Quest Authentication Services
Quest Authentication Services allows organizations to extend Active Directory (AD) to Unix, Linux and Mac platforms and enterprise applications. It enables the unification of identities and directories for simplified identity and access management.
 |
Quest Authentication Services allows organizations to extend Active Directory (AD) to Unix, Linux and Mac platforms and enterprise applications. It enables the unification of identities and directories for simplified identity and access management.
 |
|
Quest Software Inc.'s Authentication Services was designed to enable platforms such as Unix, Linux and Mac to participate completely with Microsoft Active Directory. It also includes a purpose-built user interface so users can locate and manage Mac OS X settings and preferences from Active Directory. For those working in heterogeneous environments, Quest Authentication Services creates a single point of management and authentication for most non-Windows systems.
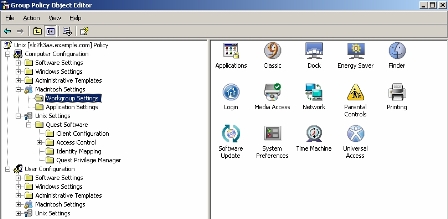
Quest now extends these features to Mac OS X. For example, Managed Client Extensions for Group Policy provides Group Policy functionality for all Mac Workgroup Manager policies and preferences. The product is based on an existing Active Directory installation.
With Authentication Services, administrators can perform the following tasks:
- Extend Group Policy management to third-party applications. Managed Client Extensions for Group Policy automatically interprets the Preference Manifest file and includes it in the user interface, which provides a single point of management for Group Policy from Active Directory.
- Manage Group Policy without additional infrastructure. Authentication Services uses the existing Active Directory infrastructure and an extension of the Group Policy Management Console to enable GP on Mac. There is no need for an additional dedicated directory or proprietary console and interface.
System requirements: The client supports Mac OS X 10.4 and 10.5.
Pricing: $65 per enabled Mac user.






