NSX-T 2.4 could surpass NSX-V as VMware's primary SDN platform
VMware NSX-T now includes High Availability, a simplified UI and firewall updates. If it can provide your data center the same functionality as NSX-V, consider making the switch.
VMware's software-defined networking product NSX Data Center -- commonly known as NSX-T -- has nearly reached feature parity with NSX for vSphere -- called NSX-V. At this rate, NSX-T might outpace NSX-V to become VMware's primary SDN product. This could spell a major change for dedicated NSX-V users.
NSX-V integrates strictly with the vSphere Client using a plugin and the NSX Manager appliance. NSX-T connects vSphere Client to vCenter servers and ESXi hosts, but doesn't require integration for management purposes. NSX-T comes with its own management interface that enables you to manage your entire deployment, whether you use vCenter, KVM hypervisors or cloud-based or container-based systems.
If you're a new customer hoping to deploy NSX in your vSphere environment, you should consider whether NSX-T can provide the functionality you require for a vSphere deployment. If it can, you should implement that product over the dedicated vSphere counterpart.
Management and control plane integration, High Availability
NSX-T 2.4 now includes NSX Manager and controller nodes integrated into a single virtual appliance. You can deploy this app with three nodes, like you can with controllers in NSX-V, which means both the management and control planes offer High Availability.
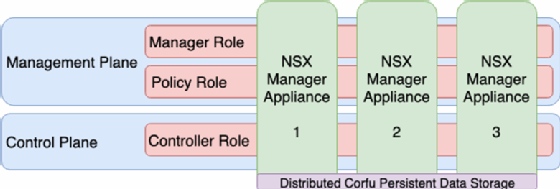
You can deploy the first NSX Manager appliance the normal way: as an OVA file from the vSphere Client for ESXi hosts or as a Qcow2 image for KVM-based hosts. You can then deploy the second and third appliances from the central management UI. NSX supports a maximum of three managers in production.
Simplified UI
You can use the HTML5-based UI to set up NSX.
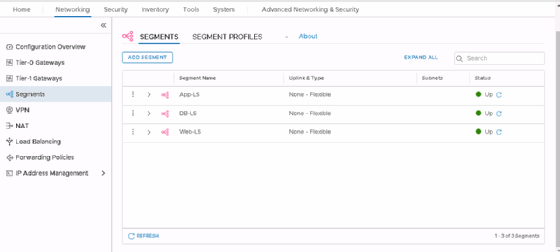
The UI features tabs for Home, Networking, Security, Inventory and Tools that belong to the simplified section of the client. Use this section for normal, day-to-day work.
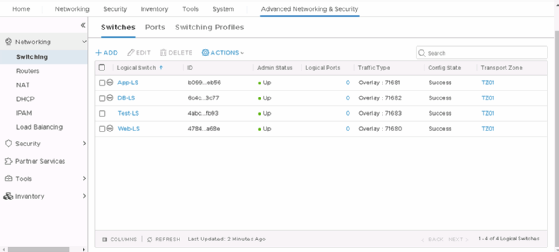
You can find additional tasks and tools, such as Traceflow, under the Advanced Networking & Security tab.
The Advanced Networking & Security section of the UI enables you to manage many of the same components as the simplified interface. However, keep in mind that anything you create in the advanced section -- such as a virtual network -- you must then manage from that section in the future.
New features in NSX-T 2.4
NSX-T 2.4 includes a Layer 7 application-aware firewall like the one included in NSX-V. The system enables the firewall to look into your traffic and identify a packet coming in over a specific port. The firewall can then determine whether that packet is Secure Shell traffic or anything else you would normally block based on its port number.
NSX-T 2.4 also includes Identity Firewall, a feature that alerts the system to which user logs into which VM and enforces firewall rules accordingly. VMware used the Guest Introspection model from NSX-V to create this feature. Identity Firewall combines with the Partner Service Insertion framework, which enables third-party vendors to integrate their products with NSX-T.
NSX-T 2.4 supports Internet Protocol version 6 (IPv6) in all routing tiers, which sets it apart from NSX-V. NSX-V's distributed logical router doesn't support IPv6 in any routing tier. However, NSX-T doesn't support Open Shortest Path First for dynamic routing, and only supports Border Gateway Protocol.
Making the switch
If you already use NSX-V but hope to switch to NSX-T with your networking configuration in place, you can use NSX-T Data Center Migration Coordinator. After starting the service on an NSX Manager node, you can access this utility from the system menu.
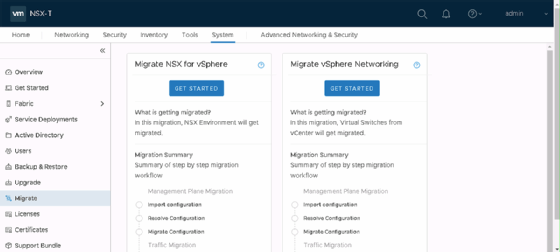
You should set up and configure your NSX-T environment before the migration. Certain configurations -- such as L2 bridges and any guest introspection or network introspection services -- don't migrate, so you must reinstall them on NSX-T.