7 must-know IAM standards in 2025
Does your IAM program need OAuth or OpenID Connect? Or maybe both? Let's look at the various standards and protocols that make identity management function.
Identity and access management handles user authentication, authorization and access management across company resources. It's a broad discipline, involving everything from provisioning and deprovisioning, single sign-on, MFA and privileged access management to machine identity management.
Because IAM involves so many tasks, no single technology or standard fully addresses everything in it. Use cases and environments differ across organizations and industries.
What's emerged over decades are several standards, including the following:
- Authentication, authorization and accounting (AAA).
- OAuth 2.0.
- OpenID Connect (OIDC).
- Security Assertion Markup Language (SAML).
- System for Cross-domain Identity Management (SCIM).
- Lightweight Directory Access Protocol (LDAP).
- Interoperability Profiling for Secure Identity in the Enterprise (IPSIE).
When combined with best practices, IAM standards help organizations gain important benefits, including the following:
- Enhanced security. IAM standards provide mechanisms for authenticating users and controlling access, reducing the risk of unauthorized access and data breaches.
- Regulatory compliance. Implementation of IAM standards helps organizations comply with regulatory requirements.
- Interoperability. Standards ensure that different IAM systems and components can work together.
- UX. Standardized IAM processes can streamline user access across multiple systems, enhancing productivity and overall experience.
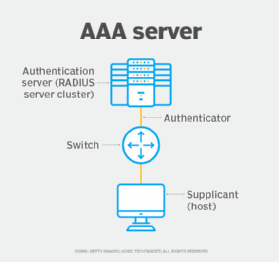
1. AAA
AAA is a security framework that controls network access by first verifying a user's identity (authentication), then determining what they're allowed to do (authorization) and, finally, tracking their resource usage (accounting).
How it works
AAA uses a client-server model that is typically managed through industry standard protocols. RADIUS is commonly used for network access. Terminal Access Controller Access-Control System Plus, or TACACS+, is used for device administration. Diameter is an enhanced version of RADIUS, running on dedicated servers that handle all three AAA steps.
Target use case
The AAA framework can work for organizations of all sizes, as it provides a structured approach that can be scaled and adapted to meet various requirements.
Pros
- Improves network security.
- Centralizes protocol management.
- Allows granular control and flexibility.
- Provides scalable access management.
Cons
- Can be complex to implement fully.
- Requires ongoing maintenance and updates.
2. OAuth 2.0
OAuth 2.0 is an authorization framework that enables third-party applications to obtain limited access to user accounts on an HTTP service.
How it works
OAuth 2.0 works by allowing a user to grant a third-party application limited access to their resources on another service without sharing the actual login credentials. The process involves the third-party app requesting access and the user approving it through the service's authorization server, which then provides the app with a temporary access token that can be used to access only the specifically permitted resources.
Target use case
OAuth 2.0 is particularly well suited for organizations developing modern web and mobile applications, especially those integrating with third-party services.
Pros
- Allows secure data sharing without exposing user credentials.
- Uses tokens instead of username and password for accessing resources.
- Provides granular access control for specific resources for specific durations.
Cons
- Primarily designed for authorization, not authentication.
- Can be susceptible to security vulnerabilities if not implemented correctly.
3. OIDC
OIDC is an authentication protocol built on top of OAuth 2.0 that enables single sign-on (SSO) and standardized user authentication.
How it works
OIDC works by redirecting users who want to access an application to an identity provider, such as Google or Microsoft, that can verify who they are. After successful authentication, the identity provider sends back a secure token containing the user's identity information to the application, allowing the user to access the service without creating new credentials.
Target use case
OIDC is an excellent choice for organizations building new applications from scratch, especially those targeting mobile platforms.
Pros
- Combines authentication and authorization.
- Supports mobile applications, APIs and browser-based applications.
- Uses JSON Web Tokens for easier implementation.
Cons
- Requires trust in third-party authentication services.
- May face service disruption if identity provider experiences downtime.
- If compromised, a single credential could affect multiple service accesses.
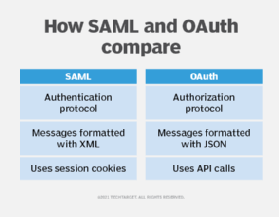
4. SAML
SAML is an XML-based standard for exchanging authentication and authorization data.
How it works
SAML works by enabling secure communication between an identity provider, such as an organization's main login system, and a third-party application. The identity provider confirms a user's identity to the service provider through digitally signed XML messages.
Target use case
SAML is ideal for large enterprises and organizations with existing XML infrastructure, particularly those requiring SSO across multiple internal applications.
Pros
- Offers extensive security for SSO in enterprise environments.
- Supports detailed user information exchange.
- Is well established in large organizations and government entities.
Cons
- Complex XML schemas can be challenging to implement.
- Is less suitable for mobile applications.
5. SCIM
SCIM is an open standard that automates cross-domain user account provisioning. Unlike SAML and OIDC, which handle authentication, SCIM manages user provisioning. SCIM can work together with SAML and OIDC to provide comprehensive identity management.
How it works
SCIM automatically synchronizes user account information between different domains or systems. When changes occur in the source system, SCIM automatically updates the corresponding user accounts in the target system, eliminating the need for manual account management.
Target use case
SCIM is valuable for organizations with complex user management, especially those dealing with frequent employee turnover or changes in access requirements.
Pros
- Streamlines user provisioning and deprovisioning.
- Reduces manual errors in user management.
Cons
- Primarily focuses on user lifecycle management, not authentication or authorization.
6. LDAP
LDAP is a software protocol that helps locate information about organizations, individuals and resources on networks.
How it works
LDAP works by providing a centralized directory service where information about users, organizations and resources is stored in a hierarchical tree structure that can be queried. When a user or application needs to find information or authenticate, LDAP establishes a secure connection to the directory server, validates the user's credentials and returns the requested information based on the user's authorization level.
Target use case
LDAP's primary use is centralized authentication and directory services.
Pros
- Centralizes authentication and user management.
- Is a lightweight and efficient protocol.
- Is an industry standard with wide support.
Cons
- Is not designed for frequent data updates.
- Is vulnerable if not properly configured.
- Is limited to hierarchical data structures.
- Can become a single point of failure.
7. IPSIE
The IPSIE Working Group is a recent initiative by the OpenID Foundation. While not a standard itself, IPSIE aims to develop secure-by-design profiles of existing specifications to enhance interoperability in enterprise implementations.
How it works
IPSIE creates standardized profiles of existing identity security protocols to ensure consistent implementation across enterprise SaaS applications and identity providers. It enables different systems to communicate and share security information in a unified way, coordinating everything from user authentication and access management to risk detection and session control.
Target use case
IPSIE targets enterprises that need standardized identity security across multiple SaaS applications to ensure consistent authentication, access control and security monitoring.
Pros
- Standardizes identity security across multiple SaaS applications.
- Is backed by major tech companies, e.g., Microsoft and Google.
- Uses existing protocols rather than creating new ones.
Cons
- Is still in early development.
- Requires widespread adoption to be effective.
- Is limited to enterprise SaaS use cases.
Sean Michael Kerner is an IT consultant, technology enthusiast and tinkerer. He has pulled Token Ring, configured NetWare and been known to compile his own Linux kernel. He consults with industry and media organizations on technology issues.








