
alphaspirit - Fotolia
Information security certification guide: Forensics
This information security certificate guide looks at vendor-neutral computer forensics certifications for IT professionals interested in cyber attribution and investigations.
While the work of all information security professionals is important, those working in the field of cybersecurity forensics play an especially pivotal role in the attribution of cyberattacks and the apprehension of perpetrators.
A thorough knowledge of information security practices and concepts is necessary for most forensics operators, but knowledge alone is not enough to be sure that evidence is collected, retained and interpreted reliably -- especially when failures in handling computer evidence could enable an innocent person to be sent to prison or a guilty one to be set free. An information security certification in forensics focuses on identifying, collecting and analyzing evidence in cybercrime incidents and nation-state cyberattacks.
This report comprehensively reviews the current state of information security certifications for computer forensics at all levels -- from beginner to advanced -- highlighting which are best for achieving goals specific to an information security career path.
This series is a companion to three other articles that cover the vendor-specific information security certification landscape, vendor-neutral certification career paths and cloud security certifications in detail.
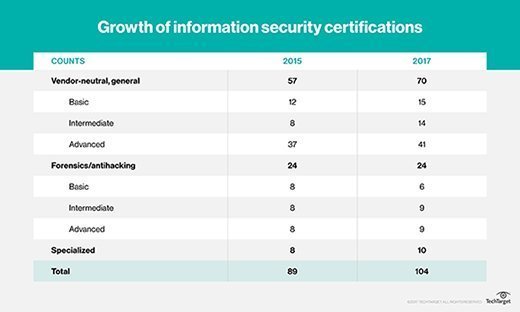
Several changes have been made for this updated information security certification guide. The following table shows the number of certifications in the 2015 edition, as well as this 2018 edition. The overall numbers for vendor-neutral information security certifications increased by about 14%. Several certifications have been discontinued, and 19 credentials have been added. Some certifications have been moved to new categories to more accurately categorize them.
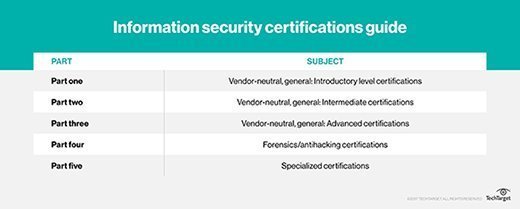
Part one of this information security certification guide series covers certifications suitable for newcomers to the industry. Part two covers intermediate certifications, and part three includes advanced information security certifications. Part five includes more specialized cybersecurity certifications.
Editor's note: The credentials are listed in alphabetical order within each section.
Forensics: Basic
Brainbench Computer Forensics (U.S.) (BCF)
The Brainbench Computer Forensics (U.S.) certification is designed to recognize experienced users who are able to analyze and collect evidence, recognize data types, follow proper examination procedures and initial analysis, use forensic tools, prepare for an investigation and report findings.
There are no prerequisites or requirements for this certification, but the exam is designed for experienced users.
Source: Brainbench Computer Forensics (U.S.)
High Tech Crime Network Certified Computer Crime Investigator -- Basic and Certified Computer Forensic Technician -- Basic
High Tech Crime Network offers four computer forensics certifications for law enforcement and private sector IT professionals seeking to specialize in the investigative side of the field. These certifications include two basic computer forensics certifications: Computer Crime Investigator (CCCI) -- Basic and Computer Forensic Technician (CCFT) -- Basic.
Basic requirements for both of these certifications include three years of experience -- whether law enforcement or corporate -- 40 hours of computer crimes training, and documented experience from at least 10 case investigations.
Mile2 Certified Digital Forensics Examiner
The Certified Digital Forensics Examiner (CDFE) certification targets cybercrime investigators who work with digital evidence and use electronic discovery techniques. Exam topics may include disk storage, seizure and collection techniques, forensic examination, artifact recovery, and more.
Other than a minimum of one year of experience working in computing, no prerequisites or courses are required for the CDFE certification, but some hands-on experience will benefit the certification candidate.
