Getty Images/iStockphoto
How to perform an AD group membership backup and restore
You can fix some problems with Active Directory with a few clicks, but things get difficult when they involve many layers of group membership. Here's a few ways to avoid trouble.
Active Directory groups and their group memberships are a key security tool in any organization, so when something goes wrong in this area, it needs to be corrected quickly.
Assigning access via groups is one of the most common ways to control access to resources in your Active Directory domain. Most organizations have hundreds, if not thousands, of groups in their Active Directory. Even though they are important to the enterprise, backing up AD groups and group memberships to protect against loss is not a common task. There are a few AD group membership backup and restore options administrators should be aware of should trouble occur.
What are Active Directory group memberships?
In Active Directory, a security principal is an entity that can authenticated by the operating system. When referring to Active Directory, security principals are more commonly referred to as objects. The two most common security principals in Active Directory are user and computer objects.
A user object represents an individual or a service and a computer object represents a specific computer. These objects can use resources in a domain only if access to those resources is allowed. For example, a user can print to a network printer once we grant the user access to the resource.
For resources to be used by many individuals or computers, it makes more sense to assign access via a security group. Security groups are collections of security principals grouped together into manageable units. A security group can contain any combination of users, computers and even other groups.
We can think of the concept of group membership in multiple ways. For example, the list of users, computers or groups that are assigned to a security group makes up a security group's group membership. But users and computers also have group membership lists. A group membership list for a user would be the list of groups that the user is a member of. For this article, when I refer to a group membership, it means the group membership of a security group.
A group's membership list is created from two distinct scenarios. The first scenario is when we create a new group, and we have a defined list of users to be added to the group. In this scenario, we add all the users in one bulk operation.
The other more common scenario is when administrators add people to an existing group over time. The group membership for very active groups may have taken years to get to its current iteration. If the group is deleted and needs to be re-created, the group membership list could be difficult to re-create due to this incremental change over time. It may require significant effort to find all those old requests and regenerate the group membership.
Where is group membership information stored?
Active Directory allows us to give objects names that are recognizable and familiar. For example, admins often name user objects based on some combination of a user's first and last name. Computer object names are often based on hardware model numbers, department names or company inventory serial numbers.
People use the object's name to identify objects in the directory. Active Directory assigns each object a security identifier (SID). Active Directory uses an object's SID to define and control what an object can and can't access. Active Directory uses SIDs because names can change but the SID for an object will always be the same.
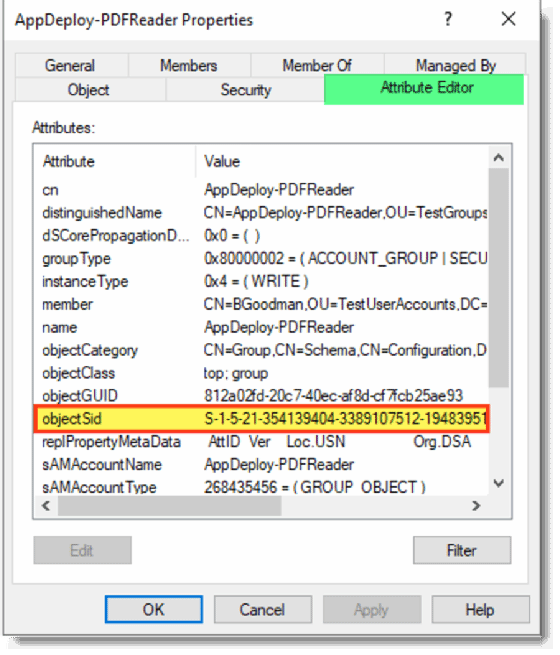
When a group is created, the Active Directory database assigns an SID to the group. Active Directory maintains a table in its database for that group and for the members that get added to the group.
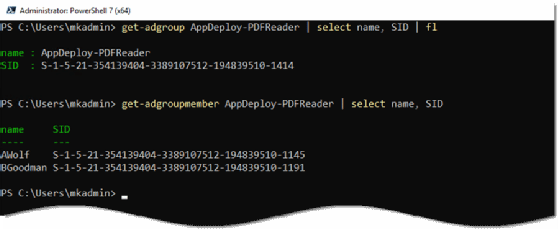
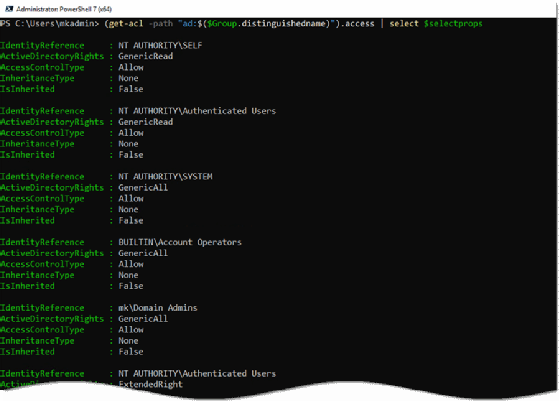
Active Directory saves and tracks information about the group, including the group SID, the SID of each object in the group and the SID of other objects in Active Directory that can manage the group's settings. Active Directory tucks away this information but it is accessible through the GUI and PowerShell if you know where to look. The following example uses a PowerShell command to read an access control list for a group.
