recovery point objective (RPO)
What is recovery point objective?
The recovery point objective (RPO) is the age of files that must be recovered from backup storage for normal operations to resume if a computer, system or network goes down as a result of a hardware, program or communications failure. The RPO is expressed backward in time -- that is, into the past -- from the instant at which the failure occurs and can be specified in seconds, minutes, hours or days. It is an important consideration in a disaster recovery plan (DRP).
Once the RPO for a given computer, system or network has been defined, it determines the minimum frequency with which backups must be made. This, along with the recovery time objective (RTO), helps administrators choose optimal disaster recovery (DR) technologies and procedures.
For example, if the RPO is one hour, admins must schedule backups for at least once per hour. In this case, external, redundant hard drives may prove to be the best disaster recovery platform. If the RPO is five days (120 hours), then backups must happen at intervals of 120 hours or fewer. In that situation, tape or cloud storage may be adequate.
How does RPO work?
RPOs work by defining the duration of time that can pass before the volume of data loss exceeds what is allowed as part of a business continuity plan (BCP).
The amount of data loss an RPO allows is known as the enterprise loss tolerance. Depending on the organization and the workload, loss tolerance will vary, which affects what the associated RPO for that workload should be.
An RPO is enabled by setting the desired data backup frequency, such that there is always a backup available that fits within the duration of time the loss tolerance allows for. Admins can automatically configure an RPO as a policy setting inside of backup or storage software and cloud services.
How do you calculate RPO?
Calculating an RPO has several prerequisite steps.
At the most basic level, organizations first need to understand what data they have and where it exists. Understanding how frequently the different data changes as part of normal business operations is another foundational step. Companies must also assess what the value of the data actually is at a given point in time.
With the prerequisite steps in place, administrators will have the information needed to make a policy decision to determine what the RPO should be. So, after understanding how often data changes and what the value of it is, they can calculate RPO as a function of their organization's loss tolerance.
That is, how much data -- as measured by duration of time -- can their company afford to lose and still be able to recover for normal business operations.
Examples of RPOs
Businesses can choose to have any number of different tiers for an RPO based on workload and loss tolerance.
- Critical data (0-1 hours). For the most valuable data organizations can't afford to lose at all, such as banking transactions, the RPO needs to be set for continuous backup.
- Semicritical (1-4 hours). For data that is semicritical, which could include data on file servers or chat logs, an RPO of up to 4 hours should be set.
- Less critical (4-12 hours). Data such as marketing information is often deemed as less critical, for example, and can work with a longer loss tolerance with an RPO of up to 12 hours.
- Infrequent (13 - 24 hours). Infrequently updated data, such as product specifications, can have an RPO of up to 24 hours.
Experts recommend not implementing an RPO of more than 24 hours, as having a daily backup is a bare-minimum best practice for nearly all data at any time of day.
RPO in disaster recovery planning
A DRP is all about having a strategy in place to help recover necessary data and systems after a data loss event or natural disaster.
Unlike scheduled maintenance or downtime, a disaster event is unpredictable. This is why organizations need to have a DR strategy with a defined RPO and other objectives in place to help limit its impact. With an RPO, enterprises will have defined what the loss tolerance is for potential data loss, so instead of a disaster event being entirely unpredictable, organizations will know ahead of time what the maximum amount of data loss will be.
For example, take an RPO for critical data that an organization backed up at least every hour. This means that as part of a business continuity plan, it knows the worst-case scenario from a data loss event is the most data it will lose is one hour's worth.
Differences between RPO and RTO
Recovery point objective is closely related to recovery time objective, which is the maximum length of time computing resources and applications can be down after a failure or disaster. Together, the two approaches enable a BCP and a DR strategy.
Recovery point objective. The RPO determines loss tolerance and how much data can be lost. It is a planning objective that defines how often data needs to be backed up to enable recovery. An organization enables RPOs by having a DR approach in place that backs up data at the right intervals, so the amount of data loss never exceeds its determined loss tolerance.
Recovery time objective. The RTO comes into play after a loss event. It helps organizations answer the question of how quickly they can recover after data loss due to a failure, natural disaster or malfeasance.
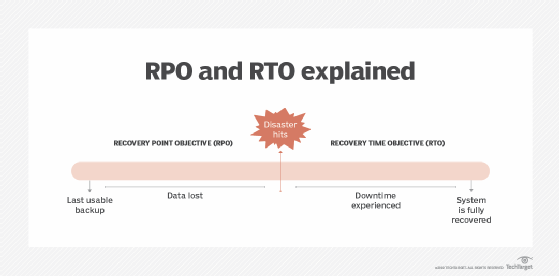
RPO and RTO work together in a time sequence, with RPO making sure a business has the right data backup policies in place and RTO ensuring it can recover data backups quickly.
