
Getty Images/iStockphoto
How to disable removable media access with Group Policy
Removable media can pose serious security problems. But there is a way to control who has access to optical disks and USB drives through Windows' Active Directory.
Even in today's cloud-based environments, USB drives are a useful tool. Removable media can perform a variety of tasks, among them quick transfers between systems on different networks or moving installation and configuration files to air-gapped networks. Optical media, such as CDs and DVDs, are also still found in some networks.
For all their versatility, removable media pose a management challenge. For many organizations, finding ways to disable removable media is a necessity. A big worry is how to manage the content entering the network. Drives and disks can house threats and malware, any of which can devastate infrastructure. And, because removable media bypass security guardrails, such as firewalls and intrusion detection systems, malware can be easily transferred onto the network.
Removable media are also a source of data exfiltration, which can be equally difficult to mitigate. Users could innocently copy confidential data to a drive so they can work on projects at home. If the drive is lost, the data is exposed.
Security awareness training can help manage these threats, but its effectiveness is limited. Company-issued media could help separate personal and business data, but that option isn't helpful either. Nor is a blanket policy that attempts to block employees from using removable media; some users could have a legitimate need for removable drives and disks, and others could simply not follow the policy.
Active Directory (AD) Group Policy can help organizations effectively manage removable media. Read on to learn how.
How Group Policy works
Group Policy is an essential management tool for AD administrators that offers thousands of settings, from password management and application deployment to desktop configurations, that can be applied to AD domain members.
Group Policy's scope is broad. Administrators can link policies to the entire domain -- consisting of all domain members -- or to specific organizational units (OUs) within the domain. Policies are not associated with groups, a departure for many administrators used to controlling resources via groups. Instead, administrators may define OUs for departments, locations within the facility, geographic regions or any other association that makes sense.
Group Policy configurations and scopes must be designed carefully to ensure correct policies cover the correct users and systems. Document ahead of time which users should or should not have access to removable media, and determine which computers require removable media restrictions. Understanding these requirements is critical.
Configuration options
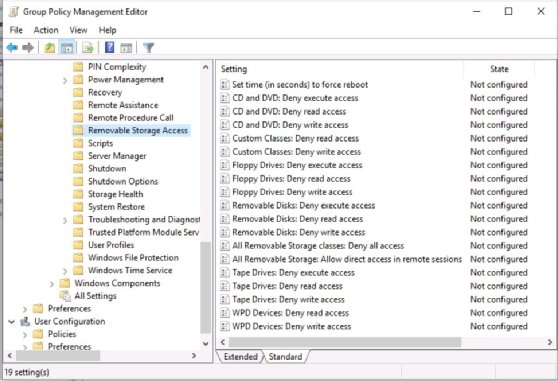
To design the strategy that best works for your operation, first, browse to the removable media settings in Group Policy. On a domain controller or another system with AD administrative tools, open Group Policy Management Console. Create or open a Group Policy Object (GPO), and browse the following nodes to show the available settings: Computers Configuration > Policies > Administrative Template > System > Removable Storage Access.
Find the entries related to specific types of removable media. Choices include optical drives (CD/DVDs), tape drives and floppy drives. USB drives are categorized as removable disks.
How to create and implement your policy
Now that you know your configuration options and what your company's security requirements are, it's time to create a policy that reflects these choices. The steps include creating a new policy, setting the configurations and linking the policy to the domain or various OUs.
First, create a new GPO. It's a good practice to use a specific policy to describe a specific configuration rather than try to maintain policies that contain a variety of unrelated settings. Give your new GPO a name that describes its purpose.

GPOs contain two primary nodes: User Configuration and Computer Configuration. The difference is in whether the policy applies to a user regardless of the computer they log on to or if it applies to the computer regardless of the user logged on. This example assumes Computer Configuration.
To edit the new GPO, right-click in Group Policy Management Editor, select Edit, and browse to Computers Configuration > Policies > Administrative Template > System > Removable Storage Access.
Group Policy Management Editor displays the available settings. You can set controls for CD/DVD drives, floppy disks, removable disks (USB drives), tape drives and custom classes of disks.
Define the settings based on your organization's security policy and design. Select the media types to control -- there are probably several. Each setting includes Enable, Disable and Not Configured options. In most cases, Enable the setting to enforce the desired configuration. I strongly recommend annotating the Comment field with the reason behind the setting and its scope. These comments help future administrators -- or even yourself -- understand why this policy exists and to what it applies.
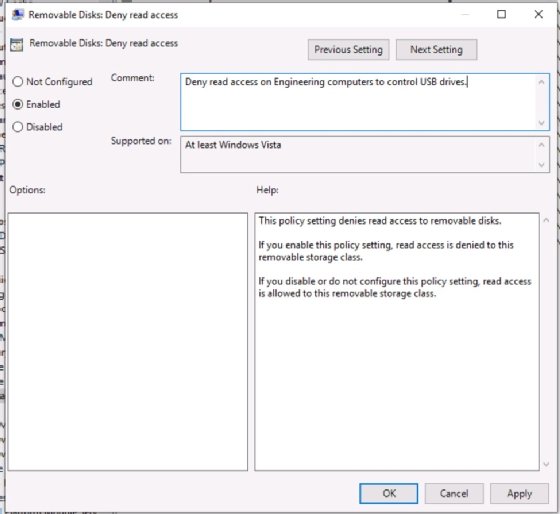
Once the GPO is created, it has to be applied. GPOs can only be linked to the domain or OUs. Suppose your security policy specifies that computers in the engineering department have their USB and CD/DVD drives disabled. Link your policy to the engineering OU. In AD, that OU should already house the engineering department employees' user accounts, as well as the accounts for the computers issued to that department. Group Policy applies the settings after it refreshes.
To link the GPO, right-click the OU, and select Link an Existing GPO. Browse to your new GPO, and select it.

In some cases, you might want to exempt certain members of the OU from the Group Policy settings. AD cannot link GPOs to individual users or groups, but there is a way to achieve a similar effect. GPOs are essentially text files, and you already know how to control access to text files in Windows – New Technology File System (NTFS) permissions. Set a Deny permission on the GPO specific to the user(s) or group(s) you want to exempt from the settings. Because the account isn't allowed to read the GPO, the policy won't apply.
Be careful when using NTFS permissions to control the application of Group Policy. The feature is difficult to document and troubleshoot, and it can lead to confusion quickly.
When do the settings take effect?
Domain members communicate with domain controllers every 90 minutes to check for updated policy settings, so you could wait for your changes to propagate based on this schedule. If you're troubleshooting Group Policy, manually refresh Group Policy settings by using the gpupdate /force command. Rebooting the system also causes it to check in with the domain controller for new settings. Beginning with Windows Server 2012, you can remotely force Group Policy updates from the domain controller. Once the system refreshes the policy, access to removable media is restricted.

Group Policy has a variety of useful security configuration options -- this article only touches on one. By locking down removable media options for secure workstations, you can help prevent inbound malware and manage outbound data leakage. These settings can be combined with many others to help mitigate security threats. This is just one more way AD administrators can harness Group Policy to disable removable media and keep their operations secure.







