7 stages of the ransomware lifecycle
It can be nearly impossible to predict if or how a ransomware group will target an organization, but there are knowable stages of a ransomware attack.
Ransomware has steadily grown since Popp's 1989 introduction of the AIDS trojan. Predating the use of web links or email attachments, that first version was transported using floppy disks. While delivery methods have certainly changed, the behavior once the process starts shows a mix of consistency and variance.
Let's look at the distinct stages of the ransomware lifecycle to better understand how attackers strike -- and how defenders might be better able to resist.
1. Target selection and reconnaissance
A ransomware group, like a bank robber, needs a target that can pay. Attackers will gather publicly available data to include lookups that reveal who owns and runs the target site to determine if that site is self-managed or if it has outsourced its management to a cloud provider or other entity. The attacker might also seek to gather information on key site personnel, sometimes even attempting to build trust with them on social media. When there's trust, a targeted individual could be more susceptible to malware delivered via a link or an email message.
For victimized organizations, being selected is beyond their control. The best a business can do to avoid this fate is to harden its defenses to become a less appealing target. This is accomplished by preparing users and systems. Some common defensive steps include user awareness training, patching and general cyber hygiene practices.
2. Malware distribution and infection
Phishing, dirty links on malicious websites and social media spam are well-known methods of malware distribution. These methods persist because, despite awareness training for users, they work. A targeted user might be in a hurry, mentally overloaded, trying to be helpful or simply curious. Whatever the reason, they fall for the trap. Once clicked, the link or attachment executes the malware, and the infiltration has begun.
Another method for invoking ransomware is social media spam. This approach relies, in part, on clickbait. A video or link looks too appealing for targets to resist, and out of curiosity or because it appears to be from a trusted sender, they click.
Theft of user credentials can also factor into ransomware delivery. If cybercriminals obtain login credentials ahead of time through a phishing scheme or malicious link, they can introduce ransomware via a trusted user.
Researchers are also seeing the growing use of service exploitation as an attack vector. Rather than create and use propagating software, attackers will sometimes exploit known vulnerabilities in public-facing applications. Attackers might consider this route more promising now that users have been better trained to steer clear of suspicious links.
Security vendors see attackers increasingly targeting legitimate tools, such as OS features or software. Exploiting remote desktop services is one example of this tactic. By blending in with legitimate traffic, attackers can better hide in plain view. Plus, these more stealthy attacks can sometimes evade traditional detection software, which relies on spotting suspicious new processes or the opening of new ports.
3. Command and control
The command-and-control stage remains a central element in the ransomware kill chain.
Once it successfully infects a target device, malware typically begins to communicate with what's known as a command-and-control server, or C&C server. Under the control of threat actors, this external server is responsible for sending encryption keys to the target device. It might also download additional malware and network-probing software.
4. Exploration and lateral movement
This phase is where attackers seek avenues to delve deeper into an organization's IT systems, often by misusing employee credentials or admin accounts. If they succeed, they can do much more damage and steal valuable data. This ability to hunt across systems without being noticed is referred to as lateral movement.
This movement is now enhanced by AI, which can probe and respond on the host rather than needing to communicate with an external control server.
Lateral movement affords ransomware attackers the ability to maximize infiltration before they encrypt. If using a zero-day vulnerability, attackers could infiltrate multiple sites without being detected, thereby spreading the attack and maximizing potential profitability. Cloud environments remain attractive targets because they potentially provide attackers with access to many sites as well as to the hypervisor, a layer that is out of reach of some security tools.
Microsoft and others have noted many instances of ransomware groups using lateral movement to elevate access and manipulate settings within a target's security products, thus giving them even greater freedom to move without triggering alarms.
5. Exfiltration and encryption
Once found, data is copied. And then it is exfiltrated.
Exfiltration is often the moment when security software first detects something is wrong.
This is also the stage of a ransomware attack when attackers might encrypt the data they have taken. Encryption is a classic crypto ransomware tactic. Malicious actors offer decryption keys in exchange for ransom payment.
