
taa22 - stock.adobe.com
VMware network monitoring strategies for better performance
VMware network virtualization complicates how admins monitor network traffic. With best practices and monitoring tools, they can improve network performance.
VMware network monitoring enables IT administrators to examine traffic and make changes that improve performance. Admins who use best practices and monitoring tools to closely observe their network traffic can reduce vulnerabilities and inconsistencies.
This article covers ways to improve network traffic management and monitoring, such as host management services isolation and the use of VMware's packet capture utility. Admins can capture network packets both inside and outside the host with a virtual switch (vSwitch) to analyze traffic in VMware systems. But the variety of tools and configurations can make monitoring virtual networks difficult. Firewall protections, VMXNET3 network interface cards (NICs) and network monitoring tools can improve network performance and enhance monitoring strategies.
Monitor and analyze VM network traffic
Admins can run virtual networks with various rules and configurations that differ from those for physical networks, which complicates the task of network monitoring. For example, in VMware infrastructure where the internal ESXi vSwitch is virtualized, the port group security policy denies traffic capture that isn't addressed to a specific VM.
Admins can change the security policy at the vSwitch to enable promiscuous mode to capture traffic that's sent within the same ESXi host. But VMware considers promiscuous mode a security risk because a third-party monitoring software can capture network traffic from within the VM.
To avoid this vulnerability, enable promiscuous mode at the port group level, not at the vSwitch level. To do so, select a vSwitch, select the exact port group to monitor, change promiscuous mode to Accept and check the Override box.
Another option is to create a separate vSwitch specifically dedicated to monitoring.
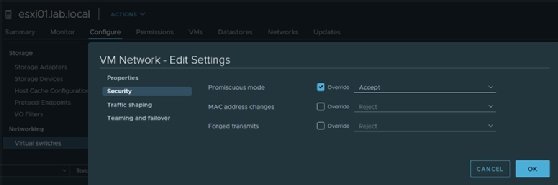
With promiscuous mode enabled, admins can capture network packets on a fully switched network and analyze traffic through network interface selection. To analyze packets only sent to VMs on the same host, enable promiscuous mode on the vSwitch.
Monitor network traffic outside the host
When admins monitor network traffic outside the host, packets travel to an upstream physical switch outside the virtual network. The physical switch must support mirroring network traffic to monitor outside the host. Different switch brands, such as Cisco, HPE or Netgear, implement network mirroring in different ways.
Packets are only sent to the switch port where the destination Media Access Control (MAC) address listens on the physical switch. Traffic mirroring uses promiscuous mode on the switch port, so the target switch port can receive all network traffic, not just the network traffic addressed to the associated MAC address.
VMware recommends admins create a dedicated vSwitch and port group to monitor network traffic external to the ESXi host. They can also configure the port group to monitor traffic limited to a specific virtual LAN (VLAN).
Configure the upstream physical switch port to span or mirror network traffic -- such as the VLAN or traffic that matches a specific MAC address range -- to a physical uplink NIC on the ESXi host. Attach the upstream NIC to a vSwitch and a port group used for monitoring purposes.
Network traffic management best practices
VMware recommends admins isolate networks used for host management and other VMware services, such as vSphere vMotion, to improve performance and security.
Admins should also control network I/O and use traffic shaping techniques, as well as dedicate a separate physical NIC for a group of VMs, to guarantee enough bandwidth for their workloads. Another practice involves creating several standard switches -- each attached to a particular set of NICs -- or using a single vSwitch with multiple port groups to execute specific network services.
Some setups can use firewall protection for VMs that route traffic between virtual networks with uplinks to physical networks, or virtual networks without uplinks, to ensure security.
Admins can also use the VMXNET3 NIC for optimal network performance. VMXNET3 is a virtualized 10 GB NIC that integrates device drivers and network processing with the ESXi hypervisor. This setup helps emulate hardware devices and improve network performance.
IT teams that use VMkernel network adapters to connect to a storage system should configure the network adapters with jumbo frames and a maximum transmission unit (MTU) of 9000 to optimize performance. It is a best practice to enforce consistent MTU configuration throughout the entire network chain.
Admins should also connect physical network adapters linked to the same vSphere standard switch or vSphere distributed switch to the physical network.
Tools for network monitoring
There are diverse tools to monitor network traffic in a VMware environment.
Admins can monitor and troubleshoot network connections and packets with VMware's pktcap-uw console utility, which is a built-in VMware ESXi utility accessible via the command line.
Tools such as Wireshark also enable admins to monitor network traffic at the VM level. Wireshark is a freeware utility with a GUI.
If the setup has a VMware vSphere Distributed Switch, Wireshark can analyze VM IP traffic that flows through the VMware vDS and send reports to a Cisco NetFlow collector.
Editor's note: This article was originally written in 2012 by Linux and virtualization expert Sander van Vugt. In 2021, consultant and vExpert Vladan Seget updated the article to reflect technology changes and include best practices.







