
alphaspirit - Fotolia
Information security certification guide: Intermediate level
Part two of this information security certificate guide looks at vendor-neutral intermediate certifications for IT professionals interested in midlevel positions.
Experience can be the best instructor, but security professionals may find that instruction coupled with more advanced certifications can help further their careers. While introductory certifications may help novices get a foot in the door, an intermediate information security certification or two may help them take the next step.
This report comprehensively reviews the current state of intermediate security certifications, highlighting which are best for achieving goals specific to an information security career path. It's a companion to three other articles, which cover the vendor-specific information security certification landscape, vendor-neutral certification career paths and cloud security certifications in detail.
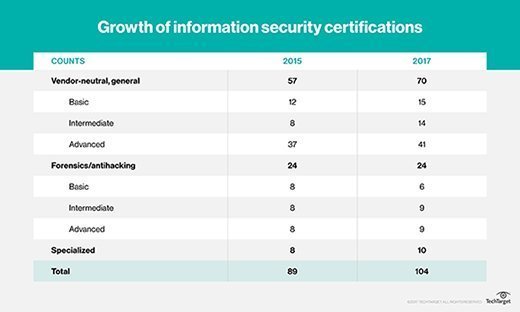
Several changes have been made for this updated cybersecurity certifications guide. The following table shows the number of certifications in the 2015 edition, as well as this 2017 edition. The overall numbers for vendor-neutral information security certifications increased by about 14%. Several certifications have been discontinued, and 19 credentials have been added. Some certifications have been moved to new categories to more accurately classify them.
Some of the notable new entries in this information security certification guide include the CompTIA Cybersecurity Analyst certification and two new EC-Council certs: the EC-Council Certified Network Defender and the EC-Council Certified Encryption Specialist.
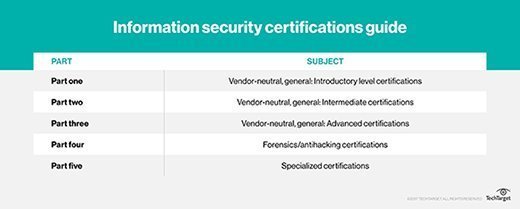
Part three of this information security certification guide offers advanced options for more experienced professionals. Part four includes certifications for forensics and anti-hacking, and part five covers more specialized certifications.
Editor's note: The credentials are listed in alphabetical order within each section.
General Cybersecurity certifications -- Intermediate
(ISC)2 Certified Authorization Professional (CAP)
The (ISC)2 Certified Authorization Professional certification identifies individuals possessing "skills and abilities required for personnel involved in the process of authorizing and maintaining information systems," according to (ISC)2. "Specifically, this credential applies to those responsible for formalizing processes used to assess risk and establish security requirements and documentation. Their decisions will ensure that information systems possess security commensurate with the level of exposure to potential risk, as well as damage to assets or individuals."
 Ed Tittel
Ed Tittel
In particular, this credential confirms that the holder has the knowledge, skill and experience necessary to authorize and maintain systems within the Risk Management Framework described in the NIST SP 800-37 Rev 1 specification. Candidates must have two years of full-time experience in one or more of the seven domains of the CAP Common Body of Knowledge. It's also recommended that candidates possess one to two years of general technical, database, systems development and network experience, along with two years of general systems experience.
Candidates must also prove technical or auditing experience within the government, U.S. Department of Defense or specific industry sectors.
(ISC)2 offers the Associate of (ISC)2 credential for candidates who pass the CAP, Certified Cyber Forensic Professional, Certified Cloud Security Professional, Certified Information Systems Security Professional, Certified Secure Software Lifecycle Professional, HealthCare Information Security and Privacy Practitioners, or Systems Security Certified Practitioner exam, but do not yet meet the experience requirement.
Source: (ISC)² Certified Authorization Professional
Mile2 Certified Incident Handling Engineer (CIHE)
The Mile2 CIHE certification recognizes security professionals who work to prevent attacks on their organization's IT infrastructure, and those who participate in incident response to successful cyberattacks. Certification candidates are expected to be familiar with common hacking approaches and techniques, safeguards, incident handling procedures, and techniques for quickly recovering from attacks.
Mile2 recommends that candidates have at least 12 months of networking experience, as well as knowledge of TCP/IP, Microsoft packages and Linux before taking the associated course and exam.
Source: Mile2 Certified Incident Handling Engineer
EC-Council Certified Network Defender (CND)
Holders of the EC-Council CND certification have deep knowledge of network security controls and protocols, and know how to manage equipment and appliances -- firewalls, intrusion detection, etc. -- that protect networks from attack. Other skills include network traffic analysis, vulnerability scanning and assessment, network security policy maintenance, and creation of incident response plans.
