denisismagilov - stock.adobe.com
Top blockchain attacks, hacks and security issues explained
Blockchain is an attractive target for malicious actors. From blockchain-specific attacks to human vulnerabilities to lack of regulations, these are the top blockchain issues.
Blockchain technology has a number of security benefits. Transaction verification no longer relies on a single centralized institution. Having no single point of failure is not just an inherent security benefit of a decentralized structural paradigm, but also a fundamental philosophical and business driver.
Blockchain is also composed of several built-in security features, including cryptography, software-mediated contracts and identity controls. It offers significant levels of data protection and integrity by enabling a distributed way to verify access, authenticate transaction records and maintain privacy.
Despite these security enhancements, however, the blockchain market has been rife with security issues. Where there is potential for a payoff, there are malicious actors -- and blockchain networks are proliferating both.
Here are six factors that have created issues for the blockchain security landscape.
1. New blockchain exploit tactics
New technologies come with new tools and methods for exploitation, and blockchain is no exception. A new class of cyber threats is emerging, involving tactics unique to blockchain networks. These include the following:
- 51% attacks are when the majority of a network conspires against a minority of participants, as seen in several incidents involving platforms such as Ethereum Classic, Verge Currency and ZenCash (now Horizen). In a 51% attack, a malicious miner or group of miners gains control of more than 50% of a network's hash use or computing resources, giving them the ability to alter the blockchain. The controlling party could then prevent transactions, halt payments, reverse transactions and conduct double-spend, a type of fraud that occurs when coins are used in more than one transaction.
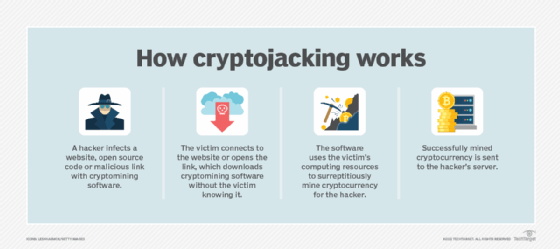
- Cryptojacking is when computers are hijacked for their computational power to mine cryptocurrencies. It is an example of backdoor and on-ramp exploits, which are similar to supply chain attacks but use the distributed nature of blockchain. In a cryptojacking attack, malware infects a target device and uses its electricity, hardware and other resources to mine cryptocurrency for the attacker.
![Graphic of how cryptojacking works]()
Cryptojacking involves malicious actors installing specialized malware that enables an attacker to use the victim's computing resources to mine cryptocurrency. - Flash loan attacks are when smart contracts that are designed to support flash loans -- loans that let users borrow assets without collateral -- are attacked to siphon assets elsewhere. These attacks exploit uncollateralized loans by manipulating smart contract inputs, as seen in the $24 million attack on xToken and $80 million attack on Beanstalk Farms.
- Rug pulls are when insiders -- such as crypto developers, criminal groups or paid influencers -- create hype about a project only to abandon it and run off with investors' funds. Such pump-and-dump schemes resulted in $170 million in losses across just 48 attacks in 2022 and made up more than half of all fraud schemes on cryptocurrency platforms, according to Crystal Blockchain.
2. Old exploits, new platform
Just as malicious actors are innovating new attacks specifically for blockchain, they are also adapting tried-and-true cybersecurity attacks to use on blockchain. Examples include the following:
- Phishing attacks involve malicious actors using social engineering techniques to attain users' credentials, install malware on users' devices, and obtain users' private keys and seed phrases -- recovery phrases generated by crypto wallets during setup that enable users to access their wallets if they forget their password or lose their device.
- Sybil attacks are when bad actors create and use multiple false identities to flood, overtake or crash a system -- usually to undermine authority. Some of the first instances of Sybil attacks were on peer-to-peer networks. In a blockchain context, Sybil attacks involve attackers using multiple fake nodes on the blockchain network, enabling them to prevent connections and transactions, take control of the network and conduct 51% attacks.
- DDoS attacks occur when attackers overwhelm their target network, causing the system to slow down or crash, thus denying services to legitimate users. A DDoS attack on a blockchain network has the same goal of taking down the system. In a blockchain DDoS attack, malicious actors could, for example, flood the network with spam transactions, causing operations to slow and preventing legitimate users from accessing it.
3. The human risk factor
Many blockchain attacks focus less on the technology and more on basic human vulnerabilities. For example, stolen cryptographic keys -- private digital signatures -- were the likely cause of crypto exchange Bitfinex's $73 million breach in 2016.
Endpoint vulnerabilities are also entry points for malicious actors, such as those at the device, app, wallet or third-party vendor level. Employees and vendor personnel are targets, too. The Bithumb crypto exchange, for example, was hacked using an employee's computer in 2017. Erroneous data input and developer incompetence, even with no malicious intent, are other risks to be aware of.
4. Not all blockchains are equal
Blockchain architectures vary widely, especially when it comes to how different structures and components introduce security tradeoffs. Private versus public blockchains, for example, differ in whether known entities or unknown entities can join the network and participate in verification.
Different network configurations employ different components, which carry different security risks. These configurations create several questions: How is a consensus achieved? How is identity verified? How are sidechains and/or data in transit managed? What incentivizes miners?
As components, algorithms and uses for blockchain continue to evolve, so too will attack tactics and threat mitigation techniques.
5. Lack of regulation
While many blockchain advocates worry regulation will delay innovation, regulations and standards can indeed benefit security and innovation. The current market is suffering from high fragmentation, where different companies, consortia and products operate using different rules and protocols. This means developers can't learn from the mistakes and vulnerabilities of others -- never mind risks of low integration.
Just because centralized brokers can be corrupt doesn't mean decentralized record-keeping is immune to corruption. Smart contracts are not a replacement for compliance -- they aren't legally binding. From money laundering to counterfeit and privacy to scams, an unclear regulatory environment slows adoption and enables cybercriminals to thrive.
6. Cybersecurity talent crisis
The current cybersecurity landscape suffers from a major skills shortage. This challenge is more severe in the blockchain security space because even fewer cybersecurity professionals have blockchain expertise or grasp novel security risks of the emerging Web3 decentralized economy.