Source: Mile2 Certified Digital Forensics Examiner
EC-Council Certified Incident Handler
The EC-Council Certified Incident Handler (ECIH) is geared toward incident handlers, risk assessment administrators, penetration testers, cyberforensic investigators and vulnerability assessment auditors, among others. A professional with the ECIH credential knows how to respond to computer security incidents -- whether they originate from an internal or external source -- understands laws and policies related to security incidents, and performs risk assessments.
To obtain the ECIH certification, a candidate needs to complete a two-day course and pass one exam.
Source: EC-Council Certified Incident Handler
EC-Council Disaster Recovery Professional
The EC-Council Disaster Recovery Professional (EDRP) validates individuals with the ability to develop and test disaster recovery plans in an enterprise environment. This includes creating a secure network by implementing the appropriate policies and procedures and restoring a network in the event of a disaster.
To obtain the EDRP certification, a candidate must pass one exam; a two-day course is optional.
Forensics: Intermediate
International Society of Forensic Computer Examiners Certified Computer Examiner
The Certified Computer Examiner (CCE) certification is administered by the International Society of Forensic Computer Examiners, and it identifies individuals who have the appropriate computer forensics training or experience, including evidence gathering, handling and storage.
In addition, candidates for the CCE certification must do one of the following: attend authorized training, have at least 18 months of experience conducting digital forensic examinations, or have documented self-study in digital forensics deemed appropriate by the Certification Board. Candidates must also pass an online examination, have no criminal record and successfully perform a hands-on examination.
Source: International Society of Forensic Computer Examiners Certified Computer Examiner
EC-Council Certified Ethical Hacker
The Certified Ethical Hacker (CEH) recognizes security professionals capable of finding and detecting weaknesses and vulnerabilities in computer systems and networks by using the same tools and applying the same knowledge as a malicious hacker.
Candidates with at least two years of information security experience can take the approved training or complete an eligibility form, and then must pass a single exam to receive the CEH certification.
Source: EC-Council Certified Ethical Hacker
International Association of Computer Investigative Specialists Certified Forensic Computer Examiner
The International Association of Computer Investigative Specialists offers the Certified Forensic Computer Examiner (CFCE) certification to law enforcement and private industry personnel alike.
Candidates must have broad knowledge, training or experience in computer forensics, including forensic procedures and standards, as well as ethical, legal and privacy issues. CFCE certification requires an intensive peer review, hands-on performance-based testing, as well as a written exam.
A background check is also required unless the applicant is a full-time law enforcement or government employee whose employer can verify their qualification, or unless the applicant has a verifiable government clearance or security rating.
Source: International Association of Computer Investigative Specialists Certified Forensic Computer Examiner
EC-Council Computer Hacking Forensic Investigator
The Computer Hacking Forensic Investigator (CHFI) credential is intended to certify personnel involved in computer forensics and working in law enforcement, defense, military, information technology, law, banking and insurance, among other industries.
A CHFI-certified professional should be able to perform a wide variety of tasks related to investigating cybercrimes, such as serving as a first responder at digital crime scenes, gathering and examining evidence, recovering files, and performing steganalysis.
To obtain the CHFI certification, a candidate needs to successfully complete one exam.
Source: EC-Council Computer Hacking Forensic Investigator
EC-Council Certified Network Defense Architect
The Certified Network Defense Architect (CNDA) certification is geared toward IT personnel who act as penetration testers or legitimate hackers to test the strength and integrity of a network's defense. The CNDA exam is identical to the CEH exam; however, the CNDA program was designed for U.S. government and military agencies.
To obtain the CNDA certification, a candidate needs to successfully complete one exam and be employed by the U.S. government.
Source: EC-Council Certified Network Defense Architect
Mile2 Certified Network Forensics Examiner
The Certified Network Forensics Examiner (CNFE) certification was originally developed for a classified U.S. government agency to certify the skills of security professionals working in U.S. government agencies who perform network forensic examinations and generate reports based on their findings. Certification candidates must have practical experience with forensic investigations, network data recovery, traffic capture and analysis, wireless attacks, and intrusion detection and prevention systems.