The skills required for this credential align with the National Initiative of Cybersecurity Education framework, and they map to Department of Defense job roles for system/network administrators. Candidates must take a course and pass the certification exam.
Source: EC-Council Certified Network Defender
CompTIA Cybersecurity Analyst (CSA+)
The CompTIA CSA+ certification is a vendor-neutral credential designed to certify professionals who have three to four years of security and behavioral analytics experience. A CSA+ commonly works with data collected by network protocol analyzers, network intrusion detection systems, and security information and event management software.
For candidates climbing the CompTIA certification ladder, the CSA+ is the next rung above Security+ and just below the advanced-level CompTIA Advanced Security Practitioner.
Source: CompTIA Cybersecurity Analyst
(ISC)² Certified Secure Software Lifecycle Professional (CSSLP)
The (ISC)² CSSLP certification recognizes individuals who specialize in software security across the lifecycle, from conceptualization and design, through coding, testing and deployment.
Candidates must have at least four years of direct experience in the software development lifecycle in one or more of the eight domains covered in the CSSLP Common Body of Knowledge, agree to adhere to a code of ethics, answer questions regarding their criminal history and background, and pass one exam.
Candidates who lack the requisite experience may become an Associate of (ISC)2 by passing the CSSLP exam. Those obtaining the Associate credential have five years to gain the required experience in order to upgrade the certification.
Source: (ISC)² Certified Secure Software Lifecycle Professional
Mile2 Certified Wireless Security Engineer (CWSE)
The Mile2 CWSE certification is geared toward network administrators, systems engineers, IT managers and security consultants who are responsible for the security of one or more wireless local area networks (WLANs). Certification candidates must be familiar with WLAN security concepts, legacy security, common attacks, WLAN auditing and more.
Prerequisites for the CWSE certification are the Mile2 Certified Security Sentinel and Certified Information Systems Security Officer certifications, or at least 12 months of networking experience. Candidates must pass one exam to achieve certification.
Source: Mile2 Certified Wireless Security Engineer
CertiTrek Group Certified Wireless Security Professional (CWSP)
Made available by the CertiTrek Certified Wireless Network Professional (CWNP) Wi-Fi certification and training unit, the CWSP credential recognizes individuals who can design, implement and manage wireless LAN security.
To obtain this credential, candidates must pass one exam.
Source: CWNP Certified Wireless Security Professional
EC-Council Certified Encryption Specialist (ECES)
The EC-Council ECES recognizes IT professionals who can select and apply symmetric and asymmetric cryptography, common algorithms and hashing algorithms. A professional with the ECES credential can also set up a virtual private network, select and implement digital certificates, encrypt a drive, and use a variety of steganography tools.
To obtain ECES certification, a candidate needs to complete a three-day course and pass one exam.
Source: EC-Council Certified Encryption Specialist
SANS Institute Global Information Assurance Certification Program (GIAC)
SANS is well-known for timely, focused and useful security information and training courses. SANS offers regular in-person training, as well as online classes, and uses such classes to draw attendees to their frequent, well-situated, week-long conferences.
SANS created the GIAC program to administer certifications related to SANS training. The GIAC program seeks to identify individuals who can demonstrate both knowledge of and the ability to manage and protect important information systems and networks.
Overall, the GIAC program aims at serious, full-time security professionals responsible for designing, implementing and maintaining a state-of-the-art security infrastructure, which may include incident handling and emergency response team management. Available intermediate-level GIAC credentials include the following:
- GIAC Security Essentials Certification
- GIAC Information Security Professional
- GIAC Certified Incident Handler
- Global Industrial Cyber Security Professional
Source: SANS Global Information Assurance Certification
Security University Qualified/Certification & Accreditation certification (Q/CA)
Security University's Q/CA is for system certifiers and validators who need cybersecurity skills. The class identifies individuals who can assess security skills to certify and validate systems and manage the security threats within an organization, particularly in the government and enterprise sectors.
The class has several labs on security controls and ends with a certification and accreditation validation practical. The Q/CA class meets the objectives of the National Security Agency's Committee on National Security Systems 4016A for a Fully Qualified Navy Validator.
Source: Security University Qualified Certification & Accreditation certification
Security University Qualified/Wireless Security Professional (Q/WSP)
Security University's Q/WSP identifies and validates individuals who can architect and install wireless networks and manage and mitigate risk. Candidates must pass one exam.
Source: Security University Qualified/Wireless Security Professional
About the author:
Ed Tittel is a 30-plus year IT veteran who's worked as a developer, networking consultant, technical trainer, writer and expert witness. Perhaps best known for creating the Exam Cram series, he has contributed to more than 100 books on many computing topics, including titles on information security, Windows OSes and HTML.






