Set Office 365 group limits to avoid administrative hassles
With help from PowerShell, administrators can tailor Office 365 Groups to develop common-sense restrictions on the tools and other components in the collaboration service.
Office 365 Groups provides the collaborative glue that binds different services, but administrators should implement Office 365 group limits to rein in unchecked access, which could lead to unintended consequences.
An Office 365 group not only contains the membership list for a collection of people, but also manages provisioning and access to multiple services, such as Exchange and SharePoint. At a fundamental level, this means each time a user creates a group for something -- a project, or perhaps a team -- they add a SharePoint site, group inbox, calendar, Planner, OneNote and more.
Groups is also the foundation behind new services such as Microsoft Teams, Office 365's chat-based collaboration app. In addition to messaging via channels, Teams enables users to chat with colleagues over voice and video calls, collaborate on documents and use tabs to display other relevant team information. Teams uses Office 365 Groups to produce a team within Teams, not only for the membership list, but also to connect the underlying group-enabled services for data storage.
Why Office 365 group limits are crucial
By default, Office 365 users can create groups without any restrictions. While this appears to be a great idea to prompt viral adoption, it is likely to backfire.
The strength of Office 365 Groups is only one group is needed to manage a team's calendar, share files among colleagues, and hold group video calls and chats. However, this is not immediately obvious to workers as they explore available services.
For example, a user starts work on a project and, being new to Microsoft Planner, decides to add a plan with the name Project Z Plan. The user also sees he can create a group calendar in Outlook, which he names Project Z Calendar. He feels he could also use a SharePoint site for the project, so he makes one called Project Z. Later, the user discovers Microsoft Teams and feels it can help with the project collaboration efforts, so he generates a new team named Project Z Team.
Each of those actions creates a new group in Office 365. A combined lack of guidance and structure means the worker's actions -- intended to build a seamless fabric that connects multiple Office 365 services -- added multiple silos and redundant resources.
This scenario illustrates the need for administrators to develop Office 365 group limits to avoid similar issues. Users need instruction on what tool to use and when, but also some understanding of what a group is in the context of the organization.
Checklist for a proper Office 365 Groups configuration
Before enabling Office 365 Groups for widespread adoption, the administrator should adjust the basic settings to provide limits and help users adhere to corporate standards.
At a minimum, the IT department should consider the following Office 365 Groups configuration:
- the email address policy for group Simple Mail Transfer Protocol addresses;
- usage guidelines;
- group creation restrictions; and
- group classifications.
Apart from the email address policy, all other configurations require an Azure Active Directory Premium license, as documented here.
Next, define the settings to adjust:
| Policy to update |
Configuration to implement |
Reason for the change |
| Email address |
The company will use the main domain name because all the mailboxes were moved to Office 365. |
|
| Usage guideline URL |
https://contoso.sharepoint.com/usage |
Shows users best practices for producing Office 365 Groups. |
| Group creation restrictions |
Enables line managers group to add Office 365 Groups |
Only managers can create new Office 365 Groups. |
| Group classifications |
Low risk, medium risk and high risk |
Enables users to classify groups and be aware of the sensitivity of the information within the group. |
To make these changes, we use PowerShell to change the configuration in multiple places.
For the email address policy configuration, add a new policy that applies to all groups with the New-EmailAddressPolicy cmdlet:
$UserCredential = Get-Credential
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $UserCredential -Authentication Basic -AllowRedirection
Import-PSSession $Session
New-EmailAddressPolicy -Name GroupsPolicy -IncludeUnifiedGroupRecipients -EnabledEmailAddressTemplates "SMTP:@contoso.com" -Priority 1
For the group configuration settings, use the Azure AD preview module. After connecting to Azure AD, use this code to confirm there is a template for group settings:
Connect-AzureAD -Credential $UserCredential
$Template = Get-AzureADDirectorySettingTemplate | Where {$_.DisplayName -eq "Group.Unified"}
$Setting = $Template.CreateDirectorySetting()
Next, define the group settings based on the configuration defined in the table and apply it:
# Configure the URL for our guidelines
$Settings["UsageGuidelinesUrl"] = "https://contoso.sharepoint.com/usage"
# Disable group creation except for the Line Managers group
$Settings["EnableGroupCreation"] = $False
$Settings["GroupCreationAllowedGroupId"] = (Get-AzureADGroup -SearchString "Line Managers").ObjectID
# Create our list of classifications
$Settings["ClassificationList"] = "Low Risk,Medium Risk,High Risk"
# Apply the settings
New-AzureADDirectorySetting -DirectorySetting $Settings
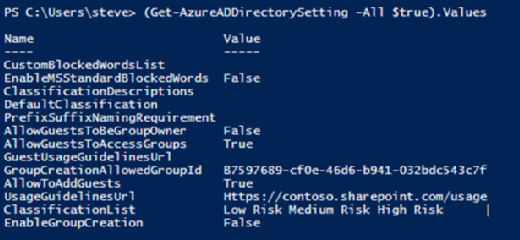
Verify those settings with the following command:
(Get-AzureADDirectorySetting -All $true).Values
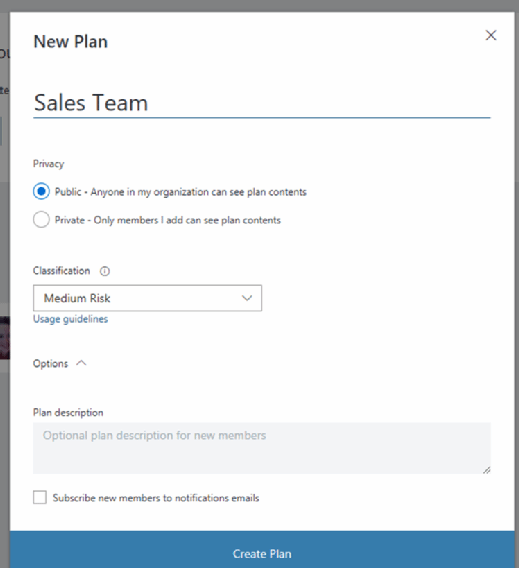
With those adjustments in place, the new Office 365 Groups creation process changes, as shown below.
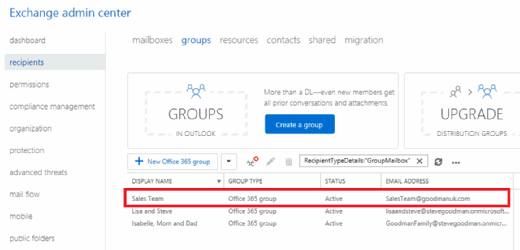
Now, new Groups will have appropriate email addresses assigned -- existing groups remain unchanged.
Add boundaries and reduce complications
It's important for administrators to employ Office 365 group limits. This practice prevents unchecked access to resources in the collaboration platform, which maintains order and avoids problems with redundancy and wasted resources.
Change key settings to put basic governance in place to steer users toward usage guidelines for Office 365 Groups. This helps the administrator ensure the groups are created correctly and can be managed properly as adoption grows.





