
kentoh - Fotolia
Unify on-premises and cloud access control with SDP
One security framework available to organizations struggling with on-premises and cloud access control issues is a software-defined perimeter. Learn how SDP can help.
Cyberthreats continue to grow more ubiquitous, subtle and tenacious. In response, the array of software and tools intended to mitigate or neutralize those threats expands steadily. One exciting security framework available has the potential to dramatically improve an organization's overall security posture and neutralize a huge swath of threats is the software-defined perimeter, or SDP.
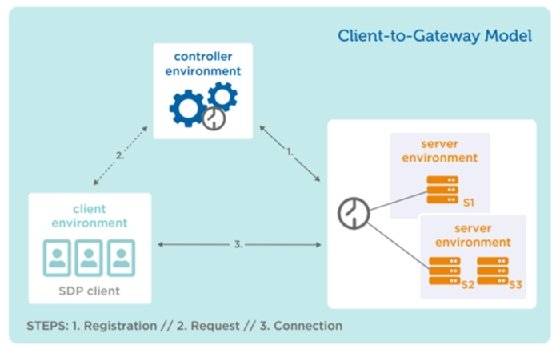
A key component to addressing access control issues, SDP establishes an environment in which only sanctioned network communications flow in and out. At its base, SDP instantiates a "discard all" default network configuration for every node. Absent specific instructions to the contrary, each protected node will drop any packet it receives. Nodes are then instructed as to which flows they should accept by an SDP controller.
Client systems also have an agent -- usually dedicated, though dynamic instantiation via browser is possible. People using the client, whether on premises or working remotely, authenticate to the SDP controller at login. Their machines are authenticated as well. This can include machine health checks.
Based on multiple factors -- including who the users are, what they're trying to access, their location, time and date, and machine information -- the SDP controller will decide whether access to the services' infrastructure is granted. The controller will usually integrate with one or more enterprise directories as systems of record for users and groups.
SDP for on-premises access
For on-premises services, IT can install on servers SDP agents that control the network stack and enforce the "drop all unless specifically sanctioned" policy. Or it can isolate service-providing infrastructure behind gateways, with a gateway controlling all traffic in or out. Either way, control of access to any and all systems can be unified in SDP.
Notably, SDP can be a single path to services even if companies have different directories tracking user identities and groups for different client platforms or services. This is often the case in international organizations, for example. These companies that grow by frequent acquisition and organizations have fragmented IT organizations and service environments, which can benefit greatly from using SDP for access control.
SDP for cloud access
SDP cannot provide the same level of "black hole" protection to SaaS and IaaS as it can to on-premises services. This is because the access points for such services have to face the public internet, and the services themselves are multi-tenant.
However, SDP can provide unifying access controls for cloud services at the same time it protects on-premises users and services.
To be able to benefit from SDP, a cloud environment has to support the enterprise's ability to restrict access to company instances to specific address ranges or domains. Salesforce, AWS and Microsoft 365, among others, support this level of control. By establishing gateways for those environments -- usually themselves in a cloud environment, enterprise-instantiated or in an SDP-as-a-service provider's own infrastructure -- SDP can enforce policies consistently across clouds.
Functioning in this capacity, SDP takes on the role of a cloud access security broker (CASB), providing a unified policy environment and visibility into usage across platforms. Note that there are other CASB functions SDP does not provide -- for example, API-style access to activities within a cloud environment.
SDP is not a single solution for all security challenges, but it can be a means of both dramatically strengthening and simplifying access control in any complex and/or hybrid service environment, especially when implementing zero trust.