More recently, some attackers have decided to skip this step. In its 2024 threat report, Symantec said it had observed a rise in encryption-free attacks. Conducting exfiltration without encryption significantly decreases time attackers spend on a ransomware operation. Instead, ransomware groups use a snippet of data to convince targeted organizations that they possess entire data sets.
6. Extortion
At this point, ransomware targets typically see a message that includes some or all of the following information:
- Notification of infection.
- The amount of money the criminals demand in exchange for the decryption key.
- Instructions for submitting payment.
- A countdown timer to indicate how long the attackers will wait for a ransom to be paid before permanently taking the stolen data or increasing the ransom amount.
If the cybercriminals uploaded files to a C&C server, they might also threaten to publicly release the data in a tactic known as double-extortion ransomware. Triple-extortion ransomware involves a third element, such as a DDoS attack or parallel extortion of the targeted organization's customers or partners.
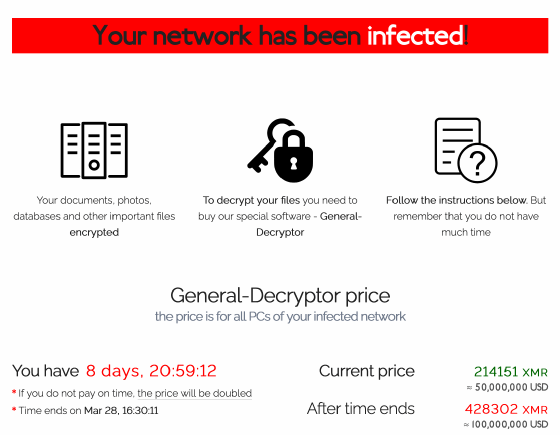
The dynamic between victim and attacker has shifted somewhat. Where historically the target was hit with ransomware and shut down while awaiting the decryption key, the confrontation is now more interactive. The attacker might encrypt the copied payload, but the victimized organization might have available backups, meaning it does not need the return of the entire data set. This dynamic opens the possibility of negotiating with a ransomware group to receive keys to a smaller subset of data or to agree on a smaller ransom. Negotiations are a factor in the decreasing payment amounts associated with ransomware.
7. Resolution and upgrades
Advanced security tools and techniques can reduce the risk of intrusion and increase the chances of uncovering and disrupting a ransomware attack if one is underway. Consider the following:
- Automated patch management. Malware often exploits unpatched vulnerabilities in a device's OS or applications. Patch management tools that automatically remediate known software security bugs can dramatically reduce the odds of a ransomware attack.
- Antimalware and antivirus software. Antimalware and antivirus software help identify and protect against known ransomware variants. When installed on devices and within email applications, these tools stop communication with known malicious domains and prevent installation of recognizable malware.
- Anomaly detection software. AI-based anomaly detection capabilities, such as those in user behavior analytics software, continuously scan network traffic to identify suspicious activity. Upon confirming a ransomware intrusion, the security team can quarantine infected devices to prevent further lateral movement and infection.
- Network microsegmentation. Microsegmentation lets IT teams restrict lateral movement. Logical separation of networks into granular subnetworks, each with tailored access control rules, prevents malware infections from spreading.
An improved defense-in-depth strategy relies on multiple detection, protection and hardening technologies to mitigate risk at each point of the potential attack chain. To guard against newer ransomware behaviors, consider two strategies. First, further tighten security controls to detect additional process activity and payload movement. Second, train security orchestration and automated response software to detect and remediate the changes to your environment that indicate anomalous activity.
The evolution of ransomware and changes in attacker behavior were inevitable, and they will likely continue to change and to become even more stealthy. These changes can be said to reflect the commoditization of the service. The rise of ransomware as a service results in a greater supply of attackers. To safeguard data, cybersecurity professionals need to keep pace with these always-changing ransomware threats.
Editor's note: This article was updated in April 2025 to add new information.
Char Sample is a cybersecurity research fellow at ICF International.
Andrew Froehlich is founder of InfraMomentum, an enterprise IT research and analyst firm, and president of West Gate Networks, an IT consulting company. He has been involved in enterprise IT for more than 20 years.






