
alphaspirit - Fotolia
Protecting safety instrumented systems from malware attacks
Trisis malware targets safety instrumented systems and puts industrial control systems at risk. Expert Ernie Hayden reviews what to know about SIS and its security measures.
A newly discovered attack on industrial control systems has the security world uncovering more questions than answers. The 2018 S4 Conference even included presentations and multiple side conversations about the attack called Trisis/Triton/HatMan.
The first public awareness of this attack came after cybersecurity company FireEye published a blog post about it in mid-December 2017. The company's moniker for this malware was Triton. Close on the heels of the FireEye announcement, Dragos CEO Robert Lee published a white paper analyzing the malware that he called Trisis because it targeted Schneider Electric's Triconex Safety Instrumented Systems.
On Dec. 18, 2017, the U.S. Department of Homeland Security's National Cybersecurity and Communications Integration Center (NCCIC) published its malware analysis report, industrial control systems (ICS)-CERT MAR-17-352-01, "HatMan -- Safety System Targeted Malware," which included its summary of the Triton/Trisis/HatMan malicious code.
Almost daily, new commentaries and analyses of Triton/Trisis/HatMan are published. It is obvious that the attack has raised more questions than answers, including: Who orchestrated the attack? Why did they develop this code? What was the attack's purpose? Are there more malware attacks to come?
One thing is certain, according to Lee, "Trisis is the first ever [attack] to target safety instrumented systems, and it is the one that gives me the most concern."
What is a safety instrumented system?
A simple, but not perfect, way to think about safety instrumented systems (SIS) is to consider them part of a dead man's switch configuration.
Dead man's switch (DMS) mechanisms are used in a variety of operating environments, such as locomotives, lawn mowers, chainsaws, snowblowers, and even for aircraft refueling. The idea is that the DMS must be continuously held or pressed by an operator, and, if the switch/handle is released during operation, the machine will either stop running or transition to a safer state, such as idling.
A DMS control in a locomotive can be a floor pedal, trigger handle or push-button where the device must be continuously held or pressed to enable the locomotive to move forward. If the engineer driving the train is incapacitated for any reason, the release of the DMS causes the engine to idle and, in some locomotives, the emergency brakes are applied. The system fails safe.
Traditional dead man's switches in trains can be overridden using duct tape, heavy bricks or other methods, and, in rare cases, the switches can fail to engage when an incapacitated engineer slumps forward.
Safety instrumented systems are more complicated than the dead man's switch described above. However, the SIS is installed -- optimally in its own dedicated network zone -- so that plant operations can be shut down under extreme plant conditions without human intervention. In other words, the plant can fail safe.
Emerson Process Management literature notes that safety instrumented systems "are specifically designed to protect personnel, equipment, and the environment by reducing the likelihood or the impact severity of an identified emergency event."
An SIS is composed of a combination of sensors, logic solvers and final elements that are separate and distinct from the other plant controls. If the plant is out of control, the SIS is there to shut the plant down with no reliance on human intervention.
Some SIS configurations include dedicated sensors that shut down plant operations -- such as refineries -- when certain pressures or temperatures are exceeded. Another example of an SIS working is a nuclear reactor automatic shutdown -- called a SCRAM -- when coolant flow is below a minimum rate, etc. Again, no human intervention is necessary.
According to standards established by the International Electrotechnical Commission in IEC 61511 and the International Society of Automation ISA S84.01, safety instrumented systems must be separate and distinct -- independent -- from other control systems that operate and control the same equipment/systems. The controls and control systems contained within the SIS are devoted solely to the proper operation of the safety system. There is no reliance on outside controls or sensor input for the SIS to trip.
Safety instrumented systems architecture
Some ICS security experts may refer to the Purdue reference model -- or the Purdue model -- when discussing ICS network architecture. The Purdue model is a part of the Purdue Enterprise Reference Architecture, which provides a framework for designing manufacturing systems, and which was developed in the 1990s by Theodore Williams and the members of the Industry-Purdue University Consortium for Computer Integrated Manufacturing.
The Purdue model is intended to help users understand a production network. The model organizes an industrial plant network architecture into four levels -- plus the underlying physical process level -- and is illustrated below.
- Level 0: The physical process -- This is where the physical work in the plant gets done.
- Level 1: Intelligent devices -- This level includes the sensors, programmable logic controllers (PLCS) and the actuators. This level has its own distinct and separate sub-zone specifically for SIS.
- Level 2: Control systems -- This level is where the production is monitored, controlled and electronically supervised, and it includes the production video screens that display the Human Machine Interface and real-time controls and software.
- Level 3: Manufacturing operations systems -- This level is essentially the brains of the manufacturing operations. It includes manufacturing execution systems, maintenance and plant performance management systems, data historians, and middleware.
