
security incident
What is a security incident?
A security incident is an event that could indicate that an organization's systems or data have been compromised or that security measures put in place to protect them have failed.
In IT, an event is anything that has significance for system hardware or software and an incident is an event that disrupts normal operations. Security events are usually distinguished by the degree of severity and the associated potential risk to the organization.
If a single user is denied access to a requested service, for example, that can be considered a security event because it might indicate a compromised system. But the access failure could also be caused by many other things. The common theme for most security events, no matter what caused them, is that they don't typically have a severe impact on the organization. However, if large numbers of users are denied access, it likely indicates a more serious problem, such as a distributed denial-of-service (DDoS) attack, so that event can be classified as a security incident because of its disruptive impact on operations. One useful illustration for differentiating between a security event and a security incident is an unsecured door. Leaving the door unlocked is the security event and any subsequent robbery arising from the unlocked door represents the security incident.
What's the difference between a security incident and a security breach?
There's often confusion about the meaning of a security incident versus a security breach. A security incident covers a wide variety of security violations -- from computer systems, network and data access violations to malware, DDoS attacks or even the theft of physical computer equipment and devices with sensitive data.
On the other hand, a security breach pertains to data breaches only -- not network or system access violations or malware invasions where data isn't involved. In this respect, the security breach is a subcategory of a security incident that specifically relates to unauthorized access or theft of data only. This data breach could involve the alteration and outright theft of sensitive company data such as intellectual property or customer lists. It can also involve the unauthorized access, alteration and theft of the personally identifiable information (PII) of customers, clients, patients or others that violates these individuals' privacy rights.
Examples of security incidents include the following:
- Attempts from unauthorized users and sources to access systems or data.
- Unplanned disruption to a service or denial of service.
- Unauthorized processing or storage of data.
- Unauthorized changes to system hardware, firmware or software.
- Insider breaches of networks, systems or information instigated by employees or contractors, including malicious attacks on systems and networks.
- A malware infection such as ransomware or a virus that compromises networks, systems or workstations or performs unauthorized actions.
- An outside cybersecurity incident that's intended to disrupt, disable, destroy or maliciously control an organization's entire computing environment or infrastructure.
- An attack designed to destroy or steal data.
- Loss or theft of computer equipment.
Examples of security breaches include the following:
- Unauthorized access to privileged and personal data.
- Stealing a computer device that contains sensitive data or PII.
- Stealing physical documents that contain sensitive or personal data.
- Data penetration that results in data corruption or destruction.
- A ransomware attack that steals data and then demands a ransom for its return.
- Access to company customer data through a third-party data broker without company or customer consent.
Common types of security incidents
Security incidents cover a wide spectrum of security threats and breaches that businesses can face. Common security incidents include the following:
- Unauthorized access attacks. These cybersecurity incidents involve unauthorized attempts by cybercriminals to access systems or data using authorized user accounts. These attempts can be made through brute-force attacks, phishing attacks or other password exploits to steal sensitive information.
- Malware infections. Malware refers to malicious software that can infect systems and jeopardize their security. Malware incidents involve the infiltration of systems by viruses, worms, ransomware or other types of malicious software.
- Privilege escalation. Privilege escalation attacks occur when an attacker seeks unauthorized access to an organization's network and aims to acquire additional privileges through a privilege escalation exploit. A successful exploit grants the attacker privileges beyond those of normal users. Typically, this attack occurs after the hacker has already compromised the organization's endpoint network security by gaining unauthorized access to a lower-level user account.
- Denial-of-service attacks. DoS attacks are designed to flood a system or network with an excessive amount of traffic so that it becomes unusable for authorized users.
- Phishing attacks. This is a type of social engineering attack in which the perpetrator impersonates a trusted entity via email to share malicious code or links, aiming to extract login credentials or account details from victims. More sophisticated variations, known as spear phishing attacks, involve the attacker investing additional time in researching the victim for a targeted and refined approach to information theft.
- Insider threats. These are various types of compromises arising from individuals within an organization, either intentionally or unintentionally, posing a security risk. For example, a disgruntled employee seeking retribution could carry out an insider attack.
- Security misconfigurations. Misconfigurations in systems, networks or applications can lead to security problems because they can produce vulnerabilities that hackers can take advantage of.
- Advanced persistent threats. An APT is a sophisticated and prolonged attack that involves discrete infiltration, persistent presence and targeted exploitation of systems or networks.
- Web application attacks. This event happens when a web application is used in an attack. Web application attacks involve exploiting code-level vulnerabilities and bypassing authentication mechanisms. A specific instance is a cross-site scripting attack, where an attacker injects data, such as a malicious script, into content from typically trusted websites.
