What is Active Directory (AD)?
Active Directory (AD) is Microsoft's proprietary directory service that enables network admins to manage users, permissions and their access to networking resources. It runs on Windows Server and stores information about objects, such as shared network resources, on a corporate network in a logical, hierarchical format. This enables administrators to manage those resources, as well as the users who need to access those resources to get their work done.
A domain controller is needed to run the AD service. A domain controller is a server running a version of the Windows Server operating system that has Active Directory Domain Services (AD DS) installed. By installing AD DS, admins can configure a specific server role for a computer, such as the role of a domain controller.
What is the role of Active Directory and what is it used for?
Active Directory stores data about all the objects on a network. An object is a single element, such as a user, group, application or shared device, such as a server or printer. Objects are normally defined as either resources, such as printers or computers, or security principals, such as users or groups.
Active Directory uses a set of rules known as the schema to define object classes and their attributes. The schema also determines the format of each object's name. AD also includes a global catalog that contains information about all the objects. The schema and global catalog make it easy for network admins to identify and manage objects. Also, by storing relevant information about user accounts on a network, such as their names and passwords, AD enables other authorized users and admins on that network to access this information.
AD also enables admins, users and applications to publish and find objects and the objects' properties. They can do this via AD's query and index mechanism. Additionally, AD provides a replication service that has two roles. It ensures that all domain controllers in a network contain a complete copy of all directory information for their domain, and it ensures that any change to the data in the directory is replicated to all domain controllers in the domain. By maintaining replicas of directory data on all domain controllers, the replication service ensures the directory's availability and also optimizes its performance for all users.

What is Active Directory Domain Services?
In older versions of Windows Server -- Windows 2000 Server and Windows Server 2003 -- the directory service was named Active Directory. However, from Windows Server 2008 R2 and Windows Server 2008 onward, Microsoft changed the name of the directory service to Active Directory Domain Services.
AD DS stores directory information, including information about user accounts. It does this using a structured data store known as the directory. This directory enables the directory information to be organized in a logical and hierarchical format. AD DS also makes directory data available to authorized network users and administrators, allowing them to access it as required.
As with AD, AD DS includes a replication system that automatically builds and updates the global catalog server, which is a domain controller. This catalog stores a full, writable replica of all objects and their attributes in a domain, as well as partial, read-only replicas of all the other domains in the forest. Such attribute replication makes it easy for users and admins to search for objects in AD DS.
AD DS provides security through built-in sign-in authentication and access control mechanisms. These mechanisms allow authorized users to access network resources and enable admins to easily manage directory data and organization throughout the network using a single network username and password.
To further support network admins, AD DS provides policy-based administration. This enables admins to easily manage even complex networks.
Active Directory modes, protocols and services
Several different services constitute Active Directory. The main service is Domain Services, but Active Directory also has the following other services:
- Active Directory Lightweight Directory Services (AD LDS) is an independent mode of AD, meaning it operates independently of AD domains or forests and can be installed without affecting AD. It provides directory services for applications, including a data store, and uses standard application programming interfaces (APIs) to access application data. However, it doesn't include AD's infrastructure features.
- Lightweight Directory Access Protocol (LDAP) is a directory service protocol used to access and maintain directories over a network. Based on a client-server model, LDAP runs on a layer above the TCP/IP stack. LDAP cannot be used to create directories or to specify how a directory service should operate. Its main function is to help with directory management.
- Active Directory Certificate Services (AD CS) is used to generate, manage and share public key infrastructure certificates. A certificate uses encryption to enable a user to exchange information over the internet securely with a public key. These certificates provide confidentiality through encryption; authenticate computers, users and device accounts on a network; and help to maintain the integrity of digital documents through digital signatures.
- Active Directory Federation Services (AD FS) authenticates user access to multiple applications -- even on different networks -- using single sign-on (SSO). As the name indicates, SSO only requires the user to sign on once rather than use multiple dedicated authentication keys for each service. By allowing the secure sharing of digital identity and entitlements rights across security and enterprise boundaries, AD FS helps to streamline user experiences as they access internet-facing applications.
- Active Directory Rights Management Services (AD RMS) enables organizations to protect their documents using information rights management (IRM). With AD RMS, they can create IRM policies to specify who can access sensitive information, thus preventing its use or misuse by unauthorized people.
