rainbow table
What is a rainbow table?
A rainbow table is a password hacking tool that uses a precomputed table of reversed password hashes to crack passwords in a database. Although rainbow tables provide security administrators with a method to test password security standards, they also provide hackers a way to quickly crack passwords and gain unauthorized access to computer systems.
Rainbow refers to the different colors used in the table to show the various hashing and reduction functions and steps. With each reduction function being a different color, the final plaintexts and hashes would look like a rainbow.
Passwords aren't typically saved as plain, readable text or plaintext. Instead, they are encrypted using hashes. Hash functions transform any given string of characters into another value. After a user enters a password, that password is converted into hashes. The result is compared with the stored hashes to look for a match. If the hashes match, then the user is authenticated.
Rainbow tables are a listing of the password hash values for each plaintext character used during authentication. Threat actors could either make a large list of hashes that correlate to common passwords or gain access to a list of password hashes. This means they can quickly infiltrate a system without knowing the original password.
Rainbow tables aren't as great of a threat as they used to be because of a process called salting. Salting adds an extra random value to hashed passwords, making the same hash a different hash value.
How do rainbow table attacks work?
Rainbow tables calculate the hash function of every string placed in the table. A rainbow table is constructed using chains of both hashing and reduction functions. Common plaintext passwords are repeatedly passed through a chain of these operations and then stored in the table next to their corresponding hash.
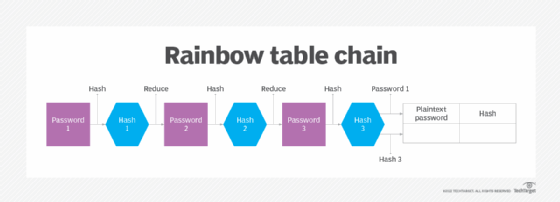
To crack a password, or for rainbow table attacks, large numbers of hashes are run through a dataset and then through multiple reduction stages to split them into smaller components that are linked to plaintext characters. The plaintext passwords are then stored in the table next to their hashes.
A password-cracking program then compares the rainbow table's list of potential hashes to hashed passwords in the database. If there's a match, the plaintext that produced the hash is retrieved and the process is stopped. With the correct hash, the threat actor can now successfully access the device -- they've cracked the authentication process.
Benefits and drawbacks of rainbow tables
Rainbow tables provide the following advantages:
- They make password cracking much faster than earlier methods, such as brute-force attacks and dictionary attacks.
- The process is simplified as a search-and-compare operation, as all of the values in a rainbow table should already be computed.
- The exact password doesn't need to be known. Authentication is possible as long as the hash matches.
Disadvantages of rainbow tables include the following:
- They require a large amount of storage to make the attack completable in a realistic amount of time.
- If the hash the attacker is trying to break isn't in the table, the attack becomes much less viable.
- Rainbow attacks are much less common due to the use of modern cryptographic hash functions, namely salted passwords.
Protecting against rainbow table attacks
To protect against attacks using rainbow tables, systems administrators should add these security measures:
- Salting.This technique adds a random string of characters to passwords before encrypting them. Rainbow table attacks work under the assumption that a text string has one specific hash value; the extra generated characters change that expected hash value.
- Biometric authentication. Rainbow table attacks don't work against biometric passwords, which verify a user's identity. They can't be typed like a password and are unique to that individual.
- Key stretching. In this method, the password, salt and an intermediate hash value are run through a hash function multiple times to increase the computation time for the attack.
- Server monitoring. Server security software is designed to detect an attack before any threat actors find a password database.
- Secure hash functions. Organizations should discontinue using outdated hashing algorithms such as the message-digest algorithm or Secure Hash Algorithm 1. Instead, they should consider using SHA-3, which is more secure.
Future of rainbow tables
Since the salting technique started being used, the prevalence and threat of rainbow table attacks have decreased dramatically. For example, Unix, Linux and Berkley Software Distribution use salted hashes. Even Apple Keychain, Apple's password management system in macOS, uses salt. Although Windows systems don't use salt, they can still encrypt stored hashes using the system key or Syskey utility. However, rainbow table attacks are possible on Windows for eight- and nine-character New Technology LAN Manager passwords
GPU-based brute force attacks have become more practical than rainbow table attacks. GPU brute-force attacks are similar to regular brute force attacks, but the graphics processing unit of a PC searches for passwords. Comparatively, rainbow table attacks are slower, less scalable and are specific to given password hash and password types.
Learn more about password security and its relation to character length.
