Web 3.0 security risks: What you need to know
Elements of the third version of the web are coming to fruition. But Web 3.0 also comes with new cybersecurity, financial and privacy threats besides the familiar risks of Web 2.0.
The next chapter of the internet's evolution isn't just about a highly decentralized architecture; it will bring with it a host of security implications. These early days of so-called Web 3.0 have brought a surge in funding, development and hype, but also fraud and cybersecurity incidents.
As the broader market grapples with the potential and perils of a more decentralized internet, web developers and users must consider Web 3.0 in context, including its security features and risks.
What is Web 3.0?
Web 3.0 is a movement to shift the economic benefits of the World Wide Web to its participants by changing its foundational architecture. The first generation of the web, which is sometimes called Web 1.0, offered participants little agency, mostly limiting them to reading static information uploaded by site administrators.
Web 2.0 brought a revolution in unlocking user-generated content, from blogs to social media, video to mobile apps. As billions of people around the world began to entrust the web with their content, and later their personal, shopping, and financial information, big tech companies such as Amazon, Google and Facebook parent Meta amassed colossal amounts of centralized data, control and wealth. This centralization has not only exacerbated power asymmetries between users and platform administrators, as well as digital haves and have-nots, it has also confronted businesses and individuals alike with prolific cybersecurity, fraud and data privacy risks.
This article is part of
What is Web 3.0 (Web3)? Definition, guide and history
Web 3.0 thus marks a philosophical turning point as much as a technological one. Decentralized databases and ledgers distributed over nodes available to anyone are designed to counteract the risks of monopolization and centralized "honeypots" of sensitive information. Instead, trusted information will be available and simultaneously updated across many nodes, reducing the possibility of theft, fraud or deletion. Furthermore, the underlying blockchain technology allows any event -- whether transaction, interaction or identification -- to be uniquely represented, which enables tokenization. These capabilities underlie a novel form of digital economics, proponents believe, where anything, from content to currencies to credentials can be owned, transferred, sold or controlled by the user, independent of a centralized authority.
Security features of Web 3.0
The following aspects of Web 3.0 have the most impact on security:
- Identity and tokenization. Unique hashes allow authentication and user control of assets, and smart contracts determine the privileges, with eligibility based on reputation metrics that are tied to digital identities.
- Distributed ledger technology. The decentralized nature of DLT improves transparency and reduces the likelihood of tampering and fraud
- Zero trust. Data flows from peer to peer in decentralized applications instead of passing through intermediaries that users trust.
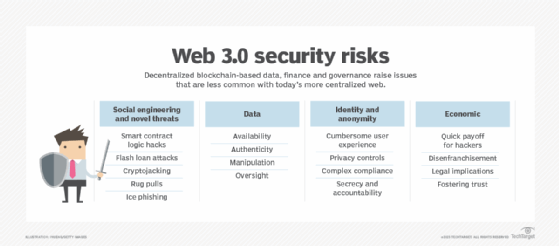
Web 3.0 security risks
The promise of Web 3.0 and blockchain architectures spells an exciting future, and it can be difficult to foresee the unique risks that might emerge from the design tradeoffs. For example, Web 2.0's democratization of user-generated web content wasn't just a revolution in expression, information access and community; it also ushered in an era of prolific misinformation, unprecedented surveillance and centralized gatekeepers.
Thus, these early days of Web 3.0 development are a crucial time to assess its emergent risks, which fall into the following four main categories:
1. Social engineering and new forms of attack
Web 3.0 has ushered in a new class of cyberthreats that are unique to blockchain networks and interfaces. Below are some examples of these novel threats:
- Smart contract logic hacks. This new threat targets the logic encoded in blockchain services. Hacks have been used to exploit a wide range of functions and services, such as interoperability, crypto-loan services, project governance and cryptocurrency wallet functions. Smart contract logic hacks also raise important legal questions because smart contracts are often not protected by the law or are fragmented across jurisdictions.
- Flash loan attacks. With this threat, smart contracts designated to support the provision of flash loans are attacked to siphon off assets. Uncollateralized loans are exploited by manipulating various inputs to the smart contract, as happened recently in a $24 million attack on xToken.
- Cryptojacking. Cryptojacking occurs when threat actors quietly install crypto-mining software on victims' computers and networks.
- Rug pulls. These attacks involve insiders -- crypto developers, criminal groups, paid influencers, etc. -- creating hype around a project, only to run off with the investors' funds.
- Ice phishing. In ice phishing, attackers convince users to sign a transaction that delegates approval of the users' tokens to the attacker.
These novel methods exist alongside traditional social engineering threats, such as phishing attacks. The risks are exacerbated by the fact that users must take responsibility for the security of their data, rather than relying on centralized gatekeepers. In fact, the complexity of Web 3.0 interfaces -- often involving multiple, personally managed wallets and passwords that cannot be restored -- creates a vulnerability to social engineering attacks.
Many recent blockchain attacks have focused less on the technology and more on basic human vulnerabilities. For example, stolen cryptographic keys (private digital signatures) were the likely cause of the $73 million breach of the Bitfinex cryptocurrency exchange. Endpoint vulnerabilities, such as those at the device, app, wallet or third-party vendor level, are also entry points for malicious actors. Employees or vendor personnel are also targets, as exemplified in the case of Bithumb, a crypto exchange that investigators say was hacked by compromising an employee's computer.