Get-ACL -path "ad:$($Group.distinguishedname)").access | select $selectprops
What happens if things go wrong with Active Directory?
Microsoft previewed Active Directory in 1999 and has released new features with every major OS release since its debut. Active Directory is one of the most reliable pieces of software that I have worked with in my more than 20 years in IT, but bad things can still happen.
Objects inside the database can get damaged, making them unreadable. This corruption can happen for a few different reasons, most of them related to user error. One example is when objects are changed by two different people within a very short period, such as a few seconds, and the changes cause a conflict, making the data unreadable. Another example is when objects get damaged when moving large amounts of data between separate organizational units (OUs) in Active Directory and the file-write process gets interrupted.
These are rare events. A more common situation is when a user or group is removed from Active Directory but a reference to the object remains. This happens when a user or group is added to a folder and then the object is deleted from Active Directory. The access control list for the folder will still show the reference to the object that was deleted by showing an SID instead of the object's name.
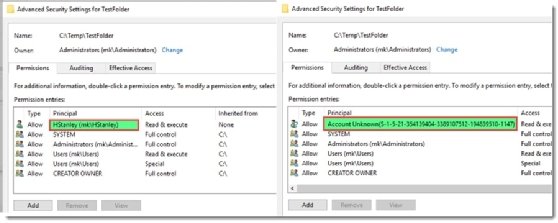
What is the Active Directory tombstone process?
From very early on, Microsoft understood that objects in Active Directory needed protection. When an object -- a user, computer, group, OU and others -- is deleted in Active Directory, the object moves to a hidden container in the database. The object no longer appears in Active Directory, but it has not been physically deleted from Active Directory.
At that point, a timer starts and when it reaches a predetermined point, the object is permanently deleted. This process is called the tombstone lifetime. Before the tombstone lifetime expires for a deleted object, it remains in this hidden container and can be restored through a simple process. After the tombstone time expires, the object is physically removed from Active Directory and can only be restored from an earlier offline backup.
How do you change the Active Directory tombstone lifetime?
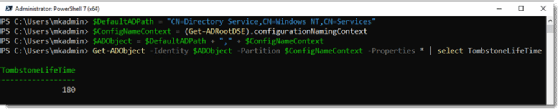
The default time for the tombstone process was 60 days in the first release of Active Directory. Microsoft increased the default time to 180 days with Windows Server 2008. We can adjust the maximum tombstone lifetime in the latest versions of Active Directory to 365 days. You can run the following PowerShell commands to check the value for your domain.
#Standard path for AD environments $DefaultADPath = "CN=Directory Service,CN=Windows NT,CN=Services" #Your corp's naming context $ConfigNameContext = (Get-ADRootDSE).configurationNamingContext #Create ADObject by joining variables $ADObject = $DefaultADPath + "," + $ConfigNameContext Get-ADObject -Identity $ADObject -Partition $ConfigNameContext -Properties * | select TombstoneLifeTime
How do you restore a deleted user of a group object?
Restoring an object from the hidden container is easier today than years past because of PowerShell. You could also use the LDP tool or NTDSUTIL to restore deleted objects. The tool you choose to restore the objects is not the challenge; it's the syntax you use to do a restore.
Active Directory uses LDAP, and the syntax of LDAP commands can be quite cryptic. To perform our search, we'll need to use an LDAP filter, which return results faster than standard Active Directory PowerShell filters, but they are difficult to read or write. I use them only in unique circumstances, such as file restoration.
Before we can restore an object with PowerShell, we need to find the deleted object information. We use the Get-ADObject cmdlet and use an LDAP filter to query only deleted objects. Without the LDAP filter, we would return both active and deleted objects. We could still find the result, but we would need to sift through a potentially giant data set.
Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=*)" – IncludeDeletedObjects
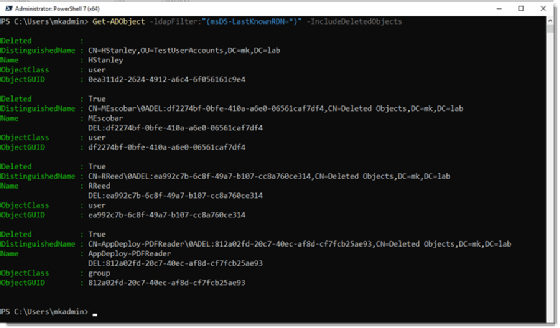
The example shows only a few deleted objects, which makes finding the right deleted object easy. However, you might have hundreds or thousands of deleted objects in a production version of Active Directory. You need to find the object you want to restore from within the list of deleted objects, which is easier than it sounds. We can find the name of the object in the Name field or in the DistinguishedName field. Once you know where to look, you can search for the name with some simple PowerShell code.
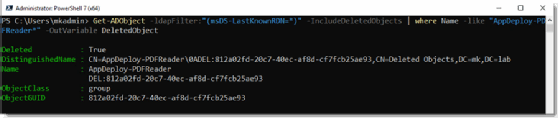
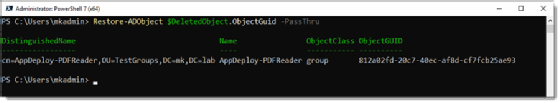
The following PowerShell command executes a search for a group named AppDeploy-PDFReader and will save the output to a variable named $DeletedObject. AppDeploy-PDFReader is the start of a longer string of data. The * wildcard character matches anything starting with AppDeploy-PDFReader.
Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=*)" -IncludeDeletedObjects | where Name -like "AppDeploy-PDFReader*" -OutVariable $DeletedObject
Once we have the object information, we can restore the object with the Restore-ADObject cmdlet. This cmdlet needs one of the following data types for a successful object restore:
- distinguished name;
- GUID (objectGUID);
- security identifier (objectSid); or
- Security Account Manager account name (sAMAccountName).
The restore syntax is very simple, but it has no output by default, which means we need to use the -passthru parameter to see the results. The following PowerShell code example uses the ObjectGUID to identify which object to restore, but you can sometimes just pass the variable and it will figure out which property to grab on its own.
Restore-ADObject $DeletedObject.objectGUID -passthru
How the Active Directory Recycle Bin works
The Active Directory Recycle Bin arrived in Windows Server 2008 R2 and gives administrators another way to restore deleted Active Directory objects from a GUI with relative ease. It is possibly the best feature introduced to Active Directory in the last 15 years. It will make your job easier when a critical object -- or multiple objects -- have been deleted.
You saw in the previous example that the restore isn't too hard with PowerShell. But the AD Recycle Bin makes recovering a deleted object a simple operation that only requires a few clicks. At one of my former employers, an IT staffer accidentally deleted 800 security groups with one accidental click of a mouse. The AD Recycle Bin made the restoration process very easy.
The only downside with the AD Recycle Bin is it can be difficult to find if you're not familiar with it, and you must be turn it on manually before it can be used.
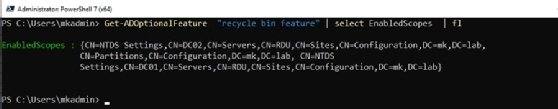
To check the status of the Active Directory Recycle Bin, you can use PowerShell. Use the following code; if it returns a list of scopes, then the AD Recycle Bin is enabled.
Get-ADOptionalFeature "recycle bin feature" | select EnabledScopes
How to enable the Active Directory Recycle Bin
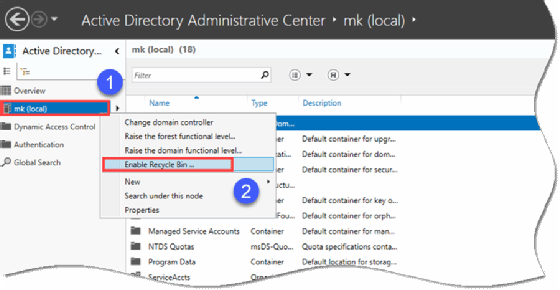
There are two methods to turn on the Active Directory Recycle Bin. Once you activate the Recycle Bin, you cannot disable it.
If you are more comfortable using the GUI, then you can use the Active Directory Administrative Center by right-clicking on the domain name in the lefthand pane and selecting Enable Recycle Bin.
You can also use the following PowerShell command to enable the AD Recycle Bin.
Enable-ADOptionalFeature -Identity 'Recycle Bin Feature' -Scope ForestOrConfigurationSet -Target 'mklab.local' -Server dc1
What are the prerequisites required to enable the Active Directory Recycle Bin?
You must meet the following prerequisites before using the Active Directory Recycle Bin:
- The Active Directory schema must be extended to at least Windows Server 2008 R2.
- All domain controllers in the forest must be Windows Server 2008 R2 or above.
