LUN masking
What is LUN masking?
LUN masking is an authorization mechanism used in storage area networks (SANs) to make LUNs available to some hosts but unavailable to other hosts. LUN masking is typically implemented at the host bus adapter (HBA) level on the servers accessing the SAN's storage systems, although some storage controllers also support LUN masking. When LUN masking is configured, a host can see only the LUNs that have been assigned to that host and cannot see or access any other LUNs.
A logical unit number (LUN) is a unique identifier that is used when allocating physical storage. A LUN can reference an entire RAID group, a single drive or partition, or multiple drives or partitions. A LUN is used by a transport protocol associated with an SCSI, iSCSI, Fibre Channel (FC) or similar interface. LUNs are central to the management of block storage arrays shared over a SAN.
Without LUN masking, a host connected to a SAN can see all available LUNs and, in some cases, take actions that might not be desired. For example, a Windows server might inadvertently corrupt non-Windows storage by trying to write volume labels to them. LUN masking makes it possible to prevent the server from accessing or even seeing those non-Windows LUNs.
LUN masking subdivides access to a given port. Then, even if multiple LUNs are available through the same port, the LUN masks can be set to limit the host's access to specific LUNs. For example, the following illustration shows a storage device with four available LUNs and two hosts, each configured with an HBA.
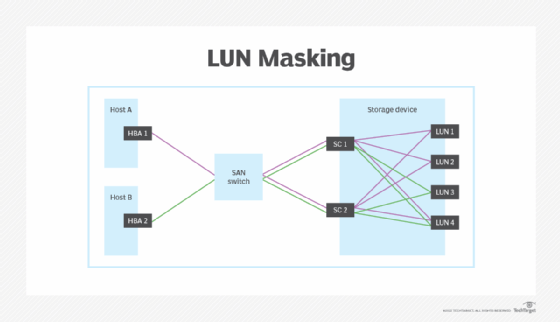
Host A contains HBA 1 and Host B contains HBA 2. Each HBA connects to the SAN switch, which in turn connects to the two storage controllers (SC 1 and SC 2). Without masking, both HBAs would have access to all four LUNs. In this case, however, LUN masking has been applied at the HBA level so that Host A can access only LUN 1, LUN 2 and LUN 4, and Host B can access only LUN 3 and LUN 4.
LUN masking can be a useful tool for controlling server access to specific LUNs, but it offers only limited security protection because it is still possible for the HBAs to be compromised, leaving the SAN infrastructure vulnerable. For this reason, most SAN deployments also implement zoning and other mechanisms to provide additional levels of protection, relying on LUN masking primarily to protect against potential server issues.
See also: Advantages and disadvantages of using a SAN, SAN vs. NAS: What are the key differences?, SAN and NAS: An illustrated guide to distinguishing the storage types and The advantages of SAN technology in an HCI world.