real-time monitoring
What is real-time monitoring?
Real-time monitoring is the delivery of continuously updated data about systems, processes or events. Such monitoring provides information streaming at zero or low latency, so there is minimal delay between data collection and analysis. It enables quick detection of anomalies, performance issues and critical events.
Real-time monitoring is a type of IT monitoring where data is collected from on-premises hardware, networks, security systems, virtualized environments and the application stack -- including those in the cloud -- and out to software user interfaces. From this data, IT staff analyze system performance, flag anomalies and resolve issues. It's a critical method of maintaining network security and ensuring good end-user experience and network performance.
Real-time monitoring ups the ante for data collection and decision-making by providing a continuous low-latency stream of relevant and current data from which administrators can immediately identify serious problems. Alerts can be more quickly routed to appropriate staff -- or even to automated systems -- for mitigation. By tracking real-time monitoring data over time, organizations can reveal and predict trends and performance.
How does real-time monitoring work?
Real-time monitoring relays the active and ongoing status of an IT environment. It can be tuned to focus on particular IT assets and set to look at a desired level of granularity.
Types of real-time data include the following:
- Central processing unit (CPU) and memory utilization.
- Application response time.
- Service availability.
- Network latency.
- Network security.
- Web server requests.
- Transaction times.
Once an infrastructure device is selected for monitoring, real-time monitoring begins collecting data and analyzing it as it's collected to generate insights and trigger alerts and notifications when anomalies are detected. Real-time monitoring software displays relevant data on customizable dashboards. Administrators choose the expected data ranges and formats as numerical line graphs, bar graphs, pie charts or percentages. The data displays can be arranged according to priorities and administrator preferences.
How can companies implement real-time monitoring?
Implementing real-time monitoring functionality requires careful planning, selection of appropriate tools and integration with existing systems. The following are key steps to consider when implementing real-time monitoring:
- Define monitoring goals. Companies should determine their objectives for implementing real-time monitoring. This involves selecting the key metrics, performance indicators and activities that need to be monitored. Key metrics can include application change time and deployment frequency. Companies should also assess their infrastructure and systems to identify the components, such as servers, network devices, applications and databases, that need monitoring. Different components require different types of monitoring, such as network performance monitoring, application monitoring and security monitoring.
- Choose the right tools. Selecting the right monitoring tools is crucial for success. Companies should evaluate the options based on factors such as scalability, flexibility, ease of use and compatibility with their existing infrastructure. Successful real-time monitoring tools support real-time data collection, offer customizable monitoring dashboards and alerts, and provide analytic capabilities.
- Set up monitoring infrastructure. Once the tools have been selected, companies should deploy monitoring agents or sensors across their network, servers and applications to collect data. This involves establishing secure connections between monitoring tools and devices being monitored and might include deployment of monitoring agents, sensors, probes, centralized monitoring servers and cloud-based monitoring platforms.
- Define key metrics. Companies should define the metrics that are critical for monitoring the performance, security and health of their managed systems. These metrics may include bandwidth use, latency, error states, server response time, CPU use and network traffic volume. Thresholds should also be established to trigger alerts when abnormal or critical conditions are detected.
- Configure alerts. Companies should configure alerts and notifications based on defined thresholds and priorities. This involves determining which relevant stakeholders should receive the alerts and establishing clear escalation procedures for addressing critical issues. Alerts should be actionable, concise and prompt, and they should provide enough real-time information to facilitate timely response and resolution. Alerts should be automated to reduce manual intervention.
- Integrate monitoring with other systems. To maximize a real-time monitoring system's effectiveness, it must be integrated with existing incident management systems, ticketing systems, and diagnostics and IT service management platforms. This can increase incident response processes. Application programming interfaces should also be used to exchange data among different systems and enable seamless information sharing.
- Perform data visualization. Dashboards and reporting systems should be set up to display monitoring data in a meaningful and easily understood format. Charts, graphs and other visual tools can help identify trends, patterns and anomalies.
- Define response procedures. Well-defined response procedures and escalation paths must be developed to address issues detected through real-time monitoring. Responsibilities should be assigned and protocols established for timely resolution and communication during critical events. These protocols and responsibilities must be secured to prevent escalation attacks.
- Regularly review and optimize. Companies should continuously monitor the effectiveness and efficiency of real-time monitoring, regularly reviewing monitoring parameters, alerting thresholds and response procedures to ensure they align with the changing needs. This requires training staff so they have the skills to interpret the data, make adjustments and incorporate feedback from users to refine the monitoring process.
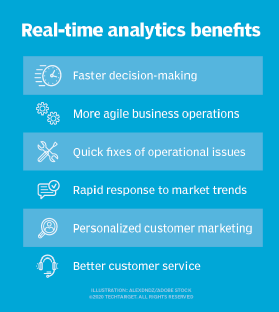
Benefits of real-time monitoring
The many advantages of real-time monitoring include the following:
- Faster decision-making and reaction time. Collecting real-time monitoring data helps IT managers quickly evaluate and react to IT events.
