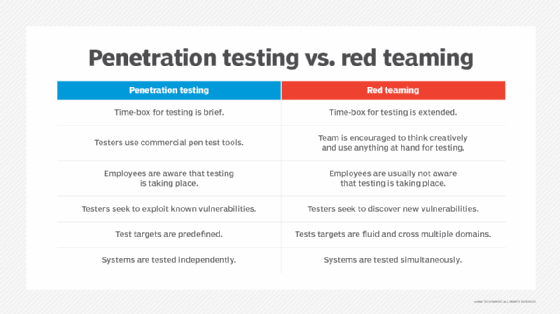
Penetration testing
Pen testing is a manual security testing method that organizations use to provide a comprehensive overview of the quality and effectiveness of their security controls. The goal is to test the vulnerability of networks, assets, hardware, platforms and applications within a defined scope. Often automated using special software tools, the attack simulation launches actions attempting to defeat the organization's security posture. Existing security measures are violated and an attack path is established. The test attempts to break through preventive measures and establish an attack surface red team operations can exploit.
Pen testing transcends a vulnerability assessment, an evaluation process used to rank cybersecurity weaknesses by importance and/or risk. Pen testing leverages ethical hackers to physically and virtually challenge the strength of security devices and procedures.
These tests are deliberate and meticulous, placing no focus on stealth or evasion. The goal is to gain access and bypass security controls by simulating real-world attacks. Pen testing lacks a competing blue team. The blue team is often informed of penetration test plan scope and depth.
Learn the necessary steps for network penetration testing.
Red teaming
Red teaming is a stealthy procedure used to test systems, protocols and the people managing them. Red teaming is a focused security testing method with specific objectives. If the objective is to access a sensitive server or a business-critical application, red team success is measured by how well it accomplishes this objective. If the red team achieves its goal, the organization is insufficiently prepared to prevent such an attack.
Outcomes from the pen test can indicate measures to take to resolve deficiencies in security controls.
The lack of notice distinguishes red teaming from pen testing. Blue teams are often purposely left in the dark during these evaluations. The goal is to force the blue team to respond as if it were an actual attack, providing a more accurate assessment.
Read more here about penetration testing vs. red teaming.
Red team methodology
Red teaming involves a tactical, deliberate process to extract all the desired information. An assessment that identifies entry points and vulnerabilities legitimate cybercriminals may want to exploit should precede a red team simulation. Doing the assessment prior to simulation ensures a controlled process and measurable outcome.
The assessment will help illuminate goals the red team wants to achieve. Any weakness associated with digital assets, physical assets, technical processes or operational processes could be targeted for exploitation in the red teaming session.
Once objectives are set, the red team will initiate an attack. Typically, the blue team will identify the red team activity as malicious and start to contain or limit the success of their efforts. Once the exercise ends, each party will provide findings that showcase the value of their perspective and the exercise itself.
The blue team will identify any indicators of compromise (IoC) they were able to detect. IoCs are flags that security teams use to register suspicious activity. Typically, security systems that protect networks and systems generate them. The red team will prepare a breakdown of its tactics, techniques and procedures (TTPs) for the blue team.
Together, the two teams use the results to create a list of actionable items -- such as firewall upgrades or server configurations -- they can perform to improve the current security system's detection and response activity. This sharing of information can often establish what's called a purple team, as shown in Figure 1 above.
Red team activities
Red team exercises that deal with cybersecurity might include a variety of activities that attempt to defeat cybersecurity controls, such as those listed in Figure 1. Examples include trying to bypass firewalls and intrusion detection and prevention systems (IDS/IPS), introducing viruses, conducting phishing and malware attacks and launching social engineering attacks.
While attacks typically address systems, applications, utilities and networking resources, they might also include an attack on a data center's physical security. This could occur by surreptitiously allowing red team members entry into data centers.
Social engineering attacks focus on psychological attributes of employees. Red team members must perform sufficient due diligence on employees (e.g., learning what they do and any particular habits that could be exploited) before launching the social engineering attack.
Much information can be gained by walking around office areas and observing employee behavior. Employees who leave their workstations without logging off create a risk of unauthorized access to their systems. In a potential red teaming simulation, employees could be called about a "problem" detected on their systems and convinced to have "IT" remotely activate a "fix."
Pros and cons of red teaming
The positive benefits of red teaming are numerous. Most importantly, they identify vulnerabilities in systems, policies, procedures and employees that could be exploited in cyberattacks. Knowledge of such vulnerabilities can be used to identify and deploy remediations to prevent future attacks.
Red teaming benefits grow when combined with blue teaming. Greater information sharing fosters collaboration, reveals areas where additional training is needed, and can encourage employees to improve their cybersecurity skills and reduce response times for future events.
Among the downsides of red teaming are the potential costs for an exercise. An exercise might not be feasible or succeed if senior management is not engaged or resources to execute it are insufficient.
Preparing for a red team exercise
As with any cybersecurity activity, senior management approval is the first step. Next is assembling the team and tools to be used. The actual attack objectives and scope should be defined, and conducting a pen test is an important preliminary step. It establishes baseline security data that can be used to formulate the exercise.
Once the exercise has been defined and resources assembled, the team decides when to launch the exercise. If a blue team has also been assembled, they should not be notified of the exercise date. Upon completion of the exercise, the teams should prepare a report of findings and recommendations. Data from cybersecurity software used in the exercise should be included. A post-exercise meeting provides an opportunity for all players to share their experiences and review recommendations.
The role of AI in the future of red teaming
Artificial intelligence is quickly permeating all aspects of IT, especially in cybersecurity. Use of AI capabilities can increase the likelihood of identifying potential attack vectors and facilitate better analysis of exercise results.
Red and blue teaming are expected to remain important and AI will enhance greatly the overall process and results from exercises, resulting in better early warnings and faster, more accurate responses to cyberattacks.
Learn about AI red teaming, which is the practice of simulating attack scenarios on an artificial intelligence application to identify weaknesses and plan preventative actions.
