
Silvano Rebai - Fotolia
Network visibility and monitoring tools now amp up security
Three technology trends are currently making network visibility even more central to security tools. Learn more about the impact of big data, AI and APIs.
Network visibility and monitoring tools used to belong strictly to the network team, while the security department managed data security tools. However, IT teams are now realizing that network security is vastly improved by security tools that can tap into end-to-end network visibility platforms.
In this article, we'll look at how network visibility and monitoring are beginning to merge with network security in the latest enterprise tools.
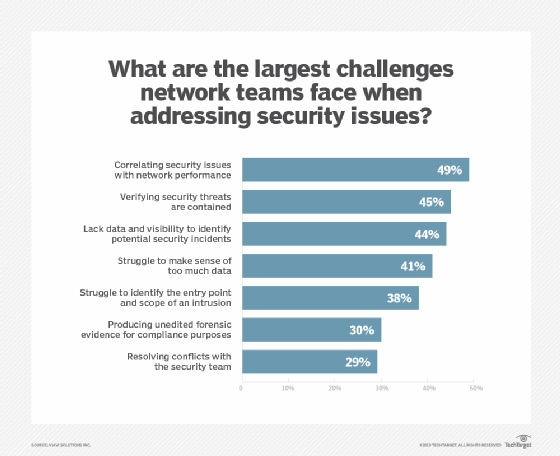
Device malware detection tools not only monitor file trajectory on the local device, but also use network packet trajectory to help determine if malware has propagated to other devices on the network. This added level of visibility can better identify communications among compromised devices. Security administrators can then isolate affected devices or networks more quickly, which leads to faster resolution times and better guarantees that the malware was eradicated.
Monitoring baseline traffic flows is also a key part of identifying malicious activity on a network. If an unexpected change in data flows occurs, it could indicate nefarious activity is taking place.
Alternatively, the improper configuration of internal devices can be spotted using flow analysis. For example, flow analysis can monitor and trigger alerts on endpoints that have been hardcoded with unauthorized DNS servers. The automated nature of this analysis also eases the burden on human administrators who would normally have to hunt down these mistakes manually.
Another way network packet and flow analysis can bolster data security is when a device or group of devices start talking with internet-located resources when they shouldn't be communicating with them. This is especially helpful when managing the security of autonomous devices, such as IoT sensors.
For example, consider this scenario: Your IT security team is alerted that some IP surveillance cameras are suddenly streaming video content to China. Security tools can identify this change in flow behavior and send out alerts. Additionally, automated incident response processes could be built to immediately block the streaming video from exiting the corporate network.
Big data, AI and APIs empower visibility and security
There are three technology trends are driving this merger of network visibility and monitoring tools with data security tools.
The first trend is the shift toward big data collection. The amount of network flow telemetry data and data collection sources in modern enterprise networks is staggering when compared to just a few years ago. Yet, just because you have more data points doesn't mean you can handle it all.
That leads us to the second technology trend -- advanced data inspection and analysis. The use of AI is the only way all the network data can be analyzed to provide meaningful security insights in a timely manner.
Finally, the shift from proprietary, closed network monitoring and security platforms to open APIs is the third trend tying together network visibility and monitoring with data security tools. Because one platform can collect data and export it easily into another, network performance monitoring data can also be sent to one or more security tools for data security analysis.
Combined, these three trends are blurring the line between network and security tools. They might mean a rethinking of how network and security teams cooperate, but these trends do signal the potential for better enterprise security going forward.