- Trends monitoring. Organizations can log and track real-time data over time to identify trends and better recognize abnormalities that fall outside set parameters of system and application behavior. This is known as trend monitoring.
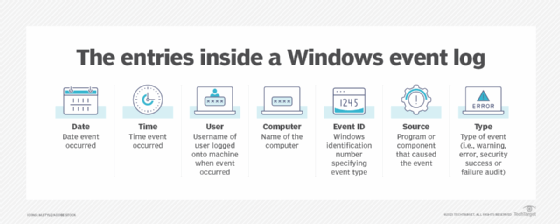
![Entries in event log]()
Real-time monitoring analyzes event logs, which include the date of an event and the computer ID associated. - Enhanced security. Real-time monitoring initiatives let businesses quickly detect and respond to security events. They can identify data security breaches, unauthorized access attempts and other suspicious behavior in real time by analyzing event log data, monitoring network traffic and using Simple Network Management Protocol (SNMP) agents.
- Improved network performance. Efficient network monitoring is critical to maximizing productivity and delivering a seamless user experience (UX). Real-time monitoring improves network performance through server and application monitoring and through UX monitoring. It also identifies bottlenecks, bandwidth issues and latency problems. By closely monitoring key performance indicators, businesses can proactively optimize their network architecture, allocate resources and streamline operations.
- Proactive incident response. Real-time monitoring lets businesses detect and respond to incidents before they happen. Real-time monitoring uses alerts, managed devices and the management information base to send relevant stakeholders instant notifications when performance metrics deviate from normal ranges. They can then address issues fast, minimize downtime and prevent potential disruptions before they impact end users. Server application monitoring tools play a crucial role in proactively monitoring and managing the performance of server and application environments.
- Increased employee productivity. Real-time monitoring enhances employee productivity. It ensures optimal network performance through monitoring tools and IP management that lets employees access critical applications, collaborate seamlessly and complete tasks efficiently. Monitoring also helps identify and address potential bottlenecks or other issues that could hinder productivity, such as slow-loading webpages and network congestion.
- Cost savings. Identifying and resolving performance issues promptly helps businesses optimize resource use, avoid unnecessary hardware upgrades and reduce maintenance costs. Real-time monitoring also enables preventative maintenance, letting businesses detect and address potential problems before they escalate into costly failures. Proactive incident response minimizes the financial effect of downtime, service disruptions and security breaches.
Examples of real-time monitoring
Monitoring is used in many industries and situations, particularly in IT and manufacturing, to enable quick reaction to momentary events. Examples of where it's used include the following:
- Server and data center management. Server and data center management can use real-time data to predict imminent equipment failures and maintenance. Additionally, using streaming telemetry instead of a version of SNMP to collect network data provides a more accurate picture of network performance.
- Software development. In software development and testing, synthetic and passive monitoring use real-time data to simulate user interactions with software, see what customers see and flag problems before the application is released to production.
- Contact centers. Contact centers can use real-time data to manage queue and staff, ensure queue uptime and report statistics about service.
- Sales. Sales agents can receive real-time alerts when customers are interested in high-value or high-margin items.
- Web store implementations. Web store implementations can collect and analyze streamed data to flag missed sales opportunities because of low inventory. They also use artificial intelligence (AI) to detect coupon fraud, where a customer uses a code multiple times against its terms.
- Fleet management. Fleet operations can use real-time data collection through vehicle Fleet management software to catch reckless, sleepy and impaired drivers, as well as maximize fleet use.
- Retail. Radio frequency ID tracking in retail can enable real-time updates on inventory and theft detection.
Real-time monitoring tools and vendors
Below are some real-time monitoring tools and providers:
- BMC Software TrueSight Capacity Optimization.
- Cisco AppDynamics.
- Datadog.
- Fortra Vityl Capacity Management.
- Nagios.
- New Relic.
- Quest Software.
- SolarWinds Server & Application Monitor.
- Splunk App for Infrastructure.
- VMware Capacity Planner.
Reactive monitoring vs. proactive monitoring
Reactive monitoring is an established troubleshooting method in IT organizations and data centers. The defining characteristic of this process is that it reacts to triggers that signal an event has occurred.
By comparison, proactive monitoring applies monitoring data without requiring a trigger event. In this approach, a monitoring tool can predict problems -- such as a memory leak -- that, if unresolved, could crash an application or an entire server. AI and machine learning are increasingly applied to proactive monitoring to comb through data, track cyclical patterns and flag abnormal behaviors. Some IT experts suggest combining reactive and proactive monitoring for optimal IT visibility.
Real-time monitoring is an effective way to detect security threats. Learn the top 10 types of information security threats for IT teams.