2. Data security and reliability
A wider network topology that encompasses actors, data storage and interfaces inherently expands the aperture of security risks. While blockchain transactions are encrypted, and decentralization of data and services reduces single points of attack and risks of censorship, they also have the potential to expose data to a broader set of risks, including the following:
- Data availability. Given that far greater control lies with end-user nodes, questions emerge about how depending on nodes for data availability might affect processes or applications if the data becomes unavailable.
- Data authenticity. The inverse of the availability challenge is also worth noting: How will people ensure that the available data is authentic, accurate, original or valid? Decentralization makes censorship more difficult but perpetuates questions of information quality and accuracy, which has already led to vast misinformation, disinformation and security issues. It remains unclear how disruptions to zero trust, identity and gatekeeping affect the quality of data, not to mention artificial intelligence models that ingest these data.
- Data manipulation. Data manipulation risks underlying several parts of the Web 3.0 ecosystem include, but are not limited to, the following:
-
- injecting malicious scripts into or across the wide range of programming languages involved in Web 3.0 to execute application commands;
- eavesdropping or intercepting unencrypted data transmitted across a network;
- wallet cloning, which attackers can do if they access a user's passphrase, effectively taking over its contents; and
- unauthorized access to data, which opens hackers up to all of the above, in addition to impersonating the end-user node.
- Less centralized oversight. Other Web 3.0 security issues include attacks on endpoints, traffic overloads and other service availability exploits -- which will likely receive less, not more, IT oversight. Questions of safety span the broader Web 3.0 web as well. Consider, for example, the difficulty of policing cybercriminals across distributed and anonymous actors or within a metaverse.
3. Identity and anonymity
Web 3.0 capabilities, such as user-controlled wallets, ID portability and data minimization, mitigate some of Web 2.0's data confidentiality and privacy risks by offering people greater agency and control over their data. However, self-sovereign identity (SSI), pseudonymity and anonymity have downsides. The transparent nature of public blockchains, which make the record of transactions available to everyone, builds trust without an intermediary but also comes with security and privacy tradeoffs. Here are a few examples of identity-related risks of Web 3.0:
- User experience. Most SSI and crypto wallets require cumbersome onboarding processes, education about private keys and multiple versions with little interoperability.
- Privacy. Web 3.0 has led to many questions about privacy. What information is stored on-chain vs. off-chain? Who needs to know when and how to authenticate transactions? Who decides, based on what parameters?
- Compliance. Web 3.0 pseudonymity creates data gaps for regulators and opens doors for money laundering and terrorist financing. Decentralized IDs also complicate existing regulations, such as GDPR, making it difficult to discern personally identifiable information (PII) data controllers (entities responsible for ensuring privacy and security) from PII data processors (entities that process PII data according to the controller's instructions).
- Anonymity. Secrecy can cause confusion and erosion of social norms, as Web 2.0 bots have demonstrated. Anonymity raises questions of accountability, liability, legal recourse and consumer protections.
As Web 3.0 applications evolve in the coming decade, organizations must consider the following risks from adjacent technological, political and social forces:
- How will the use of biometrics affect identity in Web 3.0, whether for user or employee authentication, healthcare or otherwise?
- How will IoT device-identity features interact in Web 3.0 environments when infrastructure such as cars or solar panels become economic actors?
- How might institutional backlash, political abuse and nationally centralized blockchains shift the implications of immutable identity data and ownership?
Just like they did with Web 2.0, organizations must carefully consider questions surrounding Web 3.0 design, policy, human rights and monetization.
4. Economic incentives and social risks
Microeconomies, currencies and other financial assets are embedded in most of the early Web 3.0 applications and digital communities. They give rise to new incentives and disincentives that will shift the risk calculation. Take cybersecurity as an example: Web 3.0's embedded economic architectures create clear incentives for hackers compared to traditional cloud or IT deployments. In traditional environments, services and data are often exploited without a clear or immediate monetary benefit. In blockchain applications, in comparison, significant value is often already encoded directly in the blockchain.
Businesses must also evaluate Web 3.0 for consumer and related legal, environmental and societal risks. As notions of individual ownership, financialized participation and decentralized interoperability are embedded in the web, business leaders and those designing and safeguarding the Web 3.0 ecosystem face several questions that affect the security of the organization and individuals:
- How can businesses support accessibility and avoid exacerbating digital and financial disenfranchisement?
- How can organizations support societal and environmental improvement when UX is hyper-capitalized and interactions are driven by tokenization, artificial scarcity or other purchasable signals of reputation?
- How will traditional businesses transact with Web 3.0-native decentralized autonomous organizations, and what are the legal "wrappers" that provide protection?
- Most importantly, how will organizations foster the trust of individual participants and businesses in Web 3.0 environments?

New opportunities mean new risks
The next generation of the web is not just about empowering people through distributed governance -- technical, social and economic -- it's also about better securing the ecosystem in the process. Distributed networks offer some security benefits, but they are far from immune to software exploits, human error and other vulnerabilities.
The vision of Web 3.0 addresses crucial issues of its predecessor related to power asymmetry, control, censorship, fraud, privacy and the risk of data loss. However, it does not exclude the emergence of a new class of risks in data security, identity, economic incentives and novel approaches to social engineering.







