Securing remote access for cloud-based systems
Don't believe the hype: Access control in the cloud is not a lost cause. Read these tips to learn how you can better secure remote access to your cloud-based systems.
The following is an excerpt from The Official (ISC)2 Guide to the CCSP CBK, Second Edition, by Adam Gordon, CISSP-ISSAP, ISSMP, SSCP. This section from Domain 5 outlines potential vulnerabilities surrounding remote access of cloud-based systems and tips for protecting cloud environments.
Cloud-based systems provide resources to users across many different deployment methods and service models, as has been discussed throughout this book. According to NIST SP 800-145, "The NIST Definition of Cloud Computing," the three service models for cloud computing are software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (laaS). The four cloud deployment methods are private cloud, public cloud, community cloud and hybrid cloud.
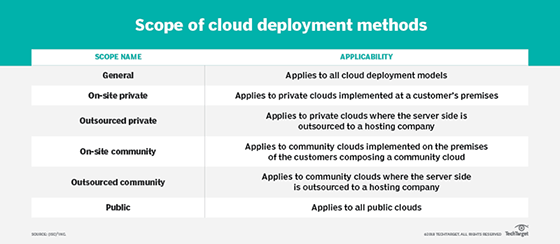
Regardless of the model, deployment method, and scope of the cloud-based systems in use, the need to allow customers to securely access data and resources is consistent. Your job as a CCSP is to ensure that all authenticated and authorized users of a cloud resource can access that resource securely, ensuring that confidentiality and integrity are maintained, if necessary, and that availability is maintained at the documented and agreed-upon levels for the resource based on the SLA in force.
Some of the threats that the CCSP needs to consider regarding remote access are as follows:
- Lack of physical security controls
- Unsecured networks
- Infected endpoints accessing the internal network
- External access to internal resources
Given the nature of cloud resources, all customer access is remote. Several methods are available for controlling remote access, including these:
- Tunneling via VPN/IPsec or SSL
- Remote desktop protocol (RDP), which allows for desktop access to remote systems
- Access via a secure terminal
- Deployment of a DMZ
There are several cloud environment access requirements. The environment of cloud-based systems should provide each of the following:
- Encrypted transmission of all communications between the remote user and the host
- Secure login with complex passwords or certificate-based login
- Two-factor authentication providing enhanced security
- A log and audit of all connections
It is important to establish OS baseline compliance monitoring and remediation. In doing so, determine who is responsible for the secure configuration of the underlying OSes installed in the environment of the cloud-based systems based on the deployment method and service model being used.
Regardless of who is responsible, a secure baseline should be established, and all deployments and updates should be made from a change- and version-controlled master image.
Conduct automated and ad hoc vulnerability scanning and monitoring activities on the underlying infrastructure of cloud-based systems to validate compliance with all baseline requirements. This ensures that any regulatory-based compliance issues and risks are discovered and documented. Resolve or remediate any deviation in a timely manner.
Sufficient supporting infrastructure and tools should be in place to allow for the patching and maintenance of relevant infrastructure without impact on the end user or customer. Patch management and other remediation activities typically require entry into maintenance mode. Many virtualization vendors offer OS image baselining features as part of their platforms.
The specific activities and technology that will be used to create, document, manage, and deploy OS image baselines vary by vendor. Follow the best practice recommendations and guidance provided by the vendor.
CCSP® is a registered mark of (ISC)².





