
Sikov - stock.adobe.com
Hydra password-cracking tool: How to download and use it for good
Ethical hackers, need help brute forcing passwords? Learn how to download and use the open source Hydra password-cracking tool with this step-by-step tutorial and companion video.
Red teams and blue teams inevitably face situations where they need to brute force a password. In offensive scenarios, red teams compromise weak passwords to gain unauthorized access. In defensive scenarios, blue teams might need to find and flag weak user passwords to help their organization conduct an audit, uncover default passwords in use, scan for bad user passwords in automated password attacks as a control, or test detection capabilities and defenses during attack simulations.
Regardless of the scenario, knowing how to successfully conduct these attacks is a valuable skill for ethical hackers -- as is knowing how to use the popular brute-force tool Hydra.
What is Hydra?
Hydra is an open source, password brute-forcing tool designed around flexibility and high performance in online brute-force attacks. Online brute force refers to brute forcing used in online network protocols, such as SSH, Remote Desktop Protocol (RDP) and HTTP (e.g., HTTP basic authentication), as well as on HTML forms. Hydra provides brute-forcing capabilities for these protocols and situations and numerous others. It was designed to be parallelized, meaning multiple threads can operate in parallel to optimize efficiency and speed up the brute-forcing process.
Offline password cracking, such as using an automated tool to try to crack a Windows Security Account Manager database or the contents of a Linux password shadow file (i.e., /etc/shadow), requires different tools, such as hashcat or John the Ripper.
How to download Hydra
There are a few different ways to obtain and use Hydra:
- Download it, and build it yourself from source.
- Pull it down in a docker container (docker pull vanhauser/hydra).
- Find it preconfigured in most penetration testing Linux distributions, including Kali, Parrot and BlackArch.
Extensive Hydra documentation is available online. Note, some sources call the tool THC Hydra in reference to the hacking group THC that developed the tool. For this article, we refer to it as just Hydra in keeping with the tool's documentation.
How to use Hydra
While an extremely powerful tool, the Hydra interface is both simple and intuitive. In general, only three pieces of information need to be supplied to Hydra:
- The username(s) to use during the brute-force attack.
- The password.
- The remote resource to be attacked.
In its simplest incarnation, use the -l (lowercase L) option to specify a single user account to try and the -p option to specify a specific password, as well as the protocol and address of the resource. In the example below, the -l flag indicates a specific user, -p indicates a specific password and the URL ssh://localhost to cause it to test the local machine.
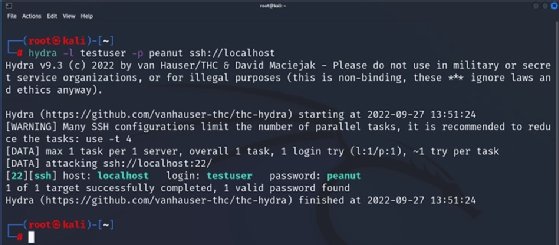
This is a contrived example; in fact, it's not much of a brute force at all because we've specified exactly one username and exactly one password. For a more realistic usage scenario, specify multiple usernames and/or multiple passwords.
Attempted passwords are typically specified in a wordlist. In cybersecurity, a wordlist refers to a collection of words and phrases commonly used for passwords. Wordlists can be found in multiple areas. By default, Kali and other pen testing distributions come with one or more wordlists to use in tests like this. For certain types of attacks, such as credential stuffing, lists can be found in other channels, such as dumps or other artifacts disclosed to public sources from prior breaches.
To use a wordlist in Hydra, use -P followed by the location of a wordlist, as shown in Figure 2. Likewise, to attempt to brute force more than one username, specify a file of usernames by using -L instead of the -l flag.
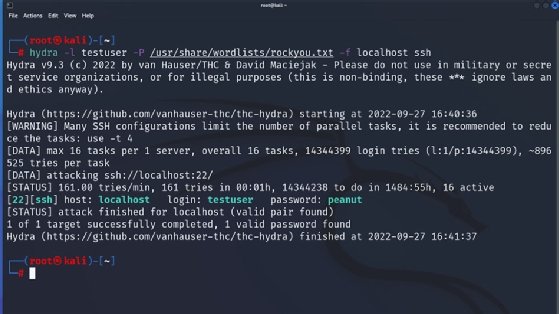
Figure 2 uses the -P option to specify the rockyou.txt wordlist -- a popular choice for brute-force attacks due to its thoroughness. It also specifies the -f option, which causes Hydra to stop when it discovers the first username/password combination. Note, if multiple hosts are specified, -f functions per host, while -F is first hit for any host. The example above also changes the format of the protocol/host combination. Instead of specifying the host and schema (protocol) in URL format (i.e., ssh://localhost), it instead specifies the protocol and host separately.
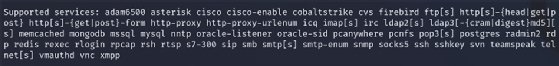
One of the great things about Hydra is its flexibility; it supports a wide range of protocols and services, a list of which can be found in the manual page -- man hydra from the command line. Note, support for some protocols needs to be compiled in. To determine what protocols and services are supported by your installation, execute the command hydra -- without arguments -- to obtain a list. Figure 3 shows what appears when running the Hydra command without arguments on a vanilla Kali installation.
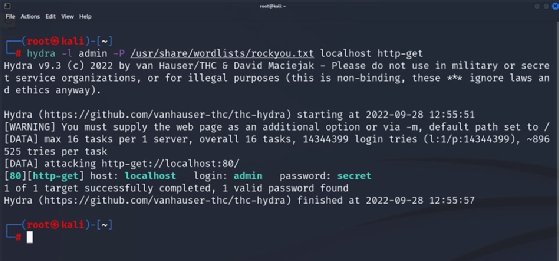
Hydra can be used to not only brute force against commonly used network protocols, such as SSH, FTP and RDP, but also to conduct brute-force attacks against web applications. Figure 4 illustrates use of the tool against a web server using HTTP basic authentication.
For a slightly more advanced example of an authentication using HTTP forms, view the following companion video for this article.
How to use xHydra
XHydra is a GUI for Hydra. Instead of specifying the various switches and flags on the command line, users select the appropriate configuration from a series of controls via the GUI.
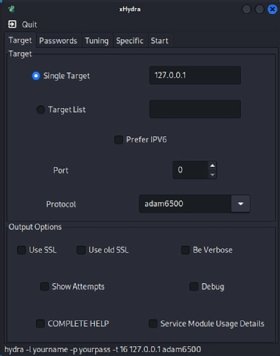
Wrapping up
Hydra is a great addition to any cybersecurity practitioner's toolkit. Red and blue teams both benefit -- offensive teams from being able to gain access to resources and defensive teams to advance security posture -- for example, as a detective control for bad passwords, to exercise alert capabilities and more.
The tool provides a powerful yet simple interface that enables users to get tremendous bang for their buck. And the best part is that the bang is completely free.
Editor's note: It is possible to use Hydra both lawfully and unlawfully. It is up to you to ensure your usage is lawful. Get appropriate permission and approval before performing brute-force attacks, and handle the information obtained ethically. If you are unsure whether your usage is lawful, do not proceed until you have confirmed that it is -- for example, by discussing and validating your planned usage with your organization's counsel.
This article was updated in June 2025 to improve the reader experience.
Ed Moyle is a technical writer with more than 25 years of experience in information security. He is currently the CISO at Drake Software.









