
Konstantin Emelyanov - Fotolia
Using SDP as a VPN alternative to secure remote workforces
Software-defined perimeter has been touted as a VPN alternative for secure remote access. How do you know if SDP or a traditional VPN is right for your company?
Traditional on-premises VPNs can be expensive and difficult to operate and maintain. Thus, many organizations tasked with maintaining or moving to a newly remote workforce are considering other network security alternatives.
Some are weighing software-defined perimeter (SDP) as a VPN alternative. SDP services from Palo Alto Networks and Zscaler, for example, can simplify remote access at a broad scale, pending some degree of financial and operational investment.
Several new VPN alternatives are simpler to set up and manage than traditional VPNs, but each may bring additional risks. For example, SDP may require organizations to use third-party brokers and service environments for hosting or facilitating access, which could bring a number of security issues.
Traditional VPN vs. SDP technology
With SDP tools and services, a cloud service provider environment brokers connectivity in place of a traditional VPN. In an SDP architecture, the SDP client is deployed on each endpoint. End users manually or automatically connect to an SDP service provider's point of presence (PoP) in the cloud. From there, users can connect to on-premises resources, cloud services or both. All users, endpoints and policies are managed from a single console.
There is some confusion about the key differences between an SDP and traditional VPN architecture and controls. Enterprise networking and security teams should consult the table below to decipher how traditional VPN and SDP features differ.
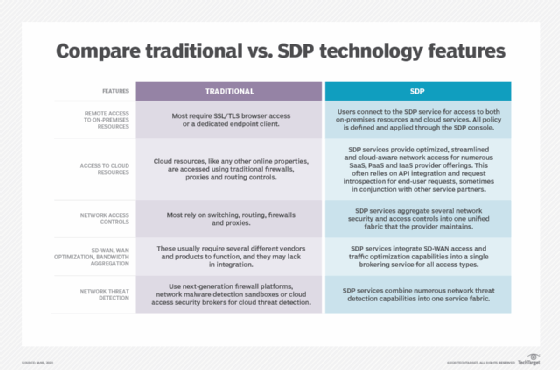
Organizations considering SDP as a VPN alternative based on networking and networking security capabilities should take two areas into account:
- Performance requirements. Be sure to scrutinize uptime and availability service-level agreements, along with the breadth in PoPs for connectivity.
- Security requirements. Carefully assess network and network security capabilities. Not all providers have the same level of maturity in each area. For example, Zscaler has a strong content filtering and proxy service in its Zscaler Internet Access gateway and a wide range of PoPs globally. Palo Alto Networks has fewer PoPs but stronger security controls for network intrusion prevention systems (IPSes) and next-generation firewalls.
SDP services are being updated regularly, so organizations should stay informed of the latest features and improvements before making a buying decision.
Limitations of SDP as a VPN alternative
While it does have its benefits, networking and security teams should understand that an SDP VPN alternative is not without its pitfalls. Potential drawbacks include the following:
- Ease-of-use challenges. Some SDP vendor offerings are a combination of acquisitions and bolted-on controls and services.
- Subpar security controls in various areas. Some services may not excel at IPS or malware sandboxing, for example.
- Limited application support. Not all cloud applications are natively supported for easy integration, and some may require additional configuration and tuning.
- Number of global PoPs available. This directly affects end-user latency and connectivity.
Most implementations entail testing with pre-configured clients that are set to connect to local provider PoPs based on current location. Once the system and user are identified, security and connectivity policies are applied and enforced to allow or prohibit access to cloud or on-premises applications and services. Depending on the type of access provisioned, some tuning of controls and bandwidth usage may be necessary to improve end-user experience. Also, organizations with a large variety of end-user devices, applications and use cases should expect longer implementation cycles, potentially between 12 and 18 months.
Most implementations with leading providers have not led to major system performance issues with clients on either Mac or Windows. However, there have been cases of local client conflicts with other installed software, so be sure to test carefully.








