
Fotolia
Shore up defenses with help from Office 365 logs
Logging on Microsoft's productivity platform used in conjunction with other tools can form an effective shield from malicious actors looking to find a way into your organization.
The COVID-19 pandemic and uptick of employees working from home resulted in bad actors doubling down on their efforts to target these users.
Remote users working on purportedly less secure personal computers and networks make attractive targets. This is especially concerning to companies that host some of their workloads in the cloud, such as Office 365, where IT may not have full control or visibility on activities against the systems. To help IT in this area, Microsoft offers security components and continuously enhances these technologies to give administrators the tools and capabilities to self-manage and monitor their Office 365 tenant. What can administrators do to add Office 365 logs to their existing security information and event management (SIEM) setup? And what should be the top priority to monitor?
SIEM is the go-to software for IT administrators to capture event and log information from multiple sources, including network devices, servers and workstations. SIEM centralizes different logs and events to give IT a comprehensive overview of the activity in their environment, which can help with threat detection. For companies that rely on a SaaS model for some of their systems, such as Office 365, having visibility over all the events and activities from the different components can be overwhelming. Microsoft addresses this need by giving administrators the option to use a SIEM product to connect to Office 365 logs via APIs for further analysis. Using SIEM without a strategy to respond to security incidents can be risky business, and this is pushing organizations to take steps to prepare for whatever situation comes their way.
Understand what Microsoft tracks and how you access that data
Office 365 is a collection of more than 20 cloud-based services, including SharePoint Online, Exchange Online, Microsoft Teams and OneDrive. With all these different services, IT must know how to investigate any reported issues and view events captured from each. The unified audit log is located in the Security section of Office 365's admin portal, which is also available directly at the URL protection.office.com/unifiedauditlog.
Recorded events for most of the platform's services, including Exchange Online and Microsoft Teams, can take up to 30 minutes before they show up in the Office 365 logs, while, for others, such as Azure Active Directory, Dynamics 365 CRM and Power Apps, it can take up to 24 hours to record an event. Administrators can choose from more than 100 activities, such as elevation of privilege or failed logins, in the search options with a date range of up to 90 days.
Always consider a SIEM tool for help with security events
Despite the availability of an easy-to-use webpage to search Office 365 logs, IT administrators should consider adopting SIEM software for added features such as the ability to store event data and audit logs in one place to access a comprehensive view of monitoring and operations data.
SIEM tools can help investigate any security event and provide a quick response to any alerts from monitoring identity, network traffic, infrastructure and general usage or consumption of services. SIEM tools assist with matching up any irregular activity in your infrastructure and Office 365 to detect any patterns.
There are several popular products to choose from when it comes to SIEM platforms, including Splunk, LogRhythm, FireEye, SolarWinds and Rapid7.
What Microsoft Azure Sentinel offers vs. other SIEM tools
Several years ago, Microsoft introduced a SIEM platform called Microsoft Operations Management Suite (OMS), which it recently replaced with Azure Sentinel. This new offering is an affordable option that is hosted in the Azure cloud and can be set up within minutes by IT. Azure Sentinel offers several connectors to ingest data logs from services, including Office 365, Microsoft Defender Advanced Threat Protection and AWS, and also supports connectivity to appliances, such as Barracuda Web Application Firewall, F5 BIG-IP and Forcepoint Data Loss Prevention.
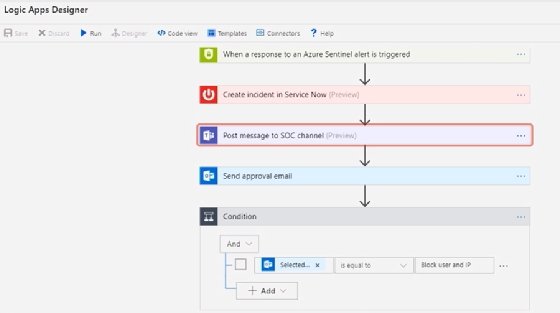
Some features of Azure Sentinel include its artificial intelligence capabilities to detect abnormal activities from all the data captured in the system, which helps keep administrators from having to analyze each event. Azure Sentinel supports customizable automated responses or actions to specific events. Using the Azure Logic Apps, a commonly used workflow engine in Azure, administrators can develop different workflows for specific actions such as resetting a password after too many failed login attempts or creating a service ticket when a high-severity alert happens, as shown in screenshot below. As an added perk, Microsoft does not charge for ingestion of Office 365 logs.
During a time when many of their users are remote, IT workers should actively monitor the Office 365 environment and closely scrutinize security events. The use of Officer 365 logs and other alerts on the platform alone are not enough, but by integrating the platform with a SIEM tool or adopting a new platform, such as Azure Sentinel, will help streamline the monitoring process. Uncovering suspicious activities can reveal bad actors targeting their end users and systems can be detected and dealt with. But security goes beyond just the set of deployed tools, IT managers also need a response plan in place for different incidents. These must be living documents that are updated frequently, like the software used by the organization.






