
Getty Images
Find and fix server problems with Best Practices Analyzer
Admins need all the help they can get, and this Microsoft utility shows IT how to correct security issues and optimize performance in key infrastructure workloads.
Maintaining the health and security of your Windows Server environment requires technical expertise, which Microsoft helpfully bottles up in one of its native tools.
Microsoft offers a range of utilities and resources to assist IT workers in their efforts to follow recommended guidelines and best practices for configuring and securing their systems. These tools also give insights into the state of the environment, identifying potential issues, risks and vulnerabilities. These utilities also help admins optimize the performance, reliability and availability of their systems. One of the most useful tools that covers all these areas is Best Practices Analyzer (BPA).
What is Microsoft Best Practices Analyzer?
Microsoft integrates BPA in several of its products, such as Windows Server, Exchange Server, SQL Server, SharePoint Server and Hyper-V. BPA scans the configuration and settings of these products and compares them with the industry standards and Microsoft's best practices. BPA generates a report that shows deviations or violations from the best practices, along with the severity level, explanation and how to resolve each issue.
BPA improves system security by detecting and fixing any misconfigurations, errors or weaknesses that could expose organizations to attacks or compromise. BPA enhances the performance and functionality of their systems by applying the optimal settings and parameters that suit their specific scenarios and workloads.
What is Windows Server Best Practices Analyzer?
Windows Server BPA is a built-in feature available in Windows Server 2008 R2 and later versions. Windows Server BPA scans the installed roles and features and checks if they comply with the best practices defined by Microsoft based on the feedback and experience of customers, partners and experts. Windows Server BPA can detect issues in several areas, such as security, performance, configuration, operation and maintenance.
You can use Windows Server BPA to run targeted scans in servers that host critical infrastructure workloads, such as AD, Dynamic Host Configuration Protocol (DHCP), DNS and SQL Server. These workloads require high levels of security, availability and performance. Any issues or misconfigurations could have serious consequences for the entire network and organization. Using Windows Server BPA ensures the servers have been secured and built to meet best practices.
You operate Windows Server BPA either with Server Manager or PowerShell. Server Manager is best used if logged in locally and you want to quickly start and/or view the report results. The benefit of using PowerShell is remote execution and running saved scripts as scheduled tasks to assist in vulnerability remediation program tracking.
How to run Windows Server BPA from Server Manager
Admins can run a BPA scan against the entire local server or at specific workloads. The following steps scan the entire server, which is helpful to establish a baseline.
For this tutorial, the target system is Windows Server 2019. To scan an installed role, select the role instead of Local Server in the first step of the following process:
- Open Server Manager. Select Local Server in the left-hand side menu, and scroll down in the main window until you see the Best Practices Analyzer section.
- Click the Tasks drop-down menu on the right-hand side above the Best Practices Analyzer section to expand it.
- Click on the Start BPA Scan button to run the scan.
- When the process completes, review the results from the window.
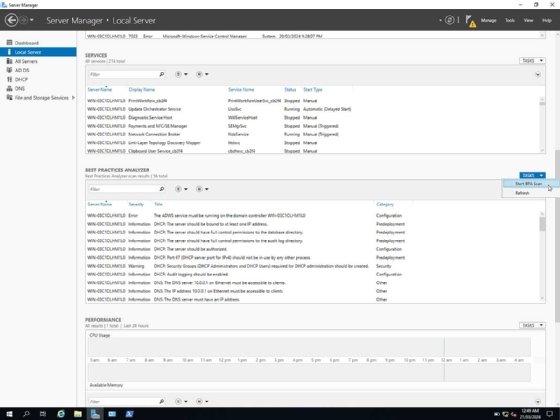
How to run Windows Server BPA with PowerShell
To use BPA with PowerShell, you must find the ModelID of the role or the feature to scan.
Open PowerShell as administrator, and enter the Get-BPAModel command to output the ModelID for the role or features to scan on the Windows Server system.