Key features of AD and AD DS logical model
Active Directory Domain Services uses a logical model consisting of forests, domains and organizational units (OUs). This model is important because it provides a way to do the following:
- Store and manage information about network resources.
- Store and manage application-specific data from directory-enabled applications.
- Enable administrators to organize users, computers, devices and other elements of a network into a hierarchical containment structure.
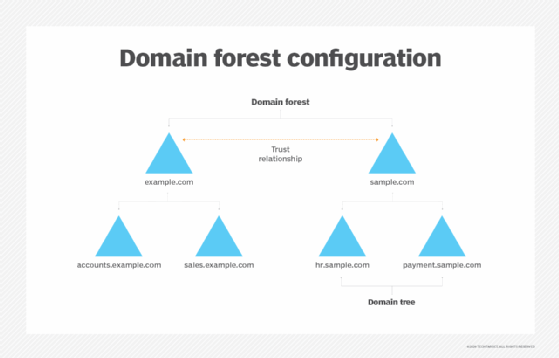
Different objects, such as users and devices that share the same database, are on the same domain. A tree is one or more domains grouped together with hierarchical trust relationships. A forest is a group of multiple trees. Forests provide security boundaries, while domains -- which share a common database -- can be managed for settings such as authentication and encryption. These different elements have the following functions:
- A forest is the top-level container in AD DS. It refers to a group of one or more AD domains. It provides a common logical structure for those domains and automatically links them with two-way, transitive trust relationships. These relationships enable AD DS to provide security across multiple domains or forests. They also enable domains to extend authentication services to users in domains outside their own forest.
- A domain is a container or partition within a forest. It provides network-wide user identity, so user identities need to be created only once. Once that is done, they can be referenced on any computer joined to the forest in which that domain is located. Domains use one or more domain controllers to store user accounts and user credentials, provide authentication services for users and control access to network resources. A domain controller for a particular domain has a copy of the directory for the entire domain in which it is located.
- An OU is the smallest element of the AD DS logical model. OUs form a hierarchy of containers within a domain. Admins typically use OUs to simplify administrative tasks, such as the application of Group Policies. OUs are also useful for the delegation of authority, which allows owners to transfer administrative control -- full or limited -- over objects to other users or groups in order to simplify the management of those objects.
The domain-forest-OU model of AD DS applies regardless of the network topology and the number of domain controllers required within each domain.
Key features of AD and Active Directory Domain Services
One of the main features of AD and AD DS is that they use a structured and hierarchical data store to logically organize and publish directory information, i.e., information about the objects stored in the AD DS directory. These objects may include the following:
- Users.
- Groups.
- Computers.
- Domains.
- OUs.
- Security policies.
A standardized schema is used to define object classes, attributes and names, as well as the constraints and limits on instances of these objects. The default schema in AD is modeled after the International Organization for Standardization X.500 series of standards for directory services. It is also extensible, meaning classes and attributes can be added to it and modified as needed. The AD schema is stored in the schema directory partition and replicated to all domain controllers in a forest.
Another important feature of AD is that it uses four directory partition types to store and copy different types of data in the Ntds.dit file on a domain's domain controller. Users and administrators can access this information throughout a domain. A directory partition typically contains data about a domain, configuration, schema and applications.
AD and AD DS feature a query and index mechanism. This mechanism enables network users or applications to find objects and their properties stored in AD. Finally, AD's replication service distributes directory data across a network. AD includes Knowledge Consistency Checker, which automatically creates replication connections from a source domain controller to a destination domain controller and generates the replication topology for the AD forest.
Trusting terminology
Active Directory relies on trusts to facilitate authentication and to provide security across multiple domains or forests. These trust relationships apply to both domains and forests in AD. AD trusts work properly only if every resource has a direct trust path to a domain controller in the domain in which it is located. Also, to enable facilitation, Windows checks if a domain being requested by a user or computer already has a trust relationship with the requesting account's domain.
The most important trust-related terms used in AD include the following:
- A one-way trust is when a first domain (Domain A) allows access privileges to users on a second domain (Domain B). However, Domain B does not allow users access to Domain A. Simply put, it is a unidirectional authentication path between Domains A and B.
