Illustrated guide to containerization security
Container security concerns are keeping IT pros up at night. Discover why and what they're doing to secure containers as well as the applications and data that run within them.
Containers have gained in popularity as a means of virtually packaging and isolating applications for deployment. With this increase in adoption has come a greater awareness of containerization security.
The roots of container technology go back to the 1960s and 1970s with partitioning and Linux chroot process isolation. Google introduced Borg container cluster management in the early 2000s, but it wasn't until the advent of Linux container technology and application containerization through the likes of Docker and Kubernetes that modern containerization took shape.
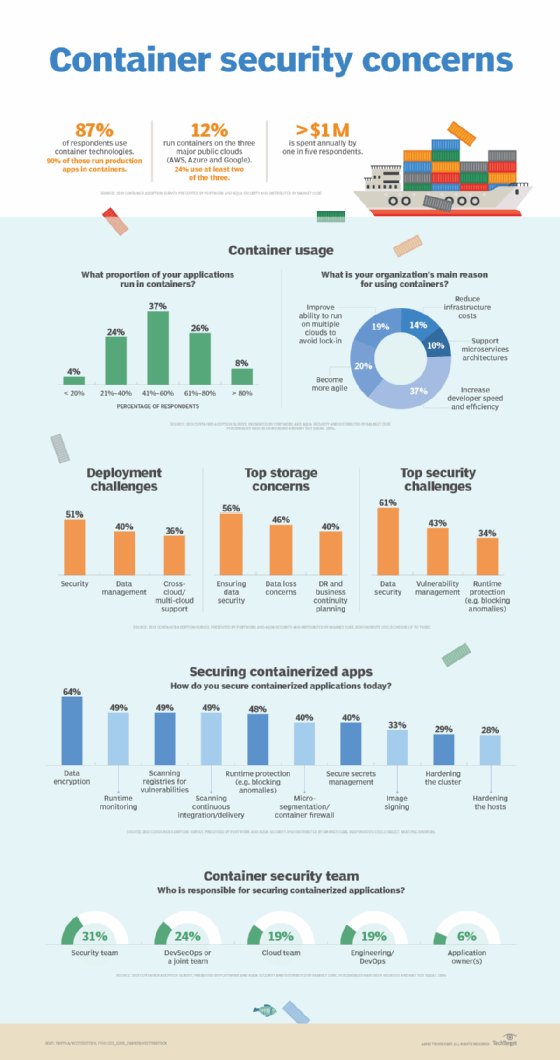
Today, containers are a mainstream alternative to VMs and physical servers, as they deliver greater agility and flexibility than virtual and physical hardware stacks. According to the 2019 Container Adoption Survey from Portworx and Aqua Security distributed by Market Cube, 87% of the 501 IT pros surveyed run container technologies, an increase of 32 percentage points from two years earlier.
Just over 50% of respondents said their main challenge is containerization security, while concerns about data protection and loss as well as DR and business continuity topped storage concerns.