
Getty Images/iStockphoto
How to configure sudo privilege and access control settings
Learn how to use the sudo command for access control configurations, from granting full administrative privileges to delegating roles.
Network system resources and data are protected by such measures as applying the principle of least privilege and disabling root access, but administrators still need privileged access to make system configuration changes and other modifications.
Enter sudo.
Sudo, short for superuser do, lets users exercise specific delegated privileges, such as editing configuration files or updating software. System administrators can define exactly what commands individual users or groups can execute by editing the /etc/sudoers file.
This article provides specific and common real-world sudo configurations. It begins with delegating full administrative privileges before covering more focused access controls. There are a few tips at the end, too.
How to configure sudo
Using the visudo command to edit the /etc/sudoers file is critical. The command verifies the file's syntax before saving changes, helping prevent administrators -- or the system itself -- from being locked out in the event of a typo or other misconfiguration in the file. Here is an example of the visudo command in use:
~$ sudo visudo
Once granted sudo privileges, users use their delegated abilities by placing the sudo command before privileged commands. For example, type the following command to add a user to the system, assuming your identity is granted this ability in /etc/sudoers:
$ sudo useradd joe
The system prompts you to enter your password.
The following is the syntax for entries in the /etc/sudoers file:
[username] [hostname]=(run-as-user:run-as-group) [commands]
Here are the various elements explained:
- [username] specifies which user privileges are granted to.
- [hostname] specifies which host the user can access.
- (run-as-user) specifies which accounts the user can switch to.
- (run-as-group) specifies which groups the user can switch to.
- [commands] specifies which commands the user can run.
To grant an account named max the ability to run the useradd command on any system, type the following:
max ALL=/usr/sbin/useradd
Users can check their sudo privileges using the -l or --l (list) switch.
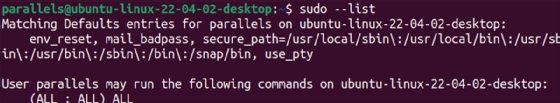
How to add a user to the administrative group
A common use of sudo is to grant system administrator privileges to a specific user. This user can usually run any command on the system. Distributions derived from Red Hat Enterprise Linux typically use the wheel group for administrative control, while Debian-derived distros rely on the sudo group.
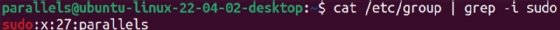
Delegating admin control involves adding the user to one of those groups:
- On Debian, Ubuntu or similar distros, enter # usermod -aG sudo max.
- On Red Hat and similar distros, type # usermod -aG wheel max.
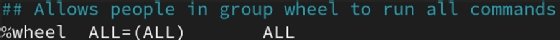
With this group membership, the user can add sudo before any command, enter the password associated with the max account and run the command successfully.
Be aware of how privileged this delegation is. Members of wheel or sudo groups can run any command on the system. Consider this in the context of the principle of least privilege. It might be better to delegate more limited and specific commands than all commands.
How to grant full administrative privileges
Admins can explicitly grant all privileges without managing wheel or sudo group memberships. To do so, enter the following line in the /etc/sudoers file:
max ALL=(ALL) ALL
Don't forget to use visudo to edit the file.
How to delegate one role to one user
Sometimes, admins need to delegate a single privilege to a user, such as maintaining software via a package manager.
Add this line to /etc/sudoers to grant privileges to the apt command:
max ALL=(ALL) /usr/bin/apt

To do the same on distros that use DNF, type the following:
max ALL=(ALL) /usr/bin/dnf
Note that you should include the absolute path to the executable.
How to grant privileges to several users
If you need to delegate privileges to multiple users, you can do this within the /etc/sudoers file by setting a user account list alias before entering a line to delegate access:
- Set a User_Alias to specify the users who should be delegated access to run the command.
- Enter a command access line.
Here are the steps in more detail.
First, define the User_Alias in the file. For example, set an alias named APPS that includes users max and cindy:
User_Alias APPS = max, cindy

If you already have an apps group on the system in the /etc/group file, specify it with %apps. The leading % tells sudo to check for regular Linux groups.
Next, grant access to the apt command to the APPS alias:
APPS ALL=(ALL) /usr/bin/apt

Note, there is an added a comment to explain this special configuration.
Use a similar entry for the DNF package manager on Red Hat-based systems.
How to grant one user several privileges
The previous example demonstrated setting an alias to represent multiple users. This example involves an alias to set multiple commands. Bundle the commands using the alias, and then grant access to a user or group to the bundle:
- Set a Cmnd_Alias to specify the commands to associate together.
- Enter a command access line for the bundle.
The syntax looks like this:
Cmnd_Alias CMD=/absolute/path/cmd1, /absolute/path/cmd2
Here's an example using a command alias named SOFTWARE:
Cmnd_Alias SOFTWARE = /usr/bin/dnf, /usr/bin/yum, /usr/bin/rpm
Now, you can delegate the software privilege to one or more users:
max ALL=(ALL) SOFTWARE
Combine the User_Alias and Cmnd_Alias settings to simplify delegating multiple commands to several users.
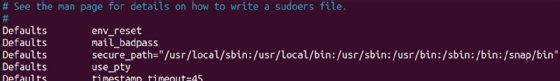
Some distributions include prewritten Cmnd_Alias examples you can uncomment to use. For instance, my Fedora 38 installation includes the following to manage storage and access control.
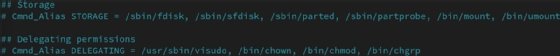
Other useful sudo tricks
There are many ways to configure sudo to manage exactly the delegations you need on the system. Here are a few useful tips for using sudo to get you started.
Use command history
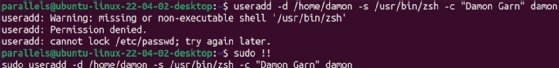
I regularly forget to use sudo. I've just never gotten used to it. As a result, I often type long commands that fail because I didn't elevate my privileges. Don't forget the value of Bash's history feature. It keeps track of your commands. Use !! to repeat your most recent command. Combine this with sudo to repeat a command with other privileges. This command generates a permission denied message:
$ useradd -d /home/damon -s /usr/bin/zsh -c "damon garn" damon
Repeat the command using sudo and command history:
$ sudo !!
Modify timeouts
Sudo caches your updated privileges for a short time, measured in minutes. Manage that time in the /etc/sudoers file. Beware that longer caches increase convenience and security risks.
To set the timeout value for user max to 45 minutes, type the following:
Defaults max: timestamp_timeout=45
To set the timeout for all users to 45 minutes, modify the following line:
Defaults: timestamp_timeout=45
Remove the password prompt
A more dangerous entry is setting /etc/sudoers to not challenge a user for a password when using sudo. Only use this on lab or test systems not connected to the network.
The following example indicates max does not need to enter a password for any commands run via sudo:
max ALL = (ALL) NOPASSWD:ALL

These are just a few examples of sudo configurations. Remember: It's essential to use visudo when editing /etc/sudoers because it confirms the file's syntax. Misconfiguration in /etc/sudoers can reduce or eliminate access to the system.
Plan ahead when configuring complex sudo configurations. Consider grouping users within /etc/sudoers or /etc/group to simplify delegation of control. Use Cmnd_Alias settings to associate related sudo commands. Package manager commands are a great example.
Consider extending the sudo timeout to make access more convenient. Make sure you don't violate any security requirements. Be extremely careful when setting the NOPASSWD option.
Examine your current sudo configuration today, and use these tips to make your systems more secure and convenient.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides, including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to TechTarget Editorial and CompTIA Blogs.






