
Vitalii Gulenok/istock via Getty
WAF vs. RASP for web app security: What's the difference?
Web application firewalls use a negative security model, while runtime application self-protection tools use a positive security model. Which is better at keeping apps secure?
As organizations deploy more web applications, protecting them from a variety of threats becomes increasingly critical. Two prominent security technologies have emerged to help: web application firewalls and runtime application self-protection.
In a nutshell, WAFs are a type of firewall that monitors, filters and stops suspicious traffic to and from web apps, while RASP tools sit internally on each app to monitor behavior and stop threats in real time.
The best way to evaluate and compare WAF vs. RASP is to consider three key factors: implementation complexity, ongoing costs and security effectiveness.
Let's look deeper at how each technology protects web applications, how they compare and whether to adopt one or both.
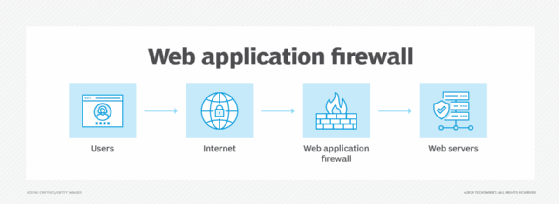
What is a web application firewall?
A WAF is a type of firewall that acts as a security barrier between web applications and the internet by monitoring and filtering HTTP traffic. WAFs inspect incoming requests and outgoing responses and apply predefined security rules to identify and block malicious traffic patterns. They excel at protecting against common web attacks, such as SQL injection, cross-site scripting and other vulnerabilities.
WAFs are network-based, host-based or cloud-based. Functioning as an external application shield, they analyze traffic patterns and parameters without requiring modifications to the application code. This makes them relatively straightforward to implement across multiple applications.
Take a typical SQL injection attack, such as 1' OR '1'='1, for example. WAFs have a specific rule to detect that text pattern -- commonly via a regular expression parser -- identify it as characteristic of a SQL injection attack and block the input.
What is runtime application self-protection?
RASP tools provide a more modern approach to application security. Unlike WAFs, RASP technology integrates directly into the application through software instrumentation -- for example, a debugger instrumenting code to insert breakpoints -- enabling it to monitor and protect the application from within. This integration helps RASP understand the application's behavior, context and logic in real time.
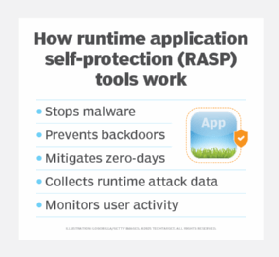
RASP tools operate by instrumenting the application's runtime environment, such as a Java VM or .NET Common Language Runtime, to provide deep visibility into application execution.
Returning to the SQL injection example, a RASP engine behaves differently than a WAF. Based on the code, the engine models an abstract syntax tree containing a select operation with a query and validates if the syntax to be executed against the database matches it. If it does match, no injection has occurred, and the query is safe. In a SQL injection attack, such as 1' OR '1'='1, however, the syntax has been modified to include a logic OR operation. RASP immediately triggers this as an injection and blocks the request. The RASP engine did not consider the format or values of the query itself, rather the fact that the syntax was expanded indicated an injection attack was in progress.
How do WAF and RASP compare?
A fundamental distinction between WAF and RASP lies in their security models. WAFs typically employ a negative security model, which means they identify and block known malicious patterns and behaviors. They maintain extensive lists of attack signatures and suspicious patterns, blocking anything that matches these known-bad behaviors.
While effective against known attack patterns, this approach can yield false positives when legitimate requests match suspicious patterns. WAF rules can also miss new attack vectors, including zero-day vulnerabilities, or carefully crafted payloads. To illustrate this, consider the WAF example with a different payload: 1' OR 2>1–. The WAF requires another rule for logical operators with comparisons to detect this, which quickly escalates into an arms race between attackers and defenders.
RASP technology, in contrast, typically implements a positive security model. It learns and understands how the application should behave during normal operation and then flags or blocks any deviations from this expected behavior. By running within the application context, RASP can make more precise security decisions based on application behavior, data flow and execution context. This approach typically results in fewer false positives, as shown in the SQL injection example, where the injection detection is precise, regardless of the input payload. RASP tools also enable organizations to better detect and prevent zero-day threats to web apps.
Other key differences are cost and management. Adopting RASP has significant operational and cost implications. First, teams need to couple the RASP engine to the main application, usually during the development cycle. This introduces some performance overhead into the application's execution and complicates the development and operation cycles because teams need to manage an additional software component. DevOps teams, therefore, often perceive RASP poorly.
WAFs offer the advantages of ubiquity and low cost, comparatively. Most firewalls, gateways and proxies offer free or open source implementations as part of the standard product. For example, the popular ModSecurity tool is available on Apache, Nginx and other web servers. RASP is predominantly a commercial offering from specialist vendors and is not universally available on all platforms. For example, C/C++ and native or unmanaged languages are poorly supported.
These different security models reflect their operational approaches: WAFs function as perimeter defense systems that make decisions based on predefined rules, while RASP operates from within the application itself, providing deeper contextual awareness. Each approach has its strengths -- WAFs excel at rapidly blocking known attack patterns, while RASP provides more nuanced protection against both known and novel threats.
RASP vs. WAF -- or both?
Rather than viewing WAF and RASP as competing security tools, consider them complementary technologies that address different aspects of application security.
WAFs provide broad protection against known attack patterns and can be quickly deployed across multiple applications. They serve as an essential first line of defense, filtering out apparent malicious traffic before it reaches the application.
RASP provides an additional security layer by protecting applications from within, catching sophisticated attacks that might slip past WAF defenses. Its context-aware protection is particularly valuable for critical applications that handle sensitive data or financial transactions.
For optimal security coverage, organizations should consider implementing both technologies:
- Use a WAF as a primary defense against common web attacks and malicious traffic.
- Deploy RASP for critical applications requiring precise, context-aware protection.
- Use the complementary nature of both options to create defense in depth.
This combined approach provides comprehensive application protection, while balancing security needs, operational considerations and resource constraints.
Colin Domoney is a software security consultant who evangelizes DevSecOps and helps developers secure their software. He has previously worked for Veracode and 42Crunch and authored a book on API security. He is currently a CTO, co-founder and independent security consultant.