- A two-way trust is when two domains trust each other. Thus, authentication requests can be passed between these domains, meaning each domain enables access to users of the other domain.
- A trusted domain is a single domain that enables user access to another domain, which is called the trusting domain. Forests used trusted domain objects to store all of the trusted namespaces, such as domain tree names, user principal name suffixes, service principal name suffixes and security identifier namespaces used in partner forests.
- A transitive trust can extend beyond two domains and allow access to other trusted domains within a forest. In AD, a two-way, transitive trust relationship is automatically established between new domains and parent domains in a forest.
- A nontransitive trust is a one-way trust that is limited to two domains. It is typically used to deny trust relationships with other domains.
- A forest trust provides seamless authentication and authorization across multiple AD forests, thus enabling access to resources and other objects in those forests. It can be one-way or two-way transitive.
History and development of Active Directory
Microsoft offered a preview of Active Directory in 1999 and released it a year later with Windows 2000 Server. Microsoft continued to develop new features with each successive Windows Server release.
Windows Server 2003 included a notable update to add forests and the ability to edit and change the position of domains within forests. Domains on Windows 2000 Server could not support newer AD updates running in Server 2003.
Windows Server 2008 introduced AD FS. Additionally, Microsoft rebranded the directory for domain management as AD DS, and AD became an umbrella term for the directory-based services it supported. AD DS is available in all the latest versions of Windows Server, including Windows Server 2016, Windows Server 2019, Windows Server 2022 and Windows Server 2025.
Windows Server 2016 updated AD DS to improve AD security and migrate AD environments to cloud or hybrid cloud environments. Security updates included the addition of privileged access management. PAM monitors access to an object, the type of access granted and what actions the user takes. PAM adds bastion AD forests to provide an additional secure and isolated forest environment. Windows Server 2016 ended support for devices on Windows Server 2003.
In December 2016, Microsoft released Azure AD Connect, now called Microsoft Entra Connect, to join an on-premises Active Directory system with Azure AD, now called Microsoft Entra ID. Through this integration, organizations could connect all the identities and access controls on their local networks with Microsoft's cloud services, such as Office 365, and enable user-friendly SSO for those services. Azure AD Connect worked with systems running Windows Server 2008, Windows Server 2012, Windows Server 2016 and Windows Server 2019. All 1.x versions of Azure AD Connect were retired on Aug. 31, 2022.
Domains vs. workgroups
A workgroup is Microsoft's term for Windows machines connected over a peer-to-peer (P2P) network. Workgroups are another unit of organization for Windows computers in networks. Workgroups enable these machines to share files, internet access, printers and other resources over the network. P2P networking removes the need for a server for authentication. There are several differences between domains and workgroups:
- Domains, unlike workgroups, can host computers from different local networks.
- Domains can be used to host many more computers than workgroups. Domains can include thousands of computers; workgroups typically have an upper limit of close to 20.
- In domains, at least one server is a computer, which is used to control permissions and security features for every computer within the domain. In workgroups, there is no server, and computers are all peers.
- Domain users typically require security identifiers, such as logins and passwords, unlike workgroups.
Main competitors to Active Directory
Other directory services on the market that provide similar functionality to AD include the following:
- Red Hat Directory Server is an LDAP-based directory that manages user access to multiple systems in Unix environments. It provides a network-based registry to centralize identity information and includes user ID- and certificate-based authentication to restrict access to data in the directory. In addition, it provides centralized, fine-grained access control over the directory and enhanced data protection, even if the number of systems and users increases.
- Apache Directory is an open source project that runs on Java and operates on any LDAP server, including systems on Windows, macOS and Linux. It provides an LDAP v3-compliant directory server and an Eclipse-based directory tool called Apache Directory Studio. Additionally, the software includes an Apache Directory LDAP API that provides a convenient way to access all types of LDAP servers.
- OpenLDAP is another open source alternative to AD. Specifically, it is an open source implementation of LDAP, with modules like a standalone LDAP load balancer daemon; standalone LDAP daemon (server); and various libraries, tools and sample clients to implement LDAP.
IT must carefully manage various Group Policies for desktops to ensure the correct policies are implemented. Learn when AD domain-joined Group Policy overrides local.






