Sergey Nivens - Fotolia
How to use a Microsoft Entra ID emergency access account
A break-glass account in Microsoft's identity and access management platform helps avoid disruptions in a crisis. Follow these best practices to keep these credentials safe.
There are no guarantees in life, but an emergency access account is the closest thing for IT to maintain access to crucial systems when a crisis hits.
Many organizations rely heavily on Microsoft Entra ID, formerly Azure Active Directory, for identity and access management. But what happens if there's an issue with multifactor authentication or the primary device tied to an admin's account is stolen? These aren't hypothetical situations, but real challenges faced by companies. When quick access is vital, organizations can't afford a disruption caused by a lockout. This is where the concept of an emergency access account (EAA), also called a break-glass account, comes into play. These accounts act as a safety net that lets trusted personnel access vital systems despite adverse scenarios. Organizations that use Microsoft Entra ID should prepare for the worst and learn how to create and use EAAs while applying best practices.
What is a break-glass account?
A break-glass account is a high-privilege, emergency account in Microsoft Entra ID. It ensures access to resources when availability issues occur. Given its power and purpose, this account must be heavily protected with strict security policies and protocols.
Regardless of size or sector, every organization can face unexpected situations that threaten regular access. Here are some scenarios where a break-glass account becomes indispensable:
- Account lockout situations. The break-glass account can restore access if an admin's account becomes accidentally locked out due to incorrect password attempts or misconfigured policies.
- Issues with multifactor authentication. What happens if the MFA mechanism fails or there's a delay with authentication codes? If an administrator cannot accept or validate an MFA request, a break-glass account configured without MFA gives an alternative access path.
- Risk of reliance on single devices. Admins might have their Microsoft Entra ID accounts tied to specific devices. If that device is lost, stolen or malfunctions, an emergency access account can resolve this type of lockout.
Beyond simply acting as a backup access mechanism, the break-glass account does the following:
- Ensures business continuity. In the face of technical hitches or security breaches, companies can continue to operate, minimizing downtime and potential revenue loss.
- Bolsters security protocols. An emergency backup lets IT teams implement robust security measures without the worry of a lockout.
- Facilitates rapid response. During a cyberattack, organizations can respond quickly, potentially mitigating risks and damages.
Break-glass accounts are for emergencies only, not routine tasks. It's crucial to closely check the account's activity through regular monitoring and audits to prevent unauthorized usage or security breaches.
Prerequisites for a Microsoft Entra ID emergency access account
A Microsoft Entra ID EAA setup has several prerequisites. The core of most Microsoft Entra ID functionalities lies in its licensing. Two of the primary licenses that provide advanced identity protections are the following:
- Microsoft Entra ID P1 license. Provides advanced identity options and functionality to create and customize policies. It includes modifying conditional access policies, which is essential to set up and manage EAAs.
- Microsoft Entra ID P2 license. Offers additional identity protection and governance features. While not strictly necessary for EAAs, it gives organizations even more flexibility and security options.
A minimum of a Microsoft Entra ID P1 license is recommended to make full use of an EAA.
It is also important to monitor EAA activities to ensure their integrity and to detect any unauthorized or unusual usage patterns. Azure Monitor is one service that can be used to collect, analyze and act on telemetry data from your Azure resources.
Before creating an EAA, determine the following:
- Identify potential admin users. Who will have access to the EAA? Select trustworthy individuals due to the elevated nature of these accounts.
- Determine emergency scenarios. Clearly define what constitutes an emergency to limit the account to appropriate use.
- Plan for audits. Set a timeline for regular checks on the account's usage to quickly detect and investigate non-emergency access.
How to set up a Microsoft Entra ID EAA
You create an EAA the same way as a regular cloud-only account within Microsoft 365, Microsoft Entra ID or Microsoft Entra. EAAs are regular user accounts with specific configurations and permissions. To create an EAA, go to the Microsoft Entra Admin Center at entra.microsoft.com and select Create a new user.
Next, give the account a username, a name and a long, complex password for the account.
EAAs must be cloud-only, not domain accounts. However, the same concept could work for on-premises applications and services. You should create two EAAs and assign one to use MFA and one that doesn't use MFA.
