What is a proxy server? Definition and use cases
A proxy server is an intermediary between a user and the internet. It's a dedicated computer or software-driven service that acts as an intermediary or gateway between an endpoint or client device, such as a computer, and a server on the internet. The computer makes requests for resources and the server provides those resources. The proxy server facilitates user access to the requested services, such as web browsing, streaming media and file downloads.
The proxy server can exist on the same machine as a firewall server, or it can be on a separate server that forwards requests through the firewall.
An advantage of a proxy server is that its cache can serve all users. If one or more internet sites are frequently requested, these are likely to be in the proxy's cache, which improves user response time. A proxy can also log its interactions, which can be helpful for troubleshooting.
How proxy servers work
When a proxy server receives an internal network request for an internet resource such as a webpage, it looks in its local cache of previously accessed pages. If it finds the page, it returns it to the user's browser without forwarding the request to the internet. If the page isn't in the cache, the proxy server, acting as a client on behalf of the user, uses one of its own Internet Protocol (IP) addresses to request the page from the server on the internet. When the page is returned, the proxy server forwards it to the user.
Proxy servers are used for both legal and illegal purposes. In the enterprise, a proxy server facilitates security, administrative control and caching services, among other purposes. In personal computing, proxy servers enable user privacy and anonymous surfing. Proxy servers can also be used for nefarious purposes: to monitor traffic and undermine user privacy.
Proxy servers provide services such as filtering and firewall protection. They check the sender, recipient and other header information, along with the data payload or content of each packet traversing the proxy. They then apply rules and policies that govern information flow, encrypt data and hide the sender's IP address. These capabilities prevent users outside an organization from seeing a sender's IP address; they also stop hackers from getting unauthorized system access.
Proxy servers are invisible to users, and all internet requests and responses returned appear to be directly interacting with the addressed internet server. However, the proxy isn't actually invisible, as its IP address must be specified as a proxy configuration option to the browser or other protocol program.
How users can configure a proxy server
Users can access web proxies online or configure web browsers to constantly use a proxy server. Browser proxy settings include automatically detected and manual options for HTTP, Secure Sockets Layer (SSL), File Transfer Protocol, and Socket Secure, also known as Socks proxies.
Proxy servers can be shared and serve many users, or they can be dedicated to just one user per server. There are several reasons for proxies and many types of proxy servers, often in overlapping categories.
Operating systems (OSes) and devices, such as Microsoft Windows and macOS, have their own set of steps for configuring proxy servers. Users should review their proxy server provider's documentation or the official documentation of their OS for precise instructions.
For example, with Windows 10 and 11, a proxy server can be automatically set up using a script or it can be done manually. Windows users access proxy setups by selecting the start button, choosing settings, network and internet, and then proxy.
An automatic setup lets Windows detect the proxy server and arrange its settings without any user intervention. A script-based setup requires the user to find and execute a suitable script that implements the necessary settings to configure the proxy server. A manual setup requires the user to enter specific details of the proxy server, such as its server name, IP address and port number.
Benefits of a proxy server
Using a proxy server can provide advantages to organizations and individuals, such as the following:
- Improved network security. Proxy servers provide content filtering, serve as firewalls and web filters, and safeguard users from malware and other cyberattacks. They can also encrypt web requests, which adds an extra layer of protection for sensitive data.
- Efficient monitoring of internet use. Businesses and individuals can tap proxy servers to regulate and monitor internet use by restricting access to specific websites during work or study hours. Proxy servers track and log online requests, providing insight into user behavior, even in situations where website restrictions aren't fully enforced. This provides effective enforcement of cyberloafing rules that restrict employees from using work time for nonwork-related activities.
- Privacy and anonymity. By changing the user's IP address, proxy servers enable anonymous browsing, masking the user's location and identity. Anonymous browsing enhances privacy and anonymity when accessing the internet.
- Improved network performance. Proxy servers enhance LAN and Wi-Fi network performance by locally caching copies of popular websites. Caching speeds access to frequently visited sites, reduces bandwidth use and improves overall network performance.
- No regional restrictions or blocks. By using a proxy server to change their IP address, individuals can bypass geographical content restrictions. The masked IP address makes them appear as though they're accessing content from a region where access is permitted. This enables them to access websites, services and content that might otherwise be restricted based on their location.
Proxy server challenges and disadvantages
In spite of the proxy servers' benefits, they also present issues such as the following:
- Performance. The addition of a proxy server can add latency to network traffic. This can slow web browsing and other activities. These servers can also be bottlenecks when large numbers of users try to send traffic through one proxy server simultaneously.
- Security. Proxy servers typically enhance security by masking IP addresses. However, they also log activity, which can pose potential privacy concerns. In addition, the central nature of a proxy server makes it a common target for hackers seeking to intercept or manipulate traffic, especially if the data involved is unencrypted.
- Reliability. A proxy server also presents a potential single point of failure for a network. If the proxy server fails, every user or application relying on it will experience disruption.
- Complexity. Proxy servers can pose compatibility issues, such as a lack of support for certain network applications and protocols. They can also be complicated to set up and maintain, especially in large or complicated networks.
