15 IAM interview questions to prep for your next career move
The job market for identity and access management positions is strong right now, but the competition could be tough. Use these 15 questions to guide your interview prep.
The job market for identity and access management professionals remains strong, but to ace the interview and get the job, you must be prepared for some tough IAM interview questions.
Some organizations are looking for IAM analysts to oversee day-to-day operations; others are in a building phase and need IAM engineers and IAM architects. But often the job description is one-size-fits-all in the list of job skills sought:
- Integrate enterprise and single sign-on (SSO) applications with multifactor authentication (MFA).
- Enhance authentication policies.
- Build role-based access control.
- Maintain auto-provisioning platforms.
- Develop IAM policies and procedures.
Information technology professionals who specialize in IAM have typically worked in IT for one to five years and have systems and network administration experience. They decide to advance their careers by becoming specialists in IAM, a business-critical subset of information security, and move up the ranks to become IAM administrators, IAM managers and, at large organizations, IAM directors.
"In the current identity and access management job market, there's a growing demand for experts in cloud-based IAM solutions, zero-trust architecture and privileged access management to maintain high levels of access controls as organizations leverage cloud solutions," said Henry Bagdasarian, founder and president of Identity Management Institute. "Knowledge of multifactor authentication, single sign-on and experience with compliance frameworks like GDPR is also highly valued. Additionally, proficiency in automation tools for IAM processes, knowledge of identity governance and hands-on experience with leading IAM platforms make candidates more competitive."
Still job opportunities for IAM professionals
Job growth for information security analysts is projected to rise 33% by 2033 -- compared to 12% for computer occupations -- an increase from 180,700 jobs in 2023, according to the U.S. Bureau of Labor Statistics. The median pay in May 2023 was $120,360, or $57.87 per hour.
IT recruiting firms paint a different picture, however. The cybersecurity industry is in its first recession. It can be hard to find full-time work. This trend has increased demand for plug-and-play contract workers and fractional employees who spend a percentage of their time on multiple projects. But there are still job opportunities for IAM professionals, particularly for IAM engineers and architects skilled in cloud-based systems and development.
"IAM roles are very technical and are amongst the most wanted skills in the cybersecurity industry," said Deidre Diamond, CEO and founder of CyberSN and Secure Diversity.
The "U.S. Cybersecurity Job Posting Data Report," released in 2024 by CyberSN tracked 16,640 job postings for IAM engineers from January 2023 to December 2023, up 10.82% over 2022. The midyear report, January 2024 to July 2024, showed 6,059 IAM engineer job postings.
Job candidates can expect a range of identity and access management interview questions. The IAM engineer interview questions might include hands-on technical assessments. The specific IAM questions will depend on the organization's size and structure, industry, data security, privacy requirements and whether it is a public company, private or in the government sector. The IAM interview questions are designed to evaluate technical, interpersonal and business skills. While it is important to accurately identify knowledge of IAM concepts, frameworks and tools, many interviewers will be more interested in skill levels and practical experience.
"When you only have half an hour to 45 minutes to tell your story, it is not necessarily about the tooling," said Joel Abraham, vice president and co-founder of Identify Security, an IT recruiting firm. "It is what kind of value you brought and what problems you solved."
Basic IAM questions and answers
Hiring managers want to determine whether a job candidate has working knowledge of basic technical concepts, including the frameworks and protocols IAM requires. The interview process involves establishing a base level of IAM knowledge and then digging deeper to find out the job applicant's level of experience.
Here are some questions to be prepared for.
1. What is the difference between authentication and authorization protocols?
An authentication protocol is a set of rules and processes to validate credentials to determine whether user identities (passwords, biometrics) and nonhuman identities (tokens, API keys) are who they claim to be. Authorization determines what authenticated users, systems and applications can or cannot access based on predetermined rules and policies.
2. Can you provide examples of authentication and authorization use cases and when you might use one versus the other?
OAuth is an open standard for secure authorization that uses Secure Sockets Layer/Transport Layer Security, commonly known as SSL/TLS. OAuth authorization and OpenID Connect authentication are used by cloud providers, such as Amazon, Microsoft and Google, to enable third-party applications to connect to user data without having to share login credentials. This approach offers security by not sharing users' password data, but it lacks encryption.
