
hywards - Fotolia
How to integrate Active Directory and vCenter Server
Admins who connect AD with vCenter Server can grant users authorization for and access to VMs, storage and compute resources in vSphere. To do so, follow these configuration steps.
VMware's vCenter Server internal user database works fine for authentication out of the box, but larger VMware deployments can rely on configuration between vCenter Server and Active Directory to centrally manage the system.
VMware vCenter Server 7 is the latest version of VMware's management software for vSphere and ESXi. VCenter Server enables you to manage multiple remote data centers from a single location.
Built-in users, groups and roles come preconfigured when you first install vCenter Server. However, you can use Microsoft Active Directory (AD) as a source of identity for authentication purposes. With Active Directory integration, vCenter Server manages access to VMs, storage and compute in vSphere based on AD users and groups. Active Directory's login information supersedes the built-in VMware user login info.
A vCenter Server and AD integration requires you to follow a few configuration steps. You'll configure AD as an identity source and then assign users and applications with administrator privileges. With AD as an identity source, vCenter Server can pull all users and groups from AD and use them to log in to vSphere and access resources.
Configure vCenter Server with AD
Configuring vCenter Server to work with Active Directory requires a DNS server on the LAN, as well as AD up and running. You must have vCenter Server installed and log in with SSO administrator privileges. This is the account used when you first install vCenter Server.
You can then use vSphere via a centrally managed domain account within AD. This is convenient because you can share the connection URL to vCenter Server with your co-workers within the company, who will then be able to log in with their Windows session authentication without reentering their login and password combination.
Step-by-step tutorial
Once you log in to vCenter Server via an SSO administrator account, navigate to Home > Administration > Single Sign-On > Configuration > Identity provider. Click the Join AD link and follow the assistant.
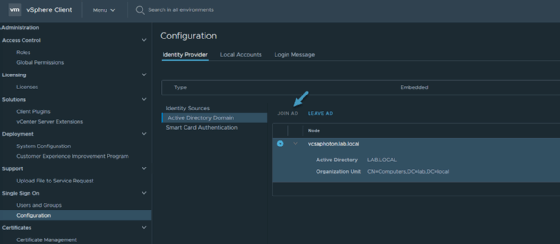
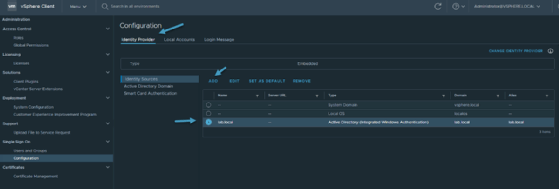
Reboot the vCenter Server Appliance for any changes to take effect. After reboot, navigate back to Home > Administration > Single Sign-On > Configuration > Identity provider and click Identity Sources. Here, add the domain you configured in the previous step.
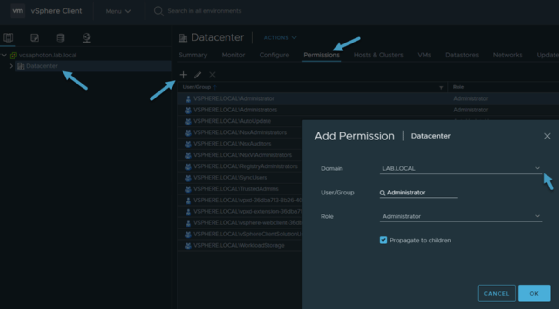
Then, assign permissions to the accounts you manage or access in the infrastructure. Navigate to the Datacenter tab in vCenter Server and click the Permissions tab to add authorized users and accounts to AD. Choose carefully which users can access which parts of the system, as well as the privileges they'll have.
Now, log in from a Windows computer attached to the Microsoft domain where you opened a session as an administrator.
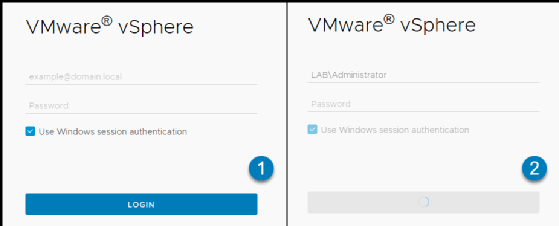
Verify if you successfully logged in as an AD administrator, checking the top right corner of your vSphere Client interface.
The login process works for users, as well as for administrator access. Add any users or groups from AD and give them access to VMs via the vSphere web client. Once AD integration with vCenter Server is configured, users and groups don't have to install additional software or remember other passwords to work with VMs.
Access control
You might want to restrict users' access to certain parts of the virtual infrastructure. To do so, select the folder where VMs reside and only grant users access to that specific folder. There are predefined roles in vCenter to choose from.
You might face a message that says you do not have enough rights to explore or modify certain parts of the virtual infrastructure. This occurs when the user requires elevated privileges to access an account. Log back in with an account that has appropriate privileges to make changes to the virtual infrastructure.