Types of proxy servers
Proxy servers come in various types, each serving specific purposes and offering distinct functionalities. The following are common proxy server types.
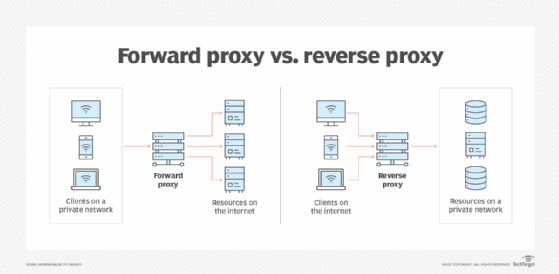
Forward proxies
Forward proxies send the client requests to a web server. To access forward proxies, users surf directly to a web proxy address or configure their internet settings to use a forward proxy. These let users circumvent firewalls and increase their privacy and security, but they can sometimes be used to download illegal content, such as copyrighted content and child sexual abuse material.
Reverse proxies
Reverse proxies transparently handle all requests for resources on destination servers without requiring any action from the requester or the origin server. Reverse proxies are used to do the following:
- Enable indirect access when a website disallows direct connections as a security measure.
- Enable load balancing between servers.
- Stream internal content to internet users.
- Disable access to a site; for example, when an internet service provider (ISP) or government wants to block a website.
Sites might be blocked for what they consider legitimate reasons; sometimes these reasons are considered justifiable, and sometimes they aren't. Reverse proxies can prevent access to news sites where users could view leaked information. They can also prevent users from accessing sites where they can disclose information about government or industry actions.
Transparent proxies
Transparent proxies are typically found near the exit of a corporate network. These proxies centralize network traffic. On corporate networks, a proxy server is associated with, or is part of, a gateway server that separates the network from external networks, typically the internet. Proxies are also associated with firewalls that protect the network from outside intrusion and let data be scanned for security purposes before delivery to a client on the network.
These proxies help with monitoring and administering network traffic, as the computers in a corporate network are usually safe devices that don't need anonymity for typically mundane tasks.
Anonymous proxies
Anonymous proxy servers hide the IP address of the client, enabling access to materials that are blocked by firewalls or circumventing proxy IP address bans. They are also used to enhance online privacy and protection from cyberattacks.
Highly anonymous proxies
Highly anonymous proxies, also known as high anonymity proxies, present a nonproxy public IP address. They hide even the fact that clients are using them and can enable access to sites that block proxy servers.
Socks 4 and 5 proxies
Socks 4 and 5 proxies provide proxy service for User Datagram Protocol data and Domain Name System (DNS) lookup operations in addition to web traffic. Some proxy servers offer both Socks protocols.
DNS proxies
DNS proxies forward DNS requests from local area networks to internet DNS servers while caching for enhanced speed.
Distorting proxies
A distorting proxy is a type of proxy server that masks the client's IP address by modifying the HTTP headers and presenting a fake IP address to the target server. This manipulation creates the impression that the user is from a different location, providing a layer of anonymity and privacy while limiting the ability to monitor the user's browsing activity.
HTTP proxies
Primarily used for web browsing, an HTTP proxy handles HTTP requests from web browsers and forwards them to web servers. It can also handle HTTPS requests in some cases.
Residential and data center proxies
Residential and data center proxies conceal the client's real IP addresses, with the primary distinction lying in their IP address sources. Data center proxies originate from data centers, whereas ISPs assign residential proxies.
Public proxies
A public proxy is a proxy service available to any user. It lets the user take advantage of the proxy server's benefits, such as anonymity and security, without the need to deploy and maintain a proxy server of their own. Public proxies might be available in a coffee shop or other public space where a Wi-Fi network is available. Public proxies are sometimes called shared proxies.
SSL proxy
An SSL proxy provides secure sockets layer decryption services between a client and server, keeping the proxy server hidden from both the client and server sides of the connection. This facilitates data encryption and a level of anonymity. However, content encrypted and transported through an SSL proxy can't be cached since there's no point in caching encrypted data, so proxy performance may be slightly reduced.
Proxy hacking
In proxy hacking, sometimes called proxy hijacking, an attacker attempts to steal hits from an authentic webpage in a search engine's index and search results pages. The proxy hacker has either a fraudulent site emulating the original or whatever they choose to show the clients requesting the page.
Proxy hacking encompasses a range of activities, including the following:
- Imitation website creation. The attacker creates a copy of the targeted webpage on a proxy server and uses methods such as keyword stuffing and linking to the copied page from external sites to artificially raise its search engine ranking. The authentic page will rank lower and can be seen as duplicated content, in which case a search engine can remove it from its index.
- Redirection and malware introduction. Proxy hacking can also be used to deliver pages with malicious intent. Proxy hacking can direct users to fake banking sites, for example, to steal account info that can then be sold or used to steal funds from the account. The attacker can also use the hack to direct users to a malware-infected site to compromise their machines for a variety of nefarious purposes.
