
buchachon - Fotolia
Consider Office 365 MFA to thwart attacks
More remote users are working on their own equipment, which opens an organization to a hack attempt. Office 365 customers can use multifactor authentication to lower this risk.
With governments worldwide issuing stay-at-home orders, many organizations have looked to cloud collaboration platforms, such as Office 365 to keep employees working. With new technology comes new risks that threaten those companies that have no control over devices being used to connect remotely.
Due to the COVID-19 pandemic, the number of remote workers increased sharply, leading to a consequent rise in phishing attempts. Companies that just require one factor -- a password -- to verify its users can leave themselves vulnerable to an outside attack. To address this security gap, administrators are implementing multifactor authentication (MFA) to strengthen the protections around Office 365 to verify users that sign in to use these cloud services.
Office 365 MFA requires modern authentication
Office 365 MFA provides an additional security layer to ensure the person using a login is legitimate, not a hacker using stolen credentials. This feature is available in Office 365 Business Premium and Enterprise plans to verify login attempts to Exchange Online and other Office 365 services.
To start, the administrator must enable modern authentication for their tenant. This can lead to issues for organizations still using legacy versions of Microsoft Outlook, such as Outlook 2010. To avoid difficulties, clients would need to upgrade to the 2013 version or newer.
To configure Office 365 MFA, the administrator must be a member of at least one of these roles: global administrator, SharePoint administrator, Exchange administrator, conditional access administrator, security administrator, help desk administrator, password administrator, billing administrator, user administrator or authentication administrator.
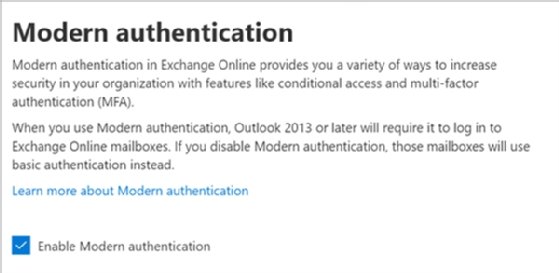
Next, the administrator must go to the Office 365 admin portal (admin.microsoft.com), then navigate to Settings > Settings and select the Services tab and choose Modern authentication. Once selected, a pop-up window appears as shown in Figure 1 and the Enable Modern authentication checkbox can be selected.
Administrators can also run the following PowerShell command to enable modern authentication after connecting to Exchange Online PowerShell:
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
Setting up Office 365 for end users
Next, the administrator can start Office 365 MFA for their end users in their tenant by browsing to the following URL and signing in with their credentials. (This URL is shown in the User panel in the General tab when making editors to a user account in the portal.)
https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx?BrandContextID=O365
To apply Office 365 MFA to a user, the administrator selects the user and chooses the enable MFA option. The administrator can notify the end user and share a link that assists them with choosing their preferred MFA option, which includes:
- Receiving a call to confirm the individual
- Receiving a notification through the mobile app
- Receiving a code via text or SMS
- Using the Microsoft Authenticator app
Administrators can also enable Office 365 MFA for multiple users at once. The MFA portal provides an option to download a sample CSV file the administrator can use as a template to populate with the list of users that require MFA, and, once completed, it can be uploaded and processed.
PowerShell can also be used to enable MFA for one or multiple users.
For individual users, use the following PowerShell script:
Import-Module MSOnline
Connect-MsolService
$st = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement
$st.RelyingParty = "*"
$st.State = "Enabled"
$sta = @($st)
Set-MsolUser -UserPrincipalName [email protected] -StrongAuthenticationRequirements $sta
For multiple users:
$users = "[email protected]","[email protected]","[email protected]"
foreach ($user in $users)
{
$st = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement
$st.RelyingParty = "*"
$st.State = "Enabled"
$sta = @($st)
Set-MsolUser -UserPrincipalName $user -StrongAuthenticationRequirements $sta
}
Using third-party MFA offerings
Administrators also have the option to use a vendor's MFA technology from companies such as Okta, RSA and Symantec to integrate with Office 365. Why consider a third-party MFA product? Microsoft's cloud platform is not impervious to outages; downtime in Azure, which supplies the Office 365 MFA functionality, can block administrators and users alike when they try to access the collaboration platform.
Another way to increase security while using Office 365 is to use hardware-based tokens for MFA needs. Deepnet Security and Token2 sell programmable tokens that display a six-digit authentication code. These options are fully compatible with Office 365 and offer an alternative to using a smartphone or an app for MFA.
While an improvement over one-factor authentication, MFA will not guarantee protection from credential leaks. Administrators should consider implementing other security features on the Office 365 platform, such as security reports, access controls and reviewing logs that detail administrative access to the system.








