Andrea Danti - Fotolia
SoftNAS Cloud users get security fix for vulnerability
SoftNAS says a web server and load balancer component it added to strengthen security for its Cloud NAS actually could enable unauthorized access to the web admin interface.
SoftNAS Cloud NAS customers need to install a security fix to patch a vulnerability a security firm discovered in versions 4.2.0 and 4.2.1 of the software-defined storage product.
Digital Defense, a San Antonio-based security firm, notified SoftNAS in January that an attacker could gain access to the web administration interface without valid user credentials and add users or execute arbitrary commands. SoftNAS issued a security fix with its 4.2.2 product update on March 12.
Jeff Russo, senior vice president of products at SoftNAS, based in Houston, said the company wouldn't label the security update as critical. He said customers are only vulnerable if they exposed SoftNAS StorageCenter ports directly to the internet by not following best practices.
But Marc Staimer, president of Dragon Slayer Consulting in Beaverton, Ore., urged customers to install the update as soon as possible, because bad actors could try to exploit the vulnerability after Digital Defense and SoftNAS disclosed it this week.
"Every time a patch comes out, they know that people tend to not implement the patches quickly," Staimer said. "That means a lot of implementations are vulnerable, and they're going to go after it."
Second vulnerability since July
Security companies have flagged SoftNAS twice for vulnerabilities in less than a year. Last July, Core Security -- now part of HelpSystems, based in Eden Prairie, Minn. -- identified a command-injection vulnerability in SoftNAS Cloud versions prior to 4.0.3. Core Security said the vulnerability in the web administration console could allow an unauthenticated attacker to execute arbitrary commands with root permissions.
Russo said, although the two vulnerabilities affected the web administration console, they were different in nature. He said the latest vulnerability relates to an open source NGINX web server and load balancer component that SoftNAS recently added. Interestingly, he said, one reason SoftNAS added the NGINX component was to improve security.
"It was essentially a bug with the way it was integrated," Russo said. "It's not something that would have been easily detected by most people. It just happens that Digital Defense has a great deal of knowledge about the NGINX component and was able to identify this issue."
Digital Defense said the SoftNAS Cloud NGINX default configuration file has a check to verify the status of a user cookie. If the check isn't set, the user gets redirected to the login page. An arbitrary value could be provided for the cookie to access the web interface without valid user credentials, according to Digital Defense.
Potentially serious vulnerability
"We feel it's fairly serious, because there aren't a lot of mitigating factors," said Mike Cotton, vice president of research and development at Digital Defense. "If you can send a ping packet at the device or access the administration interface over the network, you can exploit it."
Cotton said the SoftNAS Cloud session management code wasn't verifying the existence of a valid session, but merely checking, via the cookie, that any session key existed. That provided a way to get remote administrator access without credentials.
Customers must log into their AWS or Microsoft Azure platform account to launch a new instance of SoftNAS Cloud. Best practices call for accessing SoftNAS through a virtual private network connection to the virtual network where the SoftNAS Cloud instance lives, said John Yeazell, director of quality assurance at SoftNAS.
Once connected, Yeazell said, a customer would point a browser to the SoftNAS instance, or virtual machine, via an HTTPS session to manage it. Users access, configure and manage the virtual appliance through the SoftNAS user interface, StorageCenter or the command-line interface -- not via AWS or Azure.
"If end users choose to make the appliance accessible via a public port, they should follow the platform's best practices to lock down" the IP connection, Yeazell said.
Russo said SoftNAS worked with Digital Defense on the security fix and hasn't had any customers report exploits or breaches related to the vulnerabilities Core Security and Digital Defense discovered. SoftNAS patched the July vulnerability in its 4.0.3 product release. The 4.2.2 update that SoftNAS released on March 12 fixes the 4.2.0 and 4.2.1 product versions that have been out since Nov. 15.
Digital Defense notified SoftNAS about the vulnerability in January, in keeping with its responsible disclosure possibility, and it published its findings once the patch became available. Digital Defense has exposed other vendors' vulnerabilities in the past, including one for Dell EMC last year.
Digital Defense's business model is to perform vulnerability assessment and penetration tests, typically for customers in regulated industries, such as financial services. Cotton said the company's research team generally takes a hard look at backup and NAS devices and flagged SoftNAS as a device they were seeing and wanted to check.
Cotton estimated no more than 100 of Digital Defense's roughly 4,000 customers use SoftNAS Cloud, and he isn't aware of any clients that suffered an adverse effect related to the vulnerability.
Disruptive update
The SoftNAS Cloud 4.2.2 update requires a reboot, so customers must plan for disruption, Yeazell said. Customers with a high-availability configuration could maintain uptime, he said, but best IT infrastructure practices recommend users plot out a maintenance window.
SoftNAS claims about 300 known customers and 7,000 deployments. But it has no count or contact information for the users that acquire the software through the AWS and Azure marketplaces, according to Yolande Yip, the company's director of marketing.
Yip said the only mechanism to notify or alert those customers about security vulnerabilities or product updates is AWS-generated email sent to current subscribers on behalf of SoftNAS. Those communications go through the AWS approval process, and SoftNAS isn't privy to identifying information or the number of email messages, she said.
SoftNAS customers also have the option to manually check for updates by opening "settings" through the user interface and clicking "software updates." The wizard shows the version the customer is running and the latest available version.
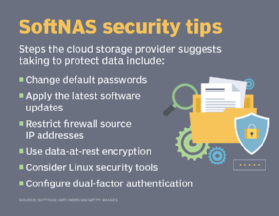
Staimer said every software company has a responsibility to know who uses their products, so it can inform them about security vulnerabilities and other issues requiring their attention. He said more cloud-based storage and compute providers are adding Multifactor authentication -- such as text messages to mobile phones and biometrics -- to prevent unauthorized access.
"Every product has vulnerabilities. It's how the company deals with them that matters," Staimer said.
Yeazell said SoftNAS offers a dual authentication option, where the user would first authenticate with SoftNAS and then authenticate using Google or Facebook credentials. He said stricter multifactor authentication options are on the product roadmap.