- The forest and domain functional level must be Windows Server 2008 R2 or higher.
There's one more piece that needs to be running properly but isn't always mentioned. The replication between domain controllers must be up to date, and the domain must be healthy.
I have a lab domain that I use for demos. When I tried to activate the AD Recycle Bin in my test domain, I received the following error: "The FSMO role ownership could not be verified because its directory partition has not replicated successfully with at least one replication partner."
My lab had a domain controller that I had not used in a very long time. It was powered off for a few months, and its secure channel to the other domain controllers was broken. I tried to reset it following Microsoft's documentation but had no success. I had to force demote the domain controller and then re-promote the domain controller to resolve the issue. For a lab, this is fine but this would be a much bigger problem in a production domain.
How to restore a group with the AD Recycle Bin
Once you have the Recycle Bin enabled, performing an object restore is very simple.
First, launch the Active Directory Administrative Center. Once the console is open, look for a folder called Deleted Objects.
Click on the Deleted Objects folder in the left pane, which will show a list of deleted objects.
Find the object to recover, right-click on it and select Restore to complete the process.
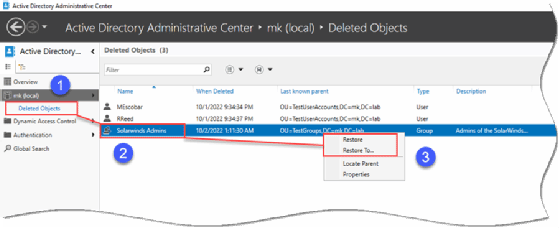
You can also restore objects to a different place than the original location if you prefer.
How to restore a group membership list
Performing a backup and restore for group memberships is more difficult. It's not possible to restore a group membership from the built-in AD tombstone process or from the AD Recycle Bin.
There is no mechanism to restore a group membership list because Active Directory does not save the group membership info when it changes. The only related data that's recorded is the separate entries into the security event log that notes a change was made to a group membership and what object was removed. But that information isn't actionable, so what is possible?
A backup plan for Active Directory or any important piece of infrastructure should never rely only on a recycle bin. Regular backups should be taken. Those backups will contain copies of groups and the group members. You can then restore the group membership by picking the backup time frame to restore the object.
Backup applications for Active Directory are as old as Active Directory itself. There are many third-party products to choose from, and Microsoft also includes a backup utility in Windows which must be installed for it to be available.
What are potential problems from an Active Directory object restore?
When you restore a deleted AD group from any method -- the AD Recycle Bin, offline backup or the tombstone process -- there is one possible drawback. A group object contains at least two pieces of information: the group information and the group membership information. If I delete the group and also delete the object of a group member, I would need to restore both objects for the group membership to show correctly.
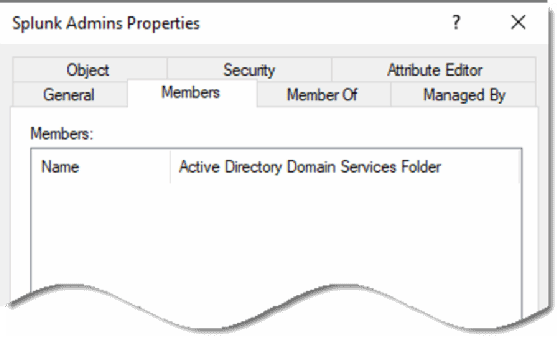
In the following example, I deleted the group named Splunk Admins and then I deleted the object named DGreenhaus, who is the only member of the Splunk Admins group. However, I only restored the group object. When I check the restored group, the group membership is blank.
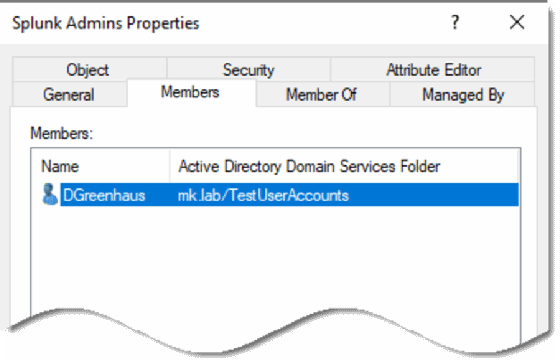
If I go back and restore the DGreenhaus object, it restores the user to the group membership list.
With care, you can avoid Active Directory restore issues
Active Directory has two tools to restore Active Directory groups and their group memberships. For at least 180 days, deleted objects will be available through the built-in tombstone process. Using the AD Recycle Bin will make the object restore process an easy task. The only caveat is that Active Directory cannot restore a previous version of a group's group membership list. However, this risk is mitigated if you take regular offline backups.