SAML, or Security Assertion Markup Language, enables users to access multiple SaaS applications with one set of credentials for single sign-on. It works by passing authentication information between an identity provider and the service provider.
3. What is the principle of least privilege?
The principle of least privilege refers to a security approach in which users are granted the minimum privileges required to perform their job tasks. This strategy protects the company's assets and can help thwart insider threats.
4. What is the difference between role-based access control and attribute-based access control?
Role-based access control (RBAC) gives a user access to accounts and systems based on their roles within the organization. IT teams assign users to one or more groups and then grant permissions and access levels based on the roles (responsibilities) instead of to users individually. Attribute-based access control (ABAC) is a security method that dynamically evaluates attributes, such as a user's location, time and device, before granting context-based access to a resource.
5. What is identity federation? How does it facilitate access management across different systems?
The advantage of identity federation, such as Microsoft's Active Directory Federation Service infrastructure in the Windows domain, is that it enables users to use single sign-on of their Active Directory credentials to access network resources, along with other trusted services such as a cloud network and SaaS. One potential drawback of identity federation is that if there's a security breach, users could lose access to their data in multiple applications.
6. What kinds of tools and technologies are used in an identity management product?
Identity management tools and technologies help organizations verify user identities and control access to resources across on-premises networks and cloud-based services. Be sure you're familiar with the following:
- Authentication tools, such as username and password, biometrics (fingerprint, facial recognition), one-time passwords and security questions.
- Authorization protocols, such as RBAC, ABAC and policy-based access control.
- Provisioning and deprovisioning methods, including user account creation and management, access rights assignment and removal, and lifecycle management of user identities.
- Directory services, such as Microsoft Active Directory and Lightweight Directory Access Protocol.
- SSO.
- MFA.
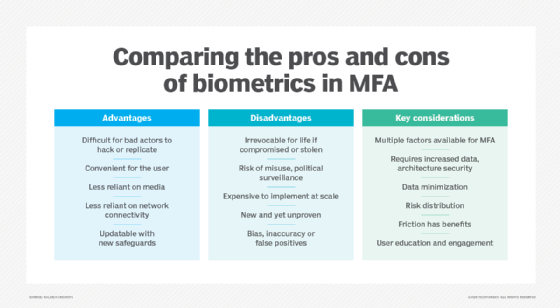
7. What is your experience with Amazon IAM, Microsoft Azure AD and Google Cloud IAM?
Entry-level job candidates should be prepared to explain the differences between Amazon Web Services, Microsoft Azure and the Google Cloud Platform -- and know the best use cases for each cloud provider.
All these cloud providers offer free trial periods to learn and test the technologies. If the job listing does not refer to a particular provider, focus on AWS IAM, which has the highest market value. The Identity Management Institute also advises you make sure you can discuss the differences between Amazon Elastic Compute Cloud and Amazon Simple Storage Service -- commonly referred to as Amazon EC2 and Amazon S3, respectively.
8. Can you walk me through the steps of a security incident related to IAM?
Here's a potential answer: A security alert from Amazon indicated irregular activity or unauthorized access of an AWS account using compromised or stolen administrator login credentials. The IAM team reviewed S3 bucket logs and AWS CloudTrail to determine if any unsanctioned activities took place. They rotated and deleted the exposed account's access keys after checking the application. In addition to implementing MFA, the IAM team worked with the cloud security team to mandate employee training on phishing campaigns and social engineering. The team also ensured all cloud data is encrypted at rest and in transit.
Advanced IAM interview questions and answers
Leadership positions often require a master's degree in computer science or a related field plus professional certifications, such as Certified Information Systems Security Professional, Certified Information Security Manager, Certified Identity and Access Manager and Certified Identity Professional. Large organizations might employ an IAM director; according to the Identity Management Institute, this is a leadership role responsible for designing, implementing and maintaining IAM systems and procedures that address the needs of 10,000 or more users. As more companies undergo digital transformations, success in these roles is measured by not only technical but also business outcomes.
Candidates for advanced IAM jobs should be prepared for questions like those following, with answers based on their knowledge and experience.
9. How do you balance IAM requirements with business needs?
Hiring managers want to ensure you can communicate the business value of IAM requirements and collaborate with other internal leaders to help the company pursue strategic IAM initiatives that strengthen the organization's security posture.
