
Getty Images
What are 3 best practices for storage encryption at rest?
Consider the fine print of encrypting data at rest. For example, access control permissions can make or break a storage encryption plan.
Encryption is one of the most fundamental practices for keeping data secure. However, there is more to using storage encryption than just its enablement.
Here are three best practices for working with storage encryption at rest.
Review access control permissions
Regularly review the access control permissions for data. Although this best practice might seem to have little to do with storage encryption at rest, there is a reason for its inclusion here. Excessively permissive access control policies can undermine the security benefits gained with storage encryption.
If access policies grant everyone -- including unauthenticated users -- access to the data, then encryption becomes meaningless.
Standardize the method of storage encryption
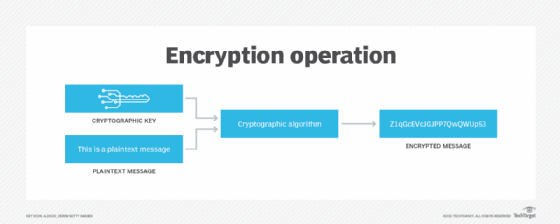
It's a good idea to use a single type of encryption algorithm for all data -- although there may sometimes be logistical constraints that make this impossible. Using one type of storage encryption at rest can help to simplify both key management and storage management.
At the same time, it is important to evaluate storage performance, both before and after the encryption. Every encryption algorithm carries a certain amount of overhead. This overhead doesn't just come into play during the initial encryption process, but also during normal, day-to-day read operations.
Remember, data must be decrypted in order to be read. This concept applies to everything from a user opening a file to a backup application that needs to protect newly created data. As such, pick an algorithm for storage encryption at rest that balances security with performance.
It's also a good idea to encrypt all data so that everything is protected, regardless of its sensitivity. This will prevent a situation in which the organization has accidentally left sensitive data unencrypted. However, there are some data types that organizations cannot safely encrypt.
Protect encryption keys
Protect encryption keys both against attack and loss. An attacker who gains access to encryption keys is able to read encrypted data. Similarly, if those same keys are lost or destroyed, then the organization loses the ability to access its own data. The data remains in a permanently encrypted state, and the organization can't decrypt it.








