How to ensure VDI network connectivity, security
A virtual desktop isn't worth a nickel if a user can't connect to it. Keep your VDI network strong with traffic prioritization and security policies.
When it comes to VDI, a strong network is your best friend. Before you deploy virtual desktops, consider how you're going to provide network-level traffic monitoring, troubleshooting, quality-of-service control, network infrastructure protection and secure access control.
First of all, you need a way to prioritize network traffic so the VDI network doesn't become overwhelmed. One way to test your network is to implement a pool of "road warrior" employees and use the information collected during that pilot to prioritize network traffic.
Many routers and switches contain the tools to prioritize VDI network traffic by type or TCP port number. However, you may wish to investigate bandwidth-optimization products that can reduce or even eliminate the need to purchase more network bandwidth, such as those from F5 Networks, Riverbed Technology, Citrix Systems, Blue Coat Systems and Zeus Technology.
Nonetheless, it's critical to manage user expectations. Although VDI vendors offer customers ways to tune protocols, and the network vendors provide ways to optimize bandwidth, the reality is that networks cannot break the laws of physics. One benefit of a virtual desktop infrastructure is the ability to dynamically monitor latency in real time. These systems give the people who manage the virtual desktop environment timely notifications of potentially disruptive latency.
Checking for VDI network connectivity
Products for bandwidth optimization often come with templates and plug-ins that make it easy to set up and configure an appliance to offer load-balancing capabilities. They may also add more "intelligence" around the availability of your virtual desktop infrastructure. Once end users connect to their virtual desktops via one of these network appliances, the appliances become the ultimate arbiters over which brokers or security servers the users connect to.
For example, F5 Networks' BIG-IP Appliance comes with the iApp plug-in to check for network connectivity. You can download and configure the plug-in for use with VMware View. Admins can then query the status of both the security server and connection server roles. If they find that the security server or connection server is unavailable, their appliance, with the intelligence from iApp, can redirect the end user to servers that are available.
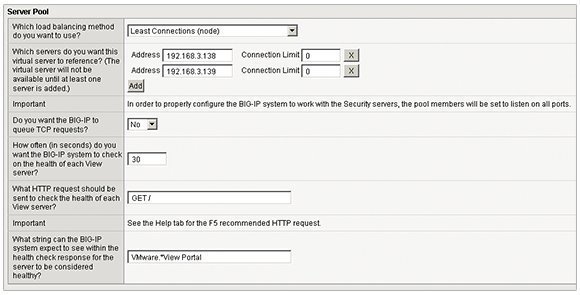
In Figure 1, the iApp controls in F5's BIG-IP allow the administrator to be aware of the security server and to set a time-out value to check the server's health status. The iApp does this by sending a connection query to the HTTP portal available on the VMware View infrastructure with the string of "VMware. *View Portal". If the security server and connection servers respond positively to this query, then the system knows they are up and available.
If there isn't a valid response to this VDI network connectivity query, then clients are redirected to a fully available View system. This conditional statement checks whether both the security server and its paired connection server are available before the redirect occurs.
Don't forget VDI network security
A mixed desktop environment requires proper security policies and services to protect the client and network infrastructures. Both server-based computing and virtual desktops introduce immense security vulnerabilities because they offer a graphically rich endpoint with access to the rest of the corporate network.
Since the weakest link in virtual desktop security is always the user, you should institute aggressive password policies. Require users to reset their passwords more frequently, and specify that passwords should follow a certain level of complexity.
More on VDI network connectivity
Guide to VDI network management
How to prepare your network for VDI
Pros and cons of offline VDI
Sadly, tight security can easily lead to end users writing their passwords on sticky notes, for instance. Many organizations have mandated two-factor authentication in the form of technologies such as RSA SecurID, SafeWord or smart cards. Those who work in government, for example, may have to integrate these security technologies into their virtual desktop strategies. Not all virtualization vendors, however, support the full range of two-factor authentication systems.
Remember that security begins at home, so use the VDI vendor's network diagrams to map out the communication paths used at every step, and then apply software- and network-hardening policies to the firewall, broker and desktop to reduce their overall attack surface area.
For added security, you should also ensure that a rigorous set of desktop policies is applied. A simple approach is to use your existing commitment to Microsoft Active Directory Group Policy Objects, or your organization can invest in tools that plug the holes that typify the Microsoft Windows client operating system.
Adopting an app virtualization-first policy is another way to reduce the amount of installed software on the desktop, which can cause VDI security issues. In addition to reducing application conflicts, this policy reduces the number of user-mode applications that hackers can hijack.