
peterschreiber.media - stock.ado
Learn to configure Office 365 alerts and other security features
More users are working from home, which makes them tempting targets for malicious actors. Take the time to fortify your environment by deploying Office 365 protections.
It's not a coincidence that reports of increased cyber attacks coincided with the spike of remote workers due to the COVID-19 pandemic.
Malicious actors have doubled down on their efforts to infiltrate enterprises to launch ransomware attacks or plant cryptomining malware to set up a steady revenue stream. Security experts have reported an increase in phishing attacks to lure users into clicking on links that puts systems -- and the organization -- at risk. These threats add more pressure on IT to implement additional security measures.
Microsoft Office 365 offers a host of cloud-based tools and services that support businesses when it comes to email, collaboration tools, cloud storage and enterprise content management. All are accessible from anywhere to support remote workers along with a distributed workforce. But it also increases the surface attack and poses a risk for companies that have just begun to let employees connect from home networks and even personal computers. This is pushing IT to rethink their security strategy to ensure company data is protected and consider some of the existing security tools integrated with the collaboration platform, such as Office 365 alerts, monitoring and identity protection tools.
Government notification issued to help Office 365 customers
The Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory, at this link shortly after most states issued stay-at-home orders to slow the spread of the coronavirus. CISA shared its recommendations for organizations that use Office 365 to incorporate into their tenant to reduce their vulnerability level.
The CISA memo noted that rapid deployment of Office 365 might have left some companies with gaps in their security arrangement and advised administrators to enable multi-factor authentication as well as role-based access controls. These recommendations can help reduce the risk of hackers using stolen credentials to access company systems, especially those account credentials with elevated permissions.
Get a security rating of your Office 365 tenant
The CISA memo also recommended using the Microsoft Secure Score feature to generate the overall security scorecard of the tenant and company.
Secure Score is a separate portal for Office 365 administrators that gives a grade for your organization's security posture along with suggestions to improve it. The portal breaks down the scoring based on five categories: identity, data, device, apps and infrastructure.
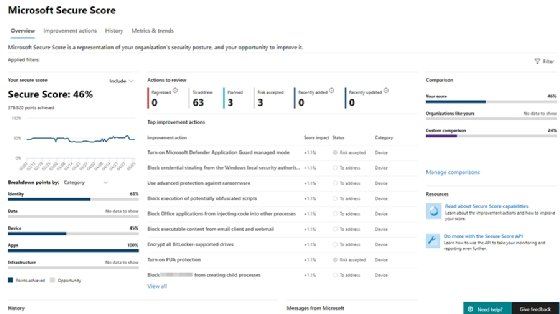
In each category, Microsoft gauges the level of security and offers configuration advice if the number is below 100%. The portal also provides valuable details in each area by describing any problems the assessment tool identified in the tenant and how administrators can address them using an action plan.
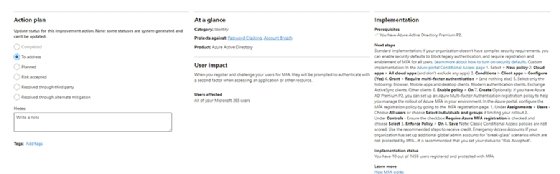
Checking the Secure Score regularly can help IT administrators see their progress using the trends section of the portal indicating the progress made with the various security implementation projects.
Set up Office 365 alerts for suspicious activities
The CISA memo also suggested configuring Office 365 alerts in the Security and Compliance Center to help the IT team react to security incidents quickly. Office 365 alerts can be sent via SMS or email to administrators, who can sign into the alerts dashboard in the Officer 365 security portal to review the content of the alert and address the issue.
Microsoft provides more than 21 different policies that address several issues related to threat management, permissions elevation changes, information governance and data leaks, and message delivery delays. The CISA memo suggested setting up Office 365 alerts for logins from unusual locations and for user accounts that have surpassed their email thresholds.
An example of an alert in the screenshot below warns administrators when a user or multiple users delete an abnormally high volume of documents, which could indicate an intentional destruction of digital documents or it could be a user deciding to clean off their machine of old data.
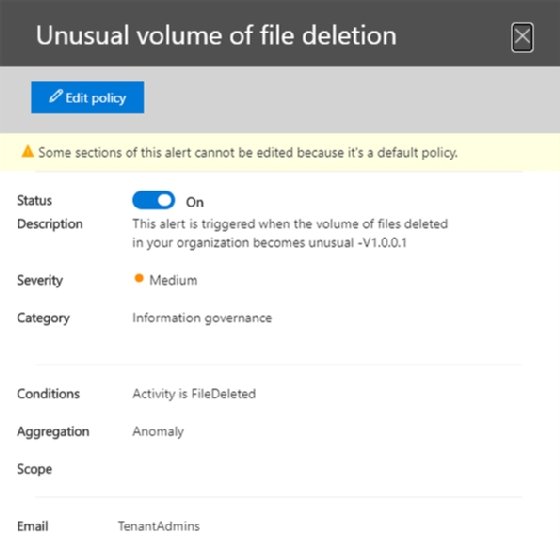
Microsoft recommends administrators enable all the 21 default policies in their tenant. Many of them, such as elevation of admin privilege or suspicious outgoing email patterns, can indicate the start of an attack that, if acted on quickly, can be stopped before extensive damage occurs.
While administrators can customize Office 365 alerts for multiple unusual activities, Microsoft also offers enhanced security features in its Cloud App Security product, which features proactive remediation when an alert is triggered. When an incident is detected, the system can automatically react and either block the user or stop the action without the intervention of the IT administrator.
Some of the advanced alerts Microsoft recommends administrators enable include:
- leaked credentials;
- unusual file share activity;
- ransomware activity;
- unusual administrative activity;
- suspicious inbox forwarding;
- impossible travel;
- risky sign-in;
- activity from suspicious IP addresses;
- activity from an infrequent country.
It's one thing to detect unusual behavior but it's another to respond fast enough to stop a potential breach before it enters the company's environment. The enhanced security features in Office 365 Cloud App Security blocks suspicious users and activities, similar to how Azure AD Premium P2 stops suspicious login attempts, on behalf of the administrator, which can help a fatigued IT staff from having to be on alert at all times.
Integrate use of SIEM tool for audit log analysis
Part of the work with security administration extends beyond reviewing Office 365 security logs. IT departments generally use other security monitoring tools to manage other areas, including network traffic, end points, firewalls and servers.
Many organizations rely on security information and event management (SIEM) tools to centralize and manage all the incoming alerts and logs to uncover activity that requires a closer look. One of the final CISA recommendations is for administrators to feed Office 365 audit logs and alerts into their existing SIEM tools to find any unusual activity and see if there are signs of similar events in other parts of the organization.