You must include or exclude security and identity protections, depending on the account. For example, you need to exclude the EAA without MFA from any specific configuration for Azure MFA, third-party MFA or conditional access policies that enforce MFA.
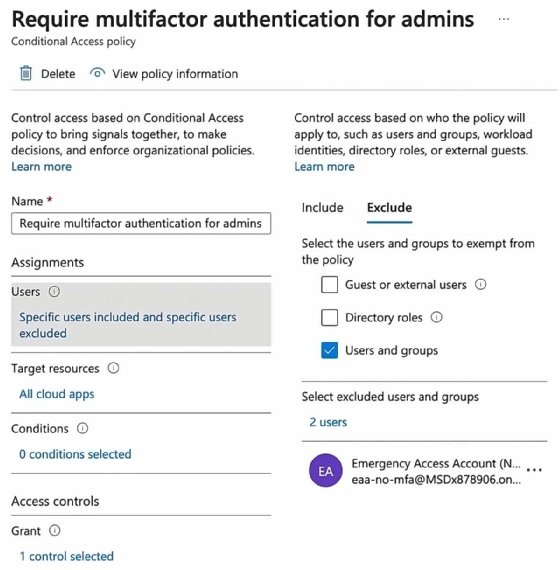
Be sure to set up the EAA with the following parameters:
- Independence from individual users. The accounts should not be tied to any specific employee or their devices, such as mobile phones or hardware tokens. Store registered devices in a secure location with multiple communication channels to Microsoft Entra ID.
- Strong and distinct authentication. Use robust authentication methods for these accounts, distinct from other admin accounts. For example, if a primary admin account uses the Microsoft Authenticator app, then employ a FIDO2 security key for emergency accounts. Avoid external dependencies in the authentication process.
- Non-expiring credentials. The device or credential for the account should not expire and be exempt from automated cleanups due to inactivity.
- Permanent role assignment. In Microsoft Entra ID Privileged Identity Management, designate the Global Administrator role for emergency access accounts as permanent, not just eligible.
How to harden security for emergency access accounts
EAAs are invaluable to maintain continuous access to vital resources, and their high-privilege nature makes them critical as a last line of defense. How can you bolster the security layers around these essential accounts?
As the master key to an organization's most critical digital assets, a break-glass account will tempt malicious actors, making it necessary to minimize any vulnerabilities. This enhanced protection limits exposure to hackers, reducing the chance of detection and access to the account. A robust defense also safeguards EAAs from accidental or deliberate misuse by internal users and helps organizations adhere to the stringent security standards mandated in many industries.
To bolster EAA security, consider splitting the password. Make a robust and intricate password and divide it into two 10-character sections for a 20-character password. Each segment goes to one person to reduce the risk of total compromise if one part is revealed during a breach. This practice also fosters team collaboration to access the EAA. The team can further improve security by placing password sections in different physical vaults, encrypted digital repositories with MFA, bank safety deposit boxes for heightened security and tamper-evident envelopes to make unauthorized access attempts readily apparent.
How to test and verify emergency access accounts
It is important to have an EAA, but it's also vital to regularly train the staff on how to access, use and validate these accounts.
Administrators and support staff must be familiar with the following processes:
- Inform security monitoring personnel of ongoing activities to check the EAA.
- Refresh documentation on the emergency break-glass process to keep it current.
- Train administrators and security officers on emergency procedures.
- Update and validate emergency account credentials, especially passwords.
- Confirm users have not linked MFA or self-service password resets to personal devices or details.
- Ensure all necessary admins have access to a device used for MFA. The device should have at least two distinct network communication paths, such as a facility's wireless and cell provider networks.
Waiting for an emergency to test the sturdiness of security measures surrounding EAAs is not just impractical, but not ideal. Taking a proactive approach is necessary to be sure access is seamless and secure. A test will highlight areas that need improvement and familiarizes the team with the process to reduce the chances of human error in a high-stress situation. To maintain the readiness of EAAs, the admin team should conduct tests at regular intervals, ideally every quarter, and after major system or policy changes.
Liam Cleary runs his own consulting company that helps customers work with Microsoft 365 and Azure-based technologies. He specializes in internal and external collaboration, document and records management, business process automation and implementing security measures.