How to respond to a security incident
Because security breaches are actually a subset of security incidents, the tools and techniques used to address them are similar. In all cases, the goal is to subdue or resolve the incident as quickly as possible.
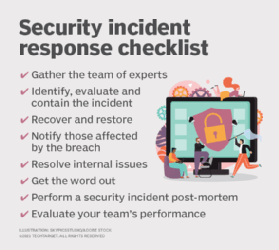
Organizations can use the following tools and techniques to respond to security incidents:
- Gather the team. Coordinate the team of security experts who will assess the severity of the incident, communicate with management and perform mitigation.
- Identify, evaluate and contain the incident. Identify what has been compromised. If a particular network is infected but other networks aren't, immediately isolate the affected systems and network to prevent the infection from spreading. At the same time, preserve all data in the infected network for later analysis.
- Recover and restore. If systems or networks are so severely affected that they can't be operated confidently, perform a full disaster recovery and failover.
- Notify those affected by the breach. If customer, client or patient data was compromised during the incident, notify persons affected of the breach and offer to pay for the mitigation services they might require.
- Resolve internal issues. If a malicious activity was perpetrated by a company employee, notify human resources so appropriate actions can be taken.
- Get the word out. Coordinate with corporate marketing and public relations for any messaging that needs to be made to the press or the public.
- Perform a security incident post-mortem. Once the security incident is resolved, review what happened, how it happened and what steps can be taken to avoid similar incidents in the future. Revise policies and practices to reflect any changes.
- Evaluate your team's performance. Security teams should determine how long it took to detect the incident, how long it took them to resolve the issue and provide remediation, and if there was anything they could have done better.
How to prevent a security incident
Methods and tools used to prevent security incidents include the following:
- Regularly train employees to ensure they're familiar with corporate security standards and practices.
- Using internal and outside IT auditors, regularly review IT security policies and practices to ensure they're current, including penetration and vulnerability testing of networks and systems.
- Ensure that security patches to hardware and software are promptly deployed.
- Monitor physical facilities, including secured access to data centers and to closets, file cabinets and other storage areas that might contain sensitive hardcopy documents.
- Monitor and log user and data activity at networks, system workstations and internet of things (IoT) devices. Use automated real-time alerts to detect potential threats and security violations.
- Vet vendors for conformance to corporate security and governance standards.
- Form agreements with business partners that restrict the sharing of confidential information with third parties without your company's express permission.
- Enforce strong access controls by limiting access to sensitive data and critical information to only authorized users.
- Promote the use of multifactor authentication among employees, as it requires users to provide an extra form of identification besides their username and password.
- Encrypt laptops and mobile devices and lock down any equipment that's lost or has been stolen in the field.
- Stay actively connected with security communities and attend conferences to stay up to date on the most recent security risks, trends and best practices.
Processes and tools designed to help with security incident management
A variety of commercial incident response tools and service providers are available to assist in the handling of security incidents. Examples of these tools include the following:
- Endpoint detection and response tools. EDR software analyzes endpoint devices such as laptops, desktops and mobile phones to detect security incidents at the periphery of the enterprise, which is helpful for securing IoT environments. CrowdStrike Falcon and Symantec Endpoint Detection and Response are examples of EDR tools.
- Security information and event management tools. SIEM tools gather and analyze log data from multiple sources, including network devices, servers and applications. They create warnings for possible security incidents, correlate events and identify patterns. IBM Security QRadar, McAfee SIEM and SolarWinds Security Event Manager are examples.
- Incident response software. Incident response planning templates assist in developing and mapping an enterprisewide security incident response plan. Providers of incident response planning templates include BlueVoyant and Exabeam.
- Security orchestration, automation and response tools. SOAR tools automate incident response by integrating with security tools, orchestrating workflows and handling repetitive tasks, leading to a faster and more efficient response. Examples include Palo Alto Networks Cortex XSOAR, Splunk Phantom and Swimlane.
- Unified threat management tools. UTM products offer a full set of security features, such as a firewall, antivirus, intrusion detection and prevention, virtual private network support and threat intelligence. They help businesses manage different security functions from a single platform. Examples of UTM tools include Check Point Next Generation Firewall, Cisco Meraki and WatchGuard Network Security.
- Security training software. Security training software helps employees learn the basics of effective security practices. However, it doesn't replace the in-house security training that should be part of every new employee orientation and annual security refresher courses for current employees. Examples of security awareness training providers and platforms include Infosec IQ from Infosec Institute, Proofpoint Security Awareness Training and SANS Institute.
As cyberattacks become increasingly diverse, staying ahead of the curve is important. Delve into 10 types of security incidents and discover effective risk management strategies.