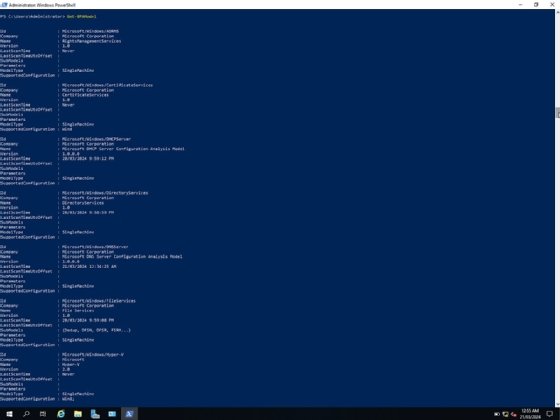
Some of the common ModelIDs on Windows Server are in this chart.
| Role or function | ModelID |
| AD Domain Services (AD DS) | Microsoft/Windows/DirectoryServices |
| DHCP | Microsoft/Windows/DHCPServer |
| DNS | Microsoft/Windows/DNSServer |
| SQL | Microsoft/SqlServer/2012 |
Next, invoke the model to scan with the following PowerShell code. This example checks the DNS server role:
Invoke-BPAModel -modelID Microsoft/Windows/DNSServerThis typically only takes a few minutes to complete.
To see the results of the scan, use the same ModelID syntax, but replace Invoke-BPAModel with Get-BpaResult:
Get-BpaResult -modelID Microsoft/Windows/DNSServer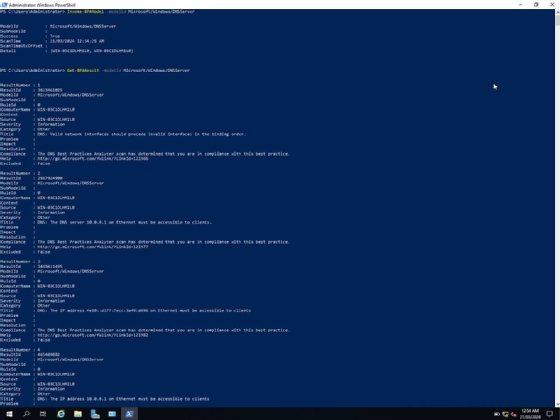
This output isn't easy to read or track. The following code exports to a text file for easier reading:
Invoke-BPAModel -modelID Microsoft/Windows/DNSServer | Out-File -FilePath [filelocation]For even better results, you could create a CSV file of the results to import into Excel to track the remediation of findings:
Invoke-BPAModel -modelID Microsoft/Windows/DNSServer | ConvertTo-CSV | Set-Content "C:\BPA_Results.csv"How to interpret the Windows Server Best Practices Analyzer results
For each BPA scan, it is important to show all results, including those in compliance, not just the issues. Using Excel to open the results in a CSV file enables filtering by severity or category. This makes the data easier to read and helps with remediation planning.
The results have information in several sections, such as the following:
- Severity. Classifies the result into three categories: error, warning and information. Errors are the most severe issues that indicate a violation of a mandatory best practice that could cause serious problems or risks. Warnings are less severe issues that show a deviation from a recommended best practice that could produce minor problems or risks. Information is the least severe issue and could indicate compliance with that best practice.
- Category. This field shows the area or aspect of the system that is covered by the best practice, such as security, performance, configuration, other, etc.
- Title. This field shows a brief description of the best practice.
For issues that are not in compliance, Windows Server BPA provides further information to help the IT staff determine priorities and course of action:
- Problem. This field shows a detailed explanation of the issue, including the current value and the expected value of the setting or parameter that is causing the issue.
- Impact. This field shows the potential consequences or effects of the issue on the system or the network, including reduced security, degraded performance, functionality loss and data corruption.
- Resolution. This field shows the steps or actions IT must take to resolve the issue and comply with the best practice.
- Help. This shows a URL to the Microsoft page with information supporting the remediation.
Admins should examine each issue and consider the category to understand how they relate to the server's specific workload and scenario. For example, some issues may be more relevant or important for certain workloads than others, while some issues may have dependencies or interactions with other problems.
This chart shows some of the possible discoveries uncovered by a Windows Server BPA scan.
| Role or function | Potential findings |
| AD DS |
|
| DHCP |
|
| DNS |
|
| SQL |
|
To follow through with the configuration changes to boost security, admins should follow the resolution steps for each issue and apply the recommended settings or parameters to the system. Admins should also verify the changes are effective and do not trigger any adverse effects or conflicts with other settings or components.
Consider using scheduled tasks to rescan the system with BPA to ensure the issues have been resolved or if any new issues came about from the changes. Admins should also document the changes and update the baseline configuration of the system.
Dwayne Rendell is a senior technical customer success manager for an Australian cybersecurity MSP. He has more than 15 years of experience in IT and specializes in service delivery, value realization and operations management of digital service portfolios. Dwayne has experience in multiple sectors, including health and government. He holds an MBA from the Australian Institute of Business.