- Level 4: Business logistics systems -- This is on the enterprise side of the plant. At this level, business-related manufacturing activities are performed, primarily relying on enterprise resource planning software, such as SAP. This is where the plant production schedule is generated and material inventory, shipping and use are monitored and modified.
Basically, when you are in the manufacturing plant, you are looking primarily at Levels 0, 1, 2 and 3.
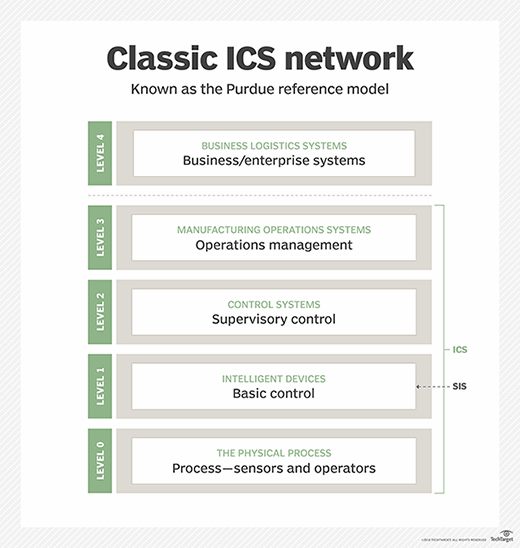
In the Purdue model, the SIS is located at Level 1 and comprises its own stand-alone network zone. The safety and protection systems monitor the manufacturing processes and, under emergency conditions, activate and return the plant to a safe state by closing valves, shutting off burners, increasing cooling water flow, etc. These safety and protection systems also include tools that monitor manufacturing and alert an operator of impending unsafe conditions.
SIS controller versus a PLC
You should understand that, visually, an SIS and an off-the-shelf programmable logic controller (PLC) or other industrial PC may look the same; however, they have different functions and different implementation schemes. Vendors typically use their current line of PLCs and modify them to fill the SIS role.
According to Clint Bodungen's Hacking Exposed: Industrial Control Systems, "... the SIS typically uses a complicated series of both analog and digital 1-out-of-2 or 2-out-of-3 voting systems to monitor and respond to adverse process conditions. Normally, SISs are designated to provide only a few core functions ..." when compared to the normal, multifunctional PLC in the manufacturing plant.
Safety instrumented systems may not be installed in every plant; however, they will be included in plants that can be affected by hackers, cyberthreats, terrorists or internal attackers, and which could result in serious dangers, such as death, injury, environmental releases, etc. So you may not see an SIS in a benign manufacturing facility, but the refinery next-door would have more than one SIS in place.
The crisis of a violated SIS
As noted above in Lee's comment regarding his concern that the SIS has been violated by Trisis, the demonstration of the SIS being violated by malware is very serious. Trisis/Triton/HatMan in the SIS may not do anything catastrophic by itself; however, the NCCIC observes "... it could be very damaging when combined with malware that impacts the (manufacturing) process in tandem."
Essentially the capacity to disable, modify or inhibit the ability of an SIS to fail safely can potentially result in physical consequences, environmental impact, injuries and even death.
In the Dragos blog, a FAQ entry rhetorically asks, "Is Trisis a Big Deal?" The answer is yes.
- Trisis is the fifth known ICS-tailored malware following Stuxnet, Havex, BlackEnergy2 and CrashOverride.
- Trisis is the first publicly known ICS-tailored malware to target SIS.
- Lastly, because SISs are specifically designed and deployed to ensure the safety of the manufacturing process, environment and human life, an assault on SIS is "... bold and unsettling."
Yes, the effect of Trisis is disconcerting and brings added attention to the security and integrity of the SIS. However, an SIS can be defeated without exotic malware by placing the SIS controller in bypass, placing the logic solver in an infinite loop, changing the trip and alarm set points, disconnecting the output from the logic, spoofing the inputs, etc., according to Secure the SIS by William L. Mostia. So waiting for SIS malware to prompt you to protect your SIS may not be enough.
The SIS is critical to safe plant operations and needs to be designed, implemented and maintained with utmost care and oversight. The Trisis/Triton/HatMan attack has certainly awakened the ICS security community.
As observed by Dale Peterson, founder and CEO of Digital Bond, a control system security company based in Sunrise, Fla., and producer of the annual S4 Conference, we are in the early stages of analyzing this SIS malware attack.
The industry needs to be reminded of how much we learned about Stuxnet after the detailed work done by Ralph Langner, et al.; however, it took time and resources before we really knew the details of Stuxnet. We may need to be patient with the ICS researchers who can tell us more about this new SIS malware and how we can best protect ourselves.







