
Where to place a firewall in an enterprise network
Firewalls are a foundational element of a strong security posture, and their positioning affects both enterprise performance and cyberdefense.
Just as in real estate, when it comes to firewall placement, location is everything.
First introduced nearly 40 years ago, firewalls are key network security tools that provide boundaries between outside and internal networks. A firewall acts as a buffer between the private corporate network and the public internet, executing rules designed to protect the organization from dangerous inbound traffic, while also preventing data leakage and theft of internal data assets.
Inbound and outbound packets are routed to the firewall, which assesses the traffic and applies firewall rules based on corporate policy to either relay the traffic in either direction or block it. For example, a corporation might limit which websites employees are allowed to access or restrict what data they can share externally.
As enterprise networking has advanced, so have firewalls. They now not only protect internal networks from external traffic, but also enforce network segmentation rules and protect different parts of the network with varying security needs.
Let's look at common firewall placements and the importance of proper placement.
Common firewall placements
Firewalls protect not only the network as a whole, but also subnetworks. They segment different sections of the corporate network by applying preconfigured rules that map to enterprise security policies. By acting as a perimeter, the firewall ensures subnetworks requiring a higher level of security or interacting with external users are protected without interfering with communications.
Between external and internal networks
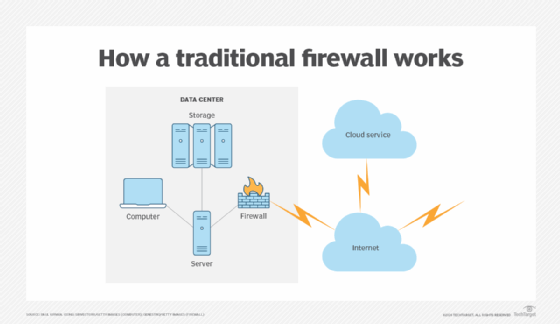
The most common firewall placement is between internal and external networks (the internet). Firewalls run on a dedicated machine or on a switch. They are typically installed across a WAN connection, usually right before the router at the ingress point to track and filter incoming and outgoing traffic. Routers themselves often have integrated firewall functionality to provide an additional level of protection.
Between external and DMZ networks
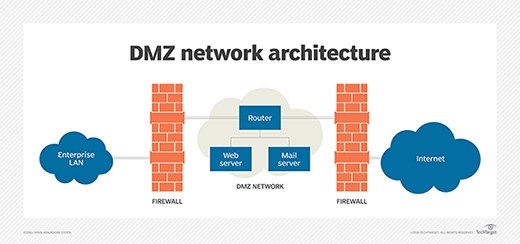
Firewalls can isolate demilitarized zone (DMZ) networks, which are subnetworks that support a company's customer-facing communications. A firewall between the DMZ and internal networks enables client interactions, while it prevents external parties from accessing internal corporate resources.
Between internal networks
Organizations can position firewalls between logically or physically separate internal subnetworks that might process confidential or sensitive data to enforce appropriate levels of access control.
Single vs. multiple firewalls
Organizations can use a single firewall or multiple firewalls to segment internal, restricted and DMZ networks according to policy. A more centralized organization that doesn't host customer-facing communications or has highly sensitive security requirements might opt to use a single firewall to protect the entire environment.
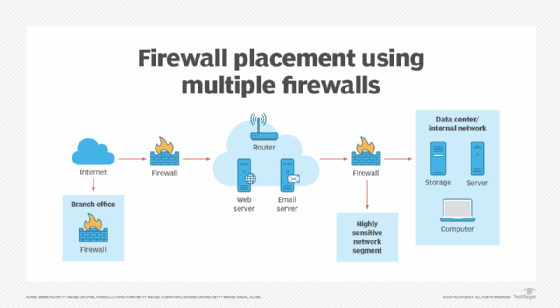
An enterprise with a more complex architecture and more variable security requirements might install multiple firewalls to carry out different security rules for specific segments and to elevate the level of security for the entire internal network. The perimeter firewall, the device closest to the WAN connection, sends traffic to and from the DMZ network. A second internal firewall takes in the traffic moving through the DMZ, screens it and passes it along to the internal network.
Some organizations opt to use multiple firewalls to cover both Layer 2 and Layer 3 interfaces. Layer 2 firewall interfaces apply the packet inspection used in intrusion prevention systems. Enterprises might also decide to use firewalls from different vendors to ensure that, if there is a security flaw associated with one, the other catches it.
Firewall placement: Benefits and best practices
Where firewalls are situated has a major effect on performance and efficiency.
Firewall placement is closely connected to network architecture. For example, companies with large, complex network infrastructures might install firewalls in parallel to improve service quality. Parallel firewalls often also include a load balancer and a firewall array, with each firewall configured the same way and executing the same rules. Arriving packets are then passed along to one of the firewalls.
Firewalls help maintain business continuity by protecting assets in situations where internal employees interact with individuals outside the organization. Network firewalls also give administrators a mechanism to carry out rules for DMZ or other restricted networks.
Some types of firewalls are not resource-intensive, so packet inspection and delivery generate only minimal delay. As firewall features become more complex, so does their resource consumption. Organizations also often use application-level gateways that conduct more in-depth analysis of network traffic by evaluating protocols. Stateful inspection firewalls that assess traffic for a broader swath of risks are more resource-consumptive, as are next-generation firewalls.
Another reason firewall placement is so crucial is that, if put in the wrong place -- for instance, ahead of a dedicated device -- there is a greater risk of relaying DoS traffic and malware to the server. Most firewalls are not built to process a high volume of connections per second. Rather, they deal with traffic flow based on IP addresses, protocols and applications.
Firewalls can be an effective defense against DoS attacks if they are located near multiple resources, rather than a single dedicated device, where it can quickly become overwhelmed.
Amy Larsen DeCarlo has covered the IT industry for more than 30 years, as a journalist, editor and analyst. As a principal analyst at GlobalData, she covers managed security and cloud services.