People in leadership positions often communicate with internal auditors, legal staff, privacy officers, human resources, contractors and regulators to achieve IAM goals and objectives. It's important to show that you can talk about the value of IAM in nontechnical terms so executives and staff can understand its importance to the security, risk management and business goals of the organization.
10. What are best practices for identity and access management in cloud infrastructures?
A question about cloud IAM presents an opportunity to emphasize the importance of IAM program management and the need to bring in multiple people from across departments so product selection and other areas do not hit roadblocks.
Discuss your experience with MFA, federated identities -- which enable SSO across multiple domains -- just-in-time access and other work that involved cloud service providers and third-party vendors. Planning the architecture before building cloud IAM is critical. While some companies have a dedicated cloud architecture team that reports to IT or security and is responsible for cloud IAM, other organizations rely on the same team that is responsible for their on-premises IAM infrastructure or even development or DevOps teams. The cloud is software. As such, IAM job applicants should have familiarity with scripting languages and best practices for REST APIs.
11. How do you handle governance and review of cloud infrastructure access?
A cloud governance framework can use many of the organization's existing policies, procedures and controls for data security, system integration, operational and cost efficiencies, and compliance. A framework can also help control cloud service use in the organization.
What most executives want to know is this: How can you tell who is accessing what in AWS, Azure and other cloud providers?
12. How do you ensure compliance with data protection?
In addition to managing IAM teams, IAM leaders work with chief information security officers to develop and enforce IAM policies, standards (e.g., NIST and ISO 27001) and procedures to ensure compliance with best practices and industry regulations, such as GDPR, CCPA, HIPAA, the Gramm-Leach Bliley Act, Payment Card Industry Data Security Standard and the Sarbanes-Oxley Act. They conduct ongoing audits and security assessments to identify vulnerabilities in existing infrastructure and access controls. They are also responsible for identity governance administration and identity lifecycle management.
These senior-level IAM positions are cross-discipline and involved in privacy, cloud and training initiatives. IAM policies, procedures and standards can help organizations meet compliance requirements, protecting personally identifiable information and health data. Other steps to ensure compliance include user identity management, strong authentication, access controls, data encryption, audits, management of third-party vendors and an incident response plan.
13. How do you use analytics to monitor access control processes and improve IAM policies and procedures to better support business initiatives?
Identity analytics and intelligence is an emerging area in IAM. These tools and techniques combine machine learning, AI and data analytics to identify inadequate IAM processes. Identity analytics might also offer insights into how to fix problems, such as removing redundant roles, entitlements or overprivileged accounts.
14: What is zero-trust architecture?
Zero-trust architecture is a security approach based on authentication inside and outside of the corporate networks -- essentially, a "never trust, always verify" model that assumes an attacker is already in the network.
Job candidates for government clients need to be well versed in zero-trust principles and frameworks. These architectures use microsegmentation and continuous risk-based authentication.
Some job listings will specify "zero-trust IAM specialist." Such positions require an ability to interact with engineering teams and understand the dependencies of critical processes and users' roles within them.
15. Why is privileged access management a priority for organizations?
Privileged access management (PAM) involves tools and strategies to support authentication, permissions and auditing procedures to regulate access to privileged accounts, such as administrative controls and higher levels of privileges for users, systems and applications. PAM software can help to centralize and automate management of privileged accounts. Because of its core security requirements, PAM is recommended -- and sometimes mandatory -- for cyber insurance.
Job hunting is never easy. It helps if you come prepared for questions like those above, ready to discuss what you've accomplished in past projects. But also come armed with your own good questions, such as asking about the company's security posture.
"A lot of people get lost in the interview, and they don't ask any questions about what they are walking into," said Abraham. "They say, 'I use this technology, and this is what I've done and this is how I've done it.' Instead of talking about, 'Hey, I helped streamline the user experience.'"
IT professionals hoping to advance their careers should study the interview questions on IAM and prepare to tell their story with real-world examples. The scenario-based interview approach demonstrates hands-on knowledge of IAM tools and technologies as well as an understanding of common threats and vulnerabilities, analytical thinking and problem-solving skills, and incident response strategies.
Kathleen Richards is a freelance journalist and industry veteran. She's a former features editor for TechTarget's Information Security magazine.








