
Getty Images/iStockphoto
Working with the Microsoft Defender for Identity portal
The security product, formerly Azure Advanced Threat Protection, taps into the cloud to uncover suspicious activity across the on-premises network.
On-premises environments can get an added security boost from the cloud to detect improper activities on the network.
Microsoft Defender for Identity, formerly Azure Advanced Threat Protection, is a cloud-based security platform that detects compromised identities and uncovers threats and ongoing attacks directed at the on-premises Active Directory. Microsoft Defender for Identity monitors user behavior and activities and using learning-based analytics. Through the Microsoft Defender for Identity portal, organizations can identify and investigate suspicious user activities and advanced attacks.
Understanding the Microsoft Defender for Identity architecture
Microsoft Defender for Identity watches network adapters on the domain controllers. It captures and parses network traffic, then combines this with Windows events directly from the domain controllers. Microsoft Defender for Identity analyzes retrieved events and data for attacks and threats. Microsoft Defender for Identity learns about the network by utilizing profiling, deterministic detection, machine learning and behavioral algorithms. The combination of features detects anomalies and warns of suspicious activities.
The core components of the system are the Defender for Identity portal, Defender for Identity sensor and Defender for Identity cloud service.
What is the Defender for Identity portal?
The portal displays data received from the sensors and performs the monitoring, managing and investigating of threats in the network environment.
The Defender for Identity Portal has five core capabilities:
- creates the Defender for Identity instance;
- configures the integration with other Microsoft security services;
- manages sensor configuration;
- displays data received from the sensors; and
- monitors suspicious activities and possible attacks based on the attack kill chain model.
Defender for Identity sensor
The Defender for Identity sensors install on either the domain controllers or servers running Active Directory Federated Services (ADFS). With the sensor installed on a domain controller, there is no need for a dedicated server or port mirroring configuration. If installed on an ADFS server, the sensor monitors network traffic and authentication events directly.
The Defender for Identity sensor has the following core functionality:
- captures and inspects domain controller network traffic;
- retrieves Windows events from domain controllers;
- receives RADIUS accounting information from any VPN providers;
- retrieves data about entities such as users and computers from the Active Directory domain;
- performs network resolution of entities; and
- transfers data to the Defender for Identity cloud service.
Defender for Identity cloud service
The Defender for Identity cloud service, available within the U.S., Europe and Asia, runs on Azure infrastructure. Defender for Identity cloud service also connects directly to Microsoft's Intelligent Security Graph.
Prerequisites for Microsoft Defender for Identity
As with all Microsoft 365 and Azure services, the first prerequisite is valid licensing. To use Defender for Identity, organizations must purchase Enterprise Mobility + Security (EMS) E5 or A5; Microsoft 365 E5, A5 or G5; Microsoft E5, A5 or G5 Security; or the standalone Defender for Identity license.
The domain controllers require internet access to the Defender for Identity cloud service; there is also support for proxy servers. The Defender for Identity configuration requires either a standard Active Directory user account or a group managed service account. A standard AD user account is the only option for servers that run Windows Server 2008 R2 SP1; both account types will work for Windows Server 2012 or higher.
Specific details about operating systems, ports, protocols and network adapters are available within the Microsoft documentation.
Accessing the Defender for Identity portal requires a license and an account designated as a global administrator or security administrator.
Create the Microsoft Defender for Identity instance
To use this service, the first task is to create the Defender for Identity instance within the portal at the portal.atp.azure.com URL. You must provide credentials using either the standard AD user account or group managed service account, and then you can download the required sensor software.
The Defender for Identity instance is named with the Azure Active Directory fully qualified domain name and created in the data center located closest to your Azure Active Directory.
After creating the instance, click the provided link to download the sensor setup. Copy the access key required to connect the sensor to the instance. Run the installation on the ADFS server or domain controller. The sensor status, name, version and health should then show in the Microsoft Defender for Identity portal.
The URL for the portal will update to the name of the instance. For example, if the instance name is training, then the new link is training.atp.azure.com rather than the default URL of portal.atp.azure.com. However, both URLs will work, with the original URL doing a redirect after logon.
How to work with alerts
Microsoft Defender for Identity security alerts uses simple language and graphics to show suspicious activities in the organization's network. It also identifies the actors (users) and computers involved in the threats. The service color codes alerts to make it easier to filter visually and organize by threat phase.
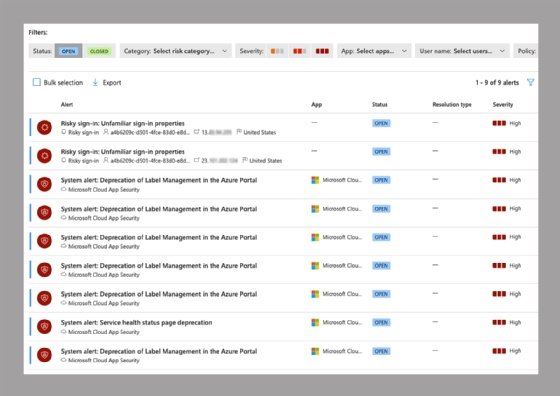
A security alert contains the title, description, any evidence and an export option. The alerts notify security teams of potential issues that might merit deeper investigation using either the Defender for Identity portal or the Cloud App Security portal.
After an investigation, each alert requires categorization in one of three classifications:
- true positive, meaning Defender detects malicious activity;
- benign true positive, meaning Defender found material evidence that was not malicious, such as activity from an approved application or a penetration test; or
- false positive, meaning a false alarm.
Other alert categories include reconnaissance, compromised credentials, lateral movement, domain dominance and exfiltration. Each alert type allows for deeper investigation and review of the performed action.
Clicking into the alert displays details such as the device name, username, status of auto-investigation and verbose alert details. The alert also displays a hierarchical representation of all processes related to the alert.
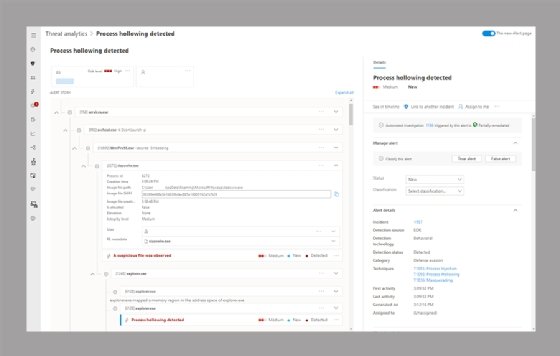
Additional protections when integrating with Defender for Endpoint
Defender for Identity monitors network traffic for account attacks and detects multiple suspicious activities, focusing on areas of reconnaissance, lateral movement cycle and persistence. Defender for Endpoint uncovers sophisticated cyber attacks by comparing alerts for known and unknown adversaries.
While Defender for Identity monitors the traffic on domain controllers, Defender for Endpoint checks the endpoints connected to the network. The Microsoft Defender for Identity portal's configuration section gives the option to integrate the two products for a single interface to check alerts.





