What is Active Directory Domain (AD Domain)?
An Active Directory domain (AD domain) is a collection of objects within a Microsoft Active Directory network. An object can be a single user or a group, or it can be a hardware component, such as a computer or printer. Each domain holds a database containing object identity information.
AD is the foundation of most modern Windows-based network management. It's part of the Windows Server family of operating systems (OSes). Conceptually, AD is often visualized as a classic telephone directory where users can look up anyone with a telephone and know their location and the number at which to reach them.
What is an AD domain?
An AD domain is a logical grouping of the objects held within AD. These objects -- which are the smallest logical unit -- may be users, computers or organizational units (OUs). Objects within a domain share common administration, security and protection behaviors, and are usually located on the same physical network. IT staff are responsible for managing the objects within a domain. An enterprise can establish numerous domains.
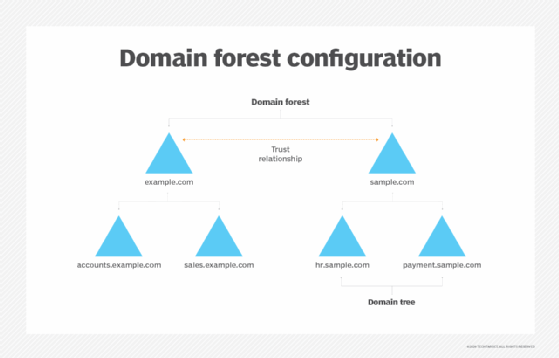
A collection of AD domains is called a forest. Domains and forests form the basis of the logical structure of Windows AD. A forest acts as the security boundary of this structure. Structuring domains in a forest provides data and service autonomy and optimizes replication (within a region). Also, the logical structure can be used to "compartmentalize" data and thus control access to it.
How do AD domains work?
A domain is a label or category representing a logical grouping of objects or resources that Active Directory manages. Most enterprise admins won't create domains often, as domains are typically long-term entities that rarely change. However, they might need to add new domains periodically as the enterprise grows and organizational demands evolve. For example, a business adopting Microsoft 365 might need to add a new domain to AD.
The process of adding a domain involves the following steps:
- Log into the current domain controller (DC).
- Access the Active Directory Domains and Trusts dialog.
- Select Properties for Active Directory Domains and Trusts by right-clicking the top button in the left tree view and selecting Properties from the dropdown menu.
- Add the new domain name to the Alternative UPN Suffixes field in the UPN Suffixes dialog.
- Click Apply and close the windows. The domain is added to the selected domain controller.
Admins can also opt to select replication options for other domain controllers. Once completed, the new domain name can be used in Active Directory. Adding a new domain name doesn't affect any users, and new users and other objects can be added to the domain as required.
What is the AD domain used for?
In practice, Active Directory is fundamentally a database designed to hold all the relevant information about users and endpoints -- such as servers and storage -- across the enterprise network. AD also provides a suite of directory services that associate those network resources with their network addresses, ensuring that information is available to the entire network. In addition, AD handles security, such as authentication to ensure that only valid users are allowed onto the network, and authorization to ensure that valid users can access only resources to which they're entitled.
Microsoft's Active Directory Domain Services (AD DS) provides a way for storing directory data and making it available to admins. This data may include user account data, such as names and passwords. Apart from admins, other authorized users on the network can also use AD DS to access this information. AD DS is part of the Windows Server operating system.
Tools to manage domains in Active Directory
Active Directory Domains and Trusts is one of the tools available for managing domains and Active Directory. Admins can use the Microsoft Management Console (MMC) to administer domain trusts, functional levels (domain and forest), and user principal name suffixes.
Other native AD management tools can be installed using Remote Server Administration Tools and include the following:
- Active Directory Administrative Center (ADAC). A tool available with multiple versions of Windows Server to simplify the management of multiple AD domains across a forest.
- Active Directory Sites and Services. An administrative tool that includes a Microsoft MMC snap-in to manage sites and related components in large, multisite networks.
- Active Directory Users and Computers (ADUC). An MMC snap-in to manage various tasks related to AD objects, such as password changes, user account resets, creation (or deletion) of OUs, delegation of object control, etc.
- Active Directory Service Interfaces (ADSI) Edit. A tool to edit AD (e.g., create or modify items), manipulate attributes, and troubleshoot issues related to AD object properties.
- Active Directory module for Windows PowerShell. A module to manage AD domains by consolidating a group of cmdlets.
Active Directory vs. domain controller
Every Active Directory domain requires a domain controller, a conventional computer server that runs AD DS software, and a version of Windows Server OS. The DC uses data stored in AD for authentication, authorization, policy administration and group management. DCs can also store a global catalog of all objects from all the domains in the forest to allow global searches. This DC is called a global catalog server.
