
Andrea Danti - Fotolia
How does VMware secure boot protect VMs and ESXi hosts?
New to vSphere 6.5, the secure boot feature protects VMs and ESXi hosts from viruses, malware and spyware -- and enabling it is as easy as checking off a box.
The new VMware secure boot feature in vSphere 6.5 comes in two forms: secure boot for ESXi and secure boot for virtual machines. Secure boot for VMs only allows users to load signed drivers to a particular VM, which adds a layer of security against malware, viruses and spyware. Secure boot also prevents the startup of VMs with corrupted drivers. This is especially important in enterprise environments, in which data must be kept highly secure.
VMware secure boot for VMs
In order to use secure boot for VMs, the guest OS must support secure boot. If it doesn't, the boot process will stop and the VM won't boot. Fortunately, most modern OSes, including VMware Photon OS, Red Hat Enterprise Linux, Windows 8 or later and Windows Server 2012 or later, do support secure boot.
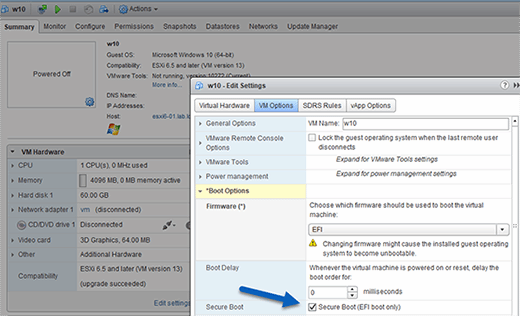
Before you can enable secure boot, make sure the VM is configured to run Extensible Firmware Interface (EFI) firmware. The VM must also run virtual hardware 13, also known as vmx-13, which is new to vSphere 6.5.
The vSphere Web Client detects OSes through the user interface; if your VM is running EFI firmware, the secure boot check box should also be visible. Click this box to enable secure boot.
VMware secure boot for ESXi
You can also enable VMware secure boot at the ESXi host level. Secure boot for ESXi uses Unified Extensible Firmware Interface (UEFI) firmware to validate the digital signature of the ESXi kernel against a digital certificate in the UEFI firmware. This ensures only a properly signed kernel boots.
ESXi is made up of digitally signed packages, called vSphere Installation Bundles. The ESXi file system maps to the content of these packages. During the boot process, the ESXi kernel checks each VIB against the UEFI firmware's digital certificate. This prevents ESXi hosts with unsigned kernels from booting.
If you enable secure boot for ESXi hosts, you won't be able to install unsigned code on ESXi, including unsigned drivers. This guarantees that secure boot only runs VMware digitally signed code with ESXi.








