air gap (air gapping)
What is an air gap?
An air gap is a security measure that involves isolating a computer or network and preventing it from establishing an external connection. An air-gapped computer is physically segregated and incapable of connecting wirelessly or physically with other computers or network devices.
Air gaps protect critical computer systems or data from potential attacks ranging from malware and ransomware to keyloggers or other attacks from malicious actors.
To transfer data between a computer or network and an air-gapped system, data is copied to a removable media device such as a USB drive and is physically carried by the user to the other system. In systems where security is paramount, the air-gapped system should have restricted access so only a few trusted users can access the system and deliver the data. The principle of least privilege limits users' access rights, which can also help decrease the chances of a cyber attack.
Air-gapped systems are still susceptible to electromagnetic leakage, which are waveforms emitted from the computing devices or wires that a hacker can analyze and use to attack the system. To prevent electromagnetic exploits, there's usually a specified amount of space between the air-gapped system and the outside walls, as well as space between its wires and the wires of other technical equipment. For a system with extremely sensitive data, an organization can use a Faraday cage to prevent electromagnetic radiation from escaping from the air-gapped equipment.
Although these measures may seem extreme, a threat actor could still intercept keystrokes or screen images from demodulated electromagnetic radiation waves from some distance away using special equipment.
Another way to protect a computing device or network from an air-gap attack is through end-user security awareness training. The infamous Stuxnet worm, which was designed to attack air-gapped industrial control systems, is thought to have been introduced by infected thumb drives found by employees or obtained as free giveaways.
Why are air gaps used?
Air-gapped networks are used to protect many types of critical systems from hackers or other malicious threat actors. For example, air-gapped networks are used to support the stock market, the military, government agencies and industrial power industries.
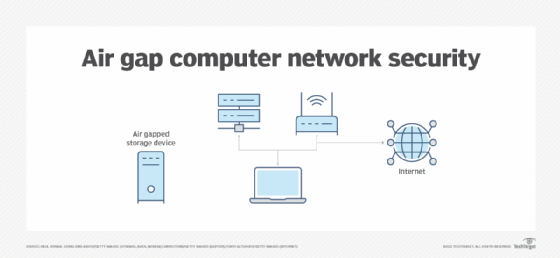
Air gaps are also used for backup and recovery. When data backups are air gapped, the security measure can aid in recovery efforts. For example, if an organization uses air gapping as part of its backup strategy and its network is hit by a ransomware attack, the air-gapped copy of data can be used for recovery.
Types of air gaps
There are generally three types of air gaps: total physical air gaps, air-gapped systems isolated within one environment and logical air gaps.
- Total physical air gaps are air-gapped systems in which hardware or software is physically isolated in its own environment. This type of air gap separates a system completely from other network-connected systems and may also have restricted physical access.
- Isolated air-gapped systems are separated from other systems in the same environment, perhaps even on the same rack, but aren't connected to the same network.
- Logical air gaps separate systems within the same network logically instead of physically. Logical separation methods can be completed using encryption and role-based access control, for example.
Some organizations may also have to handle two levels of information, which are separated into high and low sides. The high side is information or systems that require a highly secured environment -- such as critical infrastructure -- while the low side is data or systems that can be left connected to a network.
Air gap challenges
Although some organizations believe that air gapping is a viable security measure, air gaps are disappearing due to the following challenges:
- Manual updates. Air-gapped systems can't connect to the internet to update software automatically. Systems administrators must instead manually download and install new updates and patches. This requires more manual input, and if sys admins become too relaxed on updates, then the software on their air-gapped systems will become out of date, leaving the system unprotected from emerging virus threats.
- Human error and insider attacks. Sending data to an air-gapped system traditionally requires the use of a portable storage device like a USB. If brought on premises, infected USB devices could be used to leak data from an air-gapped system. Additionally, users could accidentally leave doors unlocked or USB ports unguarded.
- Electromagnetic attack. Air-gapped systems are susceptible to electromagnetic leakage, which enables malicious actors to analyze waveforms emitted from the CPU, chassis fans or wires with the goal of attacking the system.
- Supply chain attacks. A virus could be installed in updated software that gets passed along to air-gapped systems.
In 2018, the U.S. accused Russia of infecting air-gapped systems for electrical grid operations. Another instance where an attack jumped the air gap is when the Kudankulam Nuclear Power Plant in Tamil Nadu, India, was hit by a cyber attack, even though it had air-gapped systems. Any data at rest inside an air-gapped system should be encrypted to help create stronger cybersecurity practices and reduce vulnerabilities.
Learn more about air gap backups and how they add a layer of protection to data.
