
natali_mis - stock.adobe.com
Technical controls to prevent business email compromise attacks
Technical controls are at the heart of preventing successful business email compromise attacks. Learn about those and extra considerations to keep your business secure.
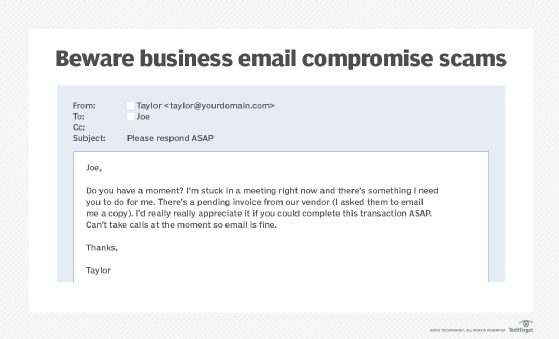
A CFO named Joe receives an email from CEO Taylor requesting a large payment to a contractor. In the email, Taylor stresses that the transfer is extremely time-sensitive and urges Joe to act with haste. Being a responsible and efficient CFO, Joe sets up the transfer and initiates the payment. Yet, fortunately for Joe, large payments at the company require a second approver, who, in this case, is Taylor, the CEO herself. Taylor is alarmed by what she sees: She never requested payment and has never even heard of the purported contractor.
If your organization has experienced a similar scenario, it has fallen victim to a business email compromise, or BEC. This isn't theoretical -- it's a reality that is happening to companies every day.
What is BEC?
BEC is a form of targeted spear phishing that focuses specifically on businesses and business executives, targeting organizations large and small. These attacks, sometimes called man-in-the-email attacks, involve malicious actors defrauding a company out of thousands of dollars -- or more.
BEC attacks are a hybrid of social engineering and technical attacks. The social side involves knowing who to target. In the above example, if the request to Joe had come from Meredith, a junior member of the quality assurance department, he wouldn't have taken it seriously. And, if the scam email had been sent to Meredith, she couldn't have transferred the money as she doesn't have the permissions to do so.
The tech side of BEC involves the actual spoofing. In some cases, attackers spoof email accounts or websites by slightly varying legitimate addresses -- for example, if the email came from [email protected] instead of [email protected]. In other cases, weak passwords are decoded and used by attackers. In most BEC attacks, however, nefarious actors use spear phishing emails or malware to spoof legitimate senders' email addresses.
Technical controls to stop the spoof
There are numerous methods to help users detect and not fall victim to BEC risk, all of which should be included in a company's security awareness training program, but let's look here at the technical controls.
The simplest way to prevent business email compromise attacks is to block illegitimate and spoofed email. Spoofed email is highly effective because it appears to come from a trusted source, like the above example where the email looked like it came from CEO Taylor. While no set of controls can guarantee 100% of unwanted mails are blocked, technology can prevent the lion's share of shady emails from hitting corporate inboxes.
Most large email providers, including Google and Microsoft, offer strong baseline protection against malicious email. To ensure the full benefit of available protections, however, companies must ensure those controls are turned on.
Key protection features include the following:
- DomainKeys Identified Mail (DKIM). DKIM uses keys to help prevent email spoofing. A signature is appended to outgoing email. When the inbound server receives the email, the signature is checked against the domain's public key. If there is a match, the email goes through. If it's not a match, it's blocked.
- Sender Policy Framework (SPF). When an email comes into a mail server, SPF checks against the approved email senders for the sender's domain. For example, the approved host to send email from techtarget.com is mxa-00051b01.gslb.pphosted.com. If a company has SPF turned on, the server will check the inbound email to see if there is a match for the approved mail exchanger and the actual one. If there isn't an authenticated match, the email can be dropped, ensuring it never reaches employee inboxes.
- Domain-based Message Authentication, Reporting and Conformance (DMARC). DMARC is an extension technology to SPF and DKIM. It enables a domain owner to publish the domain's email authentication requirements, such as whether the domain uses DKIM, SPF or both. DMARC also describes what should be done with an email if it fails authentication.
With DKIM or SPF and DMARC enabled, a company can greatly reduce the risk of passing spoofed emails into employee inboxes, which, in turn, limits BEC attack success.
Other controls for BEC protection
In addition to preventing spoofed email from making its way to employees, there are other technical controls for reducing BEC, including the following:
- Multifactor authentication (MFA). Some attackers skip past using spoofed emails by stealing credentials and sending BEC emails directly from a victim's account. In these cases, credential protection is paramount for prevention. Using MFA, such as a one-time passcode, will prevent an attacker from accessing the email account, even with a valid username and password.
- Forward rule checks. If attackers successfully access an employee's email account, one of the first things they may do is set up a mail forwarding rule to pass a copy of every inbound and outbound email from the victim's inbox to theirs. By doing this, the attacker can monitor all communications silently. Admins should lock down this functionality to ensure attackers can't use it. If your organizations has been a victim of BEC, be sure to check all email forwarding rules and remove any unauthorized ones.