It's important to note that a DC is a mission-critical business resource. If the DC server or database fails, the network and its resources could become inaccessible to users. An organization typically runs two or more DCs operating in tandem to share the network traffic load and provide operational resilience. Domain controllers each maintain an independent copy of the AD database, and the controllers automatically synchronize using replication so that changes made to the directory on one DC replicate on the other DCs as well.
How is Active Directory structured?
Active Directory is structured like a tree. The easiest way to understand the various concepts in the AD structure (including domains) is to consider the five major elements of the AD tree.
Objects
An object is the lowest-level, or most granular, logical unit of an AD structure. It can be a user account, a computer or server, a group, a share such as a storage volume, or a device such as a printer. Every object can have one or more attributes that detail its properties and limitations. These attributes are specified in the AD schema as formal definitions.
Organizational units
Objects within AD are structured into logical groupings called organizational units, which are also considered objects. They allow administrators to organize the objects better within AD. OUs can be nested, meaning one OU can hold other OUs. However, an object can only be placed in one OU at any time.
Groups
Groups are a different way of organizing objects within AD. A group is a collection of objects, such as users, where a group grants the objects common properties such as permissions. For example, all users within a group can receive access to certain file shares. Objects can be members of more than one group. Groups objects can be placed into OUs.
Domains
A domain is a logical grouping of objects, which can include individual objects, such as computers, as well as groups and OUs. A domain typically exists within a physical network, such as a corporate LAN, and an admin or admin team manages it. An organization can easily have two or more domains. For example, a business with multiple physical offices might have a domain for each physical office, such as "us.company.com" for the U.S. location and "eu.company.uk" for the U.K. office location.
Trees
Domains can be organized into trees. For example, a business with multiple domains at a given site might organize those domains into a single tree for organizational purposes. A tree allows all domains to share a common schema, or design, and global catalog for better searchability.
Forests
Trees can be organized into forests, the highest hierarchy level in AD. A forest defines a single directory. For example, a business with trees of multiple domains established at various global locations can collect those trees into a single administrative forest, which represents the entire enterprise. A forest is also the top security boundary for AD, and no trust is established with any other forest unless that trust is explicitly created by admins of each different forest. Also, the admins have complete control over the data stored in the forest.
What is Active Directory Domain Services?
AD DS is the principal service within Active Directory. AD DS stores and manages information about users, services and other objects connected to the network -- while providing a central point of administration for all network activities. The servers that host AD DA are domain controllers and an organization can host multiple redundant DCs.
AD DS is so common and vital to Active Directory that discussions around AD typically refer to AD DS. However, Active Directory also provides the following suite of complementary services beyond AD DS:

- Active Directory Lightweight Directory Services (AD LDS). These provide a range of functionalities to simplify domain management, including a 32k database page format, new log database files to extend the AD schema, and object repair with missing core attributes.
- Active Directory Lightweight Directory Access Protocol (LDAP). This protocol facilitates communications between Microsoft Exchange Server and AD.
- Active Directory Certificate Services (AD CS). This Windows Server role manages digital certificates to bind identities and private keys for secure communication.
- Active Directory Federation Services (AD FS). This enables Federated Identity and Access Management across security boundaries and extends single sign-on (SSO) capabilities within a single security or enterprise boundary.
- Active Directory Rights Management Services (AD RMS). This Windows Server role provides on-premises Rights Management protection. It can be used with the cloud-based Azure Information Protection (AIP) for documents and emails that must be protected by an on-premises key.
A domain name is a text designation that maps to a corresponding IP address that identifies a network element. The domain name is the human-readable text, while the IP address is the precise network location. For example, the IP address of a company web server might appear as 192.0.2.2, but the domain name for the company appears as "mycompany.com." The domain name system (DNS) lets human-readable domain names be translated to corresponding IP addresses.
Managing servers might require admins to identify the server's fully qualified domain name (FQDN), which includes a server name and a domain name, such as "mail.mycompany.com." The FDQN for a Windows server can be located using the following steps:
- Open the Start menu and type "device name."
- Click the View Your PC Name menu.
- Select Advanced system settings.
- The "Full computer name" entry in the Computer Name tab should display the FQDN if appropriate.
Alternatively, start Windows Terminal and type the ipconfig /all command at the command prompt to display the complete Windows IP configuration, including the hostname, primary DNS suffix and connection-specific DNS suffix related to the computer.
Learn how the DNS name resolution process is essential for resolving hostnames, querying servers and locating IP addresses.






