
James Thew - Fotolia
Microsoft Defender ATP taps into cloud for added protection
Enterprises that want to wrap up their systems in an extra layer of security have the option for more enhanced protection that integrates with other Microsoft products.
It's a full-time job to defend a Windows shop from security breaches.
In fact, many organizations simply use an "assume breach" mentality regarding their current defense posture, meaning they constantly monitor and check for vulnerabilities in their environment. There are many products designed to defend the host against malicious attackers. Microsoft Defender Advanced Threat Protection (ATP) is the tech giant's expansive threat protection platform.
Microsoft Defender ATP monitors endpoints for in-memory and kernel-based attacks. It also checks for potential system issues, such as vulnerable drivers. These features complement the more commonplace vulnerability scanning and malware detection techniques to find network exploitations, keylogging attempts and malicious scripts. Microsoft Defender ATP is the embedded interface that connects to the cloud-based Microsoft Defender Security Center.
The Microsoft Defender Security Center portal gives administrators the proverbial single pane of glass for management and control across the organization for many Windows Security features, including Windows Firewall, antivirus and performance monitors. Alerts reported by Microsoft Defender ATP can be dealt with manually or automatically based on certain criteria. To dig deeper into specific incidents, an analyst can access a timeline of real and historical data from a client or from a wide range of systems.
Microsoft continues to invest heavily in this endpoint security protection product to expand beyond the Windows OS. In fact, Microsoft Defender ATP used to be called Windows Defender ATP but underwent a name change now that it supports non-Microsoft OSes, such as Linux and macOS.
Dig deeper with Microsoft Defender ATP
A key feature of Microsoft Defender ATP is its post-breach forensics functionality to determine the proper remediation on endpoints.
Microsoft Defender ATP taps into the advanced analytic capabilities that come courtesy of the machine learning technology in the Microsoft Intelligent Security Graph, an overall security fabric that collects data from endpoints worldwide that is analyzed to determine the viability of an emerging threat.
Security teams are able to drill down and get a high level of detail to understand the full scope of a breach from attacks on endpoints. They can use behavioral analytics to watch the attack progress through your environment, as well as provide guidance on response. Below is an example of a timeline of an attack on a particular machine generated by Microsoft Defender ATP.
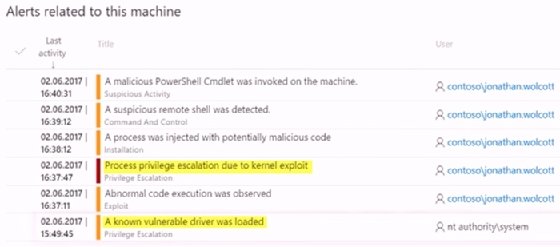
How to use Microsoft Defender ATP automation levels
For some enterprises, Microsoft Defender ATP might manage several hundred or thousands of machines resulting in a plethora of alerts. To deal with this level of activity, the ATP service has an automated investigations feature, which uses inspection algorithms and playbooks to examine and remediate incidents. Each incident appears in an automated investigations list with details such as the current status and detection source.
Microsoft Defender ATP comes with automation levels including Not Protected, Semi and Full. The default action is for semiautomatic remediation, which requires approval from the user before any action is taken when the ATP service detects malicious activity. A complete breakdown of each of the automation levels is included in the table below.
| Automation level | Description |
| Not protected |
|
| Semi -- any remediation |
|
| Semi -- non-temp folders remediation |
|
| Semi -- core folders remediation |
|
| Full |
|
After determining the extent of the damage, additional steps can be taken to defend the network from further attack, such as blocking the malicious URL with the Windows Firewall and shoring up defenses by updating to the latest definition files, disabling macros and enabling backups of critical data.
Microsoft Defender ATP also integrates with the Office 365 platform to protect from threats that come via email.
Integration with Exploit Guard
Microsoft Defender also works with Windows Defender Exploit Guard, an optional add-on to ATP. Exploit Guard provides more tools to mitigate exploits at runtime by giving enterprises more control on how code runs on their machines. It is similar to the technology it replaced, Microsoft EMET, by using intrusion prevention to stop attacks.
Exploit Guard joins with other technologies in the Microsoft ecosystem, such as Windows Defender SmartScreen. It dynamically blocks malicious websites based on the filters in SmartScreen, providing an extra layer of defense that is particularly useful for organizations that rely on a remote workforce.
Microsoft Defender ATP in action
One example of Microsoft Defender ATP's capabilities and versatility is its security integration and event management (SIEM) integration for use with detecting certain attacks, such as the WannaCry ransomware, which encrypted files on vulnerable Windows machines.
Sigma is an open source project that creates a generic signature format for SIEM systems. Microsoft Defender ATP supports this multi-tool search engine language. Users who subscribe to Microsoft Defender ATP can test how to import Sigma files by downloading the WannaCry.yml file from the project's GitHub site at this link.
Next, convert the yml file to a Sigma rule using the Python-based Sigmac tool at its GitHub site.
python sigmac — target mdatp .\win_mal_wannacry.yml
The Microsoft Defender interface provides a way to copy and paste these converted files and save them as a query with a descriptive name, such as WannaCry.
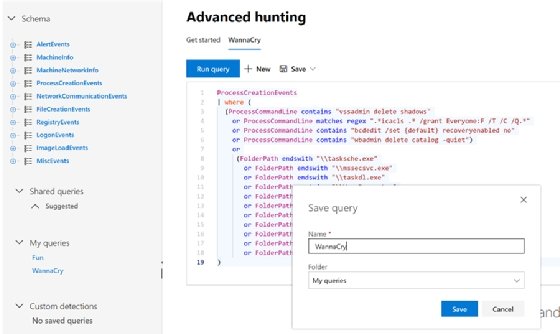
Microsoft Defender-saved queries can be converted into detection rules. These rules will run automatically every 24 hours.
If Microsoft Defender ATP detects WannaCry in the environment, it can determine if the threat has affected other machines on the network using the Microsoft Defender ATP Search. The search function works with a file hash, filename, malicious URL or IP addresses.






