
chris - Fotolia
Optimize Windows Server 2019 with file server best practices
A file server deployment must satisfy the needs of both the end user and the IT staff. Tune up Windows Server for a secure and performant repository for your critical data.
Windows file servers remain a steadfast occupant of the data center, despite the fact that many workloads have shifted to the cloud.
The advances in the recent versions of Windows Server make on-premises file servers an attractive option versus comparable cloud services. Organizations that use Windows Server 2019 file servers benefit from data deduplication for increased space savings, and higher levels of security and performance from refinements to the Server Message Block (SMB) protocol. When you deploy a new Windows Server, Microsoft's guidelines steer you to the proper settings for better protection, as well as reliability to ensure the best possible end-user experience.
Keep the installation lean
As you deploy a Windows Server 2019 file server, it is likely that you will need to install additional components. However, it is important to avoid adding roles or features the server doesn't need to do its job. For example, a dedicated Windows file server should have Hyper-V server role.
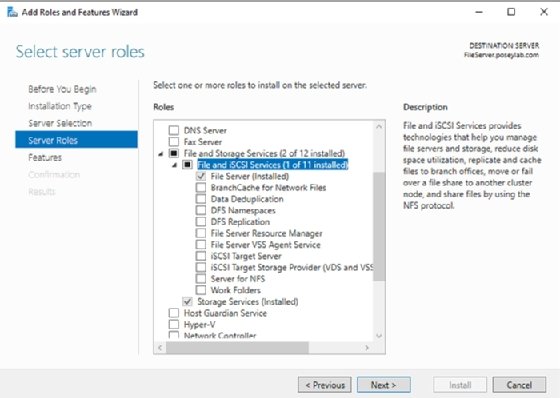
When you install unnecessary features or multiple roles, it increases the server's footprint, which can reduce file server performance. Also, when more code runs on a system, this increases the attack surface to make the server less secure. As a best practice, you should install only necessary components for a file server to operate.
Run a scan to maintain Windows Server 2019 file server best practices
You should periodically run the Best Practices Analyzer on your Windows files servers. This tool, which has been part of the OS since Windows Server 2008 R2, compares your file server's configuration against Microsoft's established best practices.
There are two main reasons why this routine checkup is important. First, as Microsoft's best practices for Windows servers evolve and the company updates the utility to reflect those changes. Regular scans validate your file server configuration. Not every issue is severe enough to mandate a change but could show an area where an adjustment might improve performance or reliability.
Second, configuration drift often occurs through the course of Windows Server management, particularly in environments with a large IT team. The Best Practices Analyzer detects modifications to settings that violate best practices.
To run a best practices scan on a Windows Server 2019 file server, open Server Manager and select the File and Storage Services tab. Next, scroll to the Best Practices Analyzer and choose the Start BPA Scan option from the Tasks menu.
The Best Practices Analyzer will scrutinize the file server role and generate a list with a severity level for each issue that includes information and potential remediation actions.
Consider the required versions of SMB
Consider which version of SMB needs to run on the Windows file server. There are three different versions of the SMB protocol, but most organizations won't need to run all three versions.
There are times Microsoft's Windows Server 2019 file server best practices recommendations are not accurate. This is when it helps to use your institutional knowledge as a Windows administrator. For example, the Best Practices Analyzer might give you bad advice with the SMB configuration. Windows Server 2019 disables SMB 1.0 by default, but the Best Practices Analyzer recommends you enable it, as shown in Figure 3.
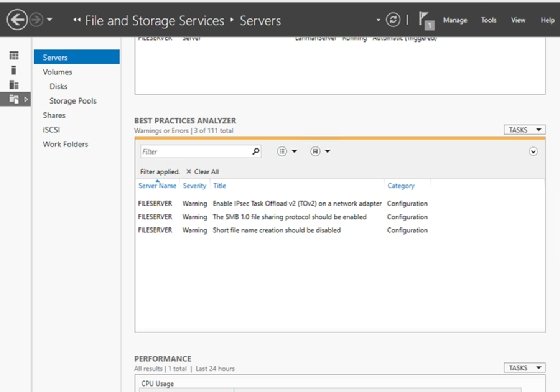
The SMB 1.0 protocol helps with older Windows systems' backward compatibility, but SMB 1.0 is also very insecure. That being the case, it's best to ignore the Best Practices Analyzer's advice and leave SMB 1.0 disabled, unless you have compelling reason to use it.
If possible, use the Resilient File System
Many organizations have historically avoided the Resilient File System (ReFS) in favor of the NT File System (NTFS), and for good reason. The ReFS was developed for data resiliency, but the 1.1 version released with Windows Server 2012 was extremely limited in its capabilities compared to NTFS. Many NTFS features did not exist in ReFS, such as the ability to boot the system.
Microsoft continues to develop ReFS and, now, most of the NTFS features exist in ReFS. ReFS version 3.4 in Windows Server 2019 is far more feature-rich than the 1.1 version, but there are still some areas where it is lacking. For instance, ReFS does not support file system compression, encryption, disk quotas or DOS-compatible 8.3 filenames.
If you can live without these features, there are significant benefits to ReFS. It is far more scalable than NTFS and supports volume sizes up to 35 PB. ReFS includes several features to protect the integrity of the data on the volume. Windows Server 2019 has a proactive error correction feature that periodically scans ReFS volumes and automatically repairs corrupt data.
Use Distributed File System in large organizations
The Distributed File System (DFS) in Windows gives a way to create a single namespace that encompasses multiple file servers. This makes it easier for users to find data without needing to know which server holds the files. DFS can make multiple data replicas and silently redirect user requests to the file server that is closest to the user.
A DFS namespace can incorporate more than just Windows file servers. You can add any file server that supports SMB file shares to a DFS namespace, which can be helpful in organizations with both Windows file servers and network-attached storage appliances.
Use the File Server Resource Manager to enforce compliance
Lastly, you should use the File Server Resource Manager (FSRM) to control the file server. FSRM is a Windows Server role used to enforce quota on folders on the file server and generate reports on storage usage to name a few features.
FSRM also has the added benefit of a file screening function that prevents users from storing certain filetypes on the file server. You determine how the system responds when a user tries to save a type of file, such as an executable. In this age of ransomware, it's another method at your disposal to prevent an attacker from encrypting all your files.