- Search engine optimization hijacking and content scraping. SEO hijacking involves attempting to gain an advantage over competitors or redirecting traffic to fraudulent websites for advertising revenue. It's also known as content scraping, web scraping or page hijacking.
- Application-level hijacking. In this type of proxy hacking, users exploit vulnerabilities in web applications that don't use SSL to encrypt data. Traffic is modified, and information is sent to a trusted application, pretending the traffic came from a legitimate user.
Some means have been developed to compromise proxy abilities. Specially crafted Adobe Flash and Java apps, JavaScript, ActiveX and other browser plugins can be used to reveal a proxy user's identity, so proxies shouldn't be used on untrusted sites or anywhere that anonymity is important.
Website owners who suspect they've been the victim of a proxy hack can search for a phrase that would uniquely identify the site. The legitimate site should be prominent on the search engine results page. If a second site with the same content shows up, it might be a proxy page.
Proxy server security
Proxy servers in many forms enhance security, but they can also be vulnerable themselves. To prevent denial-of-service (DoS) attacks and network intrusion, administrators should take the following steps:
- Keep software up to date. Software updates often include patches that address security vulnerabilities discovered in previous versions. By regularly updating the proxy server software, administrators mitigate the risk of malicious actors exploiting known vulnerabilities. Updates also introduce new security features and improvements to existing security mechanisms. These enhancements strengthen the proxy server's defenses against evolving threats, such as malware, phishing attacks and unauthorized access attempts.
- Use load balancing. Load balancing distributes incoming traffic across multiple proxy servers. For example, if one server becomes unavailable due to a security incident or overload, the load balancer redirects traffic to other servers. This mitigates the potential for single points of failure by the proxy server, ensures continuous availability and minimizes the effects of potential attacks or failures.
- Enforce secure authorization and authentication. Secure authorization and authentication measures ensure that only authorized users and devices can access the proxy server. For example, the server verifies a user's identity before granting access by requiring them to authenticate with strong credentials such as passwords, biometrics or two-factor authentication.
- Block unsolicited traffic and audit proxy activities. Blocking unsolicited proxy traffic and regularly monitoring and auditing proxy activities helps detect and prevent security breaches, such as DoS attacks, malware and phishing attempts. This lets administrators promptly identify unusual traffic patterns, unauthorized access attempts and other suspicious activities. Blocking features are often related to firewall capabilities typically included with proxy server platforms.
- Define and enforce access policies. Defining and enforcing access policies that dictate which websites or services users can access through the proxy server can minimize the risk of malicious activities. These policies restrict user access to only authorized websites and services, reducing exposure to malicious content and unauthorized activities. By controlling access, organizations can prevent data exfiltration attempts and ensure compliance with regulatory standards.
- Disable or remove unnecessary services, ports or features. By eliminating or disabling unused functionalities, administrators minimize the number of potential entry points that attackers could exploit. This proactive approach reduces the attack surface and the complexity of the server environment, making it easier to manage and secure. It also decreases the likelihood of vulnerabilities in unused services or ports that could be targeted for unauthorized access or exploitation.
- Set up a backup strategy. Having a backup strategy for critical proxy server configurations and data ensures quick recovery in case of a security incident or hardware failure. It also helps protect against certain cyberextortion attempts, such as ransomware attacks. For example, ransomware attacks can encrypt or delete data, including proxy server configurations and logs. Having offline backups stored securely ensures organizations can recover their systems without paying ransom demands, thereby mitigating financial risks associated with cyberextortion.
Proxy server vs. VPN
The choice between a proxy server and a virtual private network depends on the specific security and privacy needs of the user or organization. The main differences between a VPN and a proxy server include the following.
Proxy server
A proxy server is best used when accessing content with geographic or geopolitical restrictions, when protecting IP addresses for single applications or when complete privacy isn't a principal consideration. The following are some considerations when using a proxy server:
- Proxy servers function as agents between a user and a server that's usually on the internet. While they hide the user's IP address from the web server being accessed, proxy servers don't secure the data being sent and received.
- Proxy servers don't natively encrypt data, so a user's online activities aren't fully protected when using a proxy server. Encryption can be implemented as a feature on a proxy server, however.
- The scope of protection of a proxy server is typically limited because it only functions with a single app or service.
- Free proxy connections can be slower and less secure because of fewer configuration options and reduced infrastructure.
VPN server
A VPN is best used when protecting all sensitive data exchanged with the network, when accessing content with geographic or geopolitical restrictions, or when a high level of privacy is appropriate for online work. The following are some considerations for when to use these servers:
- A VPN server natively encrypts and routes all internet traffic through a remote server. This provides a high level of security and privacy for users' online activities.
- VPNs also hide the user's IP address, but they go further and protect privacy by redirecting internet data through an encrypted tunnel.
- VPNs offer comprehensive protection by securing all internet traffic, not just specific apps or services.
- While both VPNs and proxy servers can slow browsing, VPNs are generally considered the faster option, especially when compared with free proxy connections.
Forward and reverse proxies secure and isolate private network resources, each serving distinct roles in modern enterprise architectures. Understand their differences for effective deployment and management.