dynamic link library (DLL)
What is a dynamic link library (DLL)?
A dynamic link library (DLL) is a collection of small programs that larger programs can load when needed to complete specific tasks. The small program, called a DLL file, contains instructions that help the larger program handle what may not be a core function of the original program.
An example of those tasks might be communicating with a specific device, such as a printer or scanner to process a document. DLL files that support specific device operations are known as device drivers.
DLL contains bits of code and data, like classes and variables, or other resources such as images that the larger program can use.
In addition to being a generic term for dynamic link libraries, Dynamic Link Library is also the name of Microsoft's version of the shared library concept for Windows. A shared library can exist in any operating system (OS).
How does a dynamic link library work?
Computer programs are rarely written in a one file. They often are composed of multiple files that are linked together.
When a program is run, it must be compiled from its source code, which is human readable code that the programmer writes. It's turned into an executable file, which is binary code, or machine code, that the computer can read.
The computer goes through several intermediate steps for this to occur. During those steps, multiple files are linked to one. There are two types of linking -- static and dynamic -- and two types of corresponding link libraries:
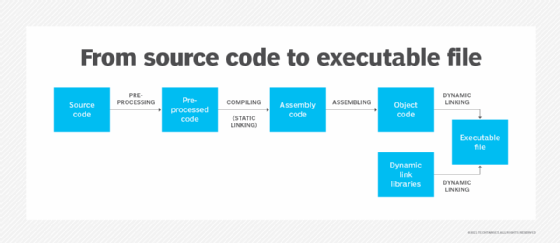
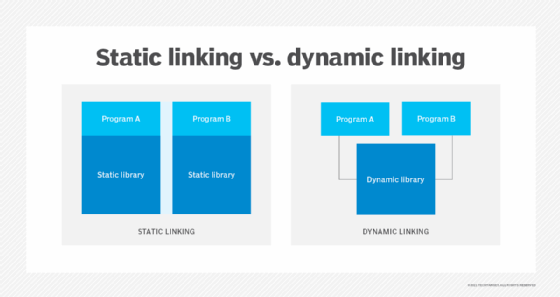
Static links. These are linked earlier in the process and are embedded into the executable. Static libraries are linked to the executable when the program is compiled. Dynamic libraries are linked later, either at runtime or at load time. Static libraries are not shared between programs because they are written into the individual executable.
Dynamic links. DLLs contain the files that a program links to. The libraries already are stored on the computer, external to the program that the user writes. They are called dynamic because they are not embedded in the executable -- they just link to it when needed.
An import library, which is a type of static library, replaces all placeholder symbols with actual links to the necessary DLL data in the main program at load time, pulling those functions from the DLL library. Programs provide the name of the library, and the OS creates a path to the link library. Different programs have their own language-specific calling conventions for linking to DLLs.
Because dynamic libraries are not written into the executable, the same shared library can be used by more than one program at the same time. They can also be modified without changing the entire program that is using it.
A dynamically linked program has a small bit of code that maps the DLL into virtual memory, where the program can access it at runtime or load time. With this setup, the dynamically linked program doesn't have to repeatedly access physical memory to access the library. Virtual memory links the same page of physical memory to different programs' virtual addresses -- also known as address space -- as different processes are run.
In the Windows operating systems, dynamic files have a ".dll" file extension, and static files have a ".lib" extension. DLL files may also have ".ocx" (ActiveX), ".cpl" (Control Panel) or ".drv" (driver) suffixes, depending on the DLL function.
Programs do not always need dynamic libraries. In some cases, static linking is preferable. However, some programs specify DLLs that are needed to run and will return an error message if they cannot be accessed.
What are the advantages of dynamic linking?
Dynamic linking and DLLs offer the following advantages:
- Fewer faults. Problems are less likely to occur at runtime because the DLL is not repeatedly retrieved from the disk. Several processes can use the same page of RAM at once, eliminating the chance of error in the paging process.
- Memory efficiency. DLLs help operating systems and programs run faster, use memory efficiently and take up less disk Space is saved in memory because the files aren't loaded along with the main program. For example, if a user is editing a document in Microsoft Word, the printer DLL file does not need to be loaded into memory. If the user decides to print the document, the Word application calls the printer DLL file for loading. DLLs are loaded into memory just once. In static linking, system libraries must be loaded into each program, which means every process has its own copy of the same library. That takes up more memory.
- Modular architecture. DLLs are part of a modular architecture, which lets a program be delivered modularly. A developer does not have to install the whole application as one executable. Instead, it can exchange certain libraries and components, without changing or rewriting the entire application. It can do this when working with other programs or when selling or updating applications.
What are the challenges of dynamic linking?
Some of the downsides of dynamic linking include the following:
- Errors. Some executables require certain DLLs to be present before they can run. If the DLL cannot be found, an error message may appear, notifying the user that the application couldn't start. The problem of broken dependencies in DLLs and shared libraries is sometimes referred to as dependency hell.
- Exploits. DLL hijacking, also known as DLL injection, is a common exploit in Windows applications that takes advantage of the order in which the DLL is loaded. A threat actor can insert a malicious .dll file in the path where a legitimate .dll file would be expected to load. That could cause the main application to load the malicious DLL file with the executable. To do this, the hacker must know the .dll files that an executable will call and then give the malicious file the same file name as the legitimate file it's replacing. The infected .dll file can deliver malware to the device running or make the device vulnerable to another exploit. For example, the 2020 SolarWinds hack used DLL injection to create a backdoor into the company's Orion platform.
- Speed. The dynamic linking process is slower than it is for static linking. Because dynamic linking happens at runtime or load time, it takes more CPU cycles than loading at compile time. However, a system's OS is faster with dynamic linking because it uses fewer resources most of the time.
How do you fix DLL errors?
DLL errors are common because of the volume of DLL files found on Microsoft Windows systems and how often they are used. Errors happen when an application can't find a file and cannot run without it.
Common reasons for DLL errors include:
- Malware
- File corruption
- File deletion
Redownloading the DLL file is one way to fix an issue. However, this can overload memory and create a duplicate file if the original is still on the device.
A better solution involves troubleshooting the DLL problem or doing a few basic maintenance tasks, such as restarting the computer and checking the recycle bin to see if the file was accidentally deleted. If the file was deleted, but is not in the recycling bin, users can try a file recovery program.
A missing DLL error can be a sign of a computer virus or exploit, so a malware scan may be needed. A system restore from a previous backup could solve the problem by bringing the computer's OS back to its state before the DLL file was corrupted.
Microsoft also offers several DLL troubleshooting tools, such as:
- Dependency Walker. A free utility that documents all the DLLs a program uses and checks for circular dependencies and the validity of DLL files.
- DLL Universal Problem Solver. An auditing tool with several utilities. One example of what the tool does is load two DLL files side by side in their own text files and produce a third text file that contains the differences between the two files.
- A DLL help database. Guides users in identifying different DLL types.
Learn about other application security threats in addition to DLL hijacking and how to prevent them.