Although Mile2 categorizes the CNFE as an advanced-level certification, it falls into the intermediate level for the purposes of this article, with two years of networking experience and two years of IT security experience required. Candidates must pass one exam to achieve certification.
Source: Mile2 Certified Network Forensics Examiner
CyberSecurity Institute CyberSecurity Forensic Analyst
The CyberSecurity Forensic Analyst (CSFA) recognizes individuals who are able to perform a comprehensive and sound forensic examination of a computer system and other digital/electronic devices within a limited time frame. Suggested prerequisites for the CSFA include at least one of the following certifications:
- AccessData Certified Examiner
- Certified Forensic Computer Examiner
- Certified Computer Examiner
- Computer Hacking Forensic Investigator
- EnCase Certified Examiner
- Global Information Assurance Certification Certified Forensics Analyst
In addition, candidates should have at least two years of experience performing forensic analysis on devices running a Windows operating system; writing forensic analysis reports; and creating content for subpoenas, affidavits and so forth.
Candidates must have no criminal record. An FBI background check is required before any candidate can sit for the exam.
Source: CyberSecurity Institute CyberSecurity Forensic Analyst
EC-Council Certified Security Analyst
The EC-Council Certified Security Analyst (ECSA) identifies security professionals capable of using advanced penetration testing methodologies, tools and techniques to analyze and interpret security tests.
Candidates must pass a single exam to achieve the ECSA certification. The EC-Council recommends candidates take a five-day training course to prepare for the exam.
Source: EC-Council Certified Security Analyst
Global Information Assurance Certification Certified Forensic Examiner
This certification is part of the Global Information Assurance Certification (GIAC) program. The GIAC Certified Forensic Examiner (GCFE) identifies professionals with the required skills to collect and analyze data from Windows computers. The GCFE certification is geared toward professionals in the information security profession and the legal and law enforcement industries.
No specific training or prerequisites are required, though candidates are urged to have taken related courses or acquired skills through practical experience. Candidates must pass one exam, and the certification is valid for four years.
Source: GIAC Certified Forensic Examiner
Forensics: Advanced
High Tech Crime Network Certified Computer Crime Investigator -- Advanced
The CCCI -- Advanced is one of four computer forensic certifications offered by the High Tech Crime Network aimed at law enforcement and private IT professionals seeking to specialize in the investigative side of the field.
Candidates must have at least five years of experience directly related to technical investigations, either in law enforcement or a corporate setting; must complete 80 hours of approved training; and must serve as the lead investigator on 20 cases, as well as have responsible involvement in an additional 40 cases. Also required is submission of a report documenting experience with at least 15 investigated cases.
Source: High Tech Crime Network Certified Computer Crime Investigator -- Advanced
(ISC)2 Certified Cyber Forensics Professional
The (ISC)2 Certified Cyber Forensics Professional (CCFP) credential recognizes professionals who possess established forensic skills across a variety of existing and emerging technologies. Certificate holders demonstrate competence in mobile and cloud forensics; anti-forensics; forensic standards of practice; forensics as it relates to cross-security disciplines, including incident response, malware and e-discovery; and digital evidence.
Candidates must pass an extensive exam demonstrating competency in the following six domains of the CCFP Common Body of Knowledge (CBK):
- Legal and Ethical Principles
- Investigations
- Forensic Science
- Digital Forensics
- Application Forensics
- Hybrid and Emerging Technologies
A four-year degree is required, plus three years of experience in three of the six CBK domains. Six years of experience is required for candidates who do not possess a bachelor's degree. Upon approval, (ISC)2 may allow candidates with other computer forensic certifications to waive one year of the required experience.
(ISC)2 offers the Associate of (ISC)2 credential for candidates who pass the Certified Authorization Professional, Certified Cyber Forensics Professional, Certified Cloud Security Professional, Certified Information Systems Security Professional, Certified Secure Software Lifecycle Professional, HealthCare Information Security and Privacy Practitioner or Systems Security Certified Practitioner exam, but do not yet meet the experience requirement.
Source: (ISC)2 Certified Cyber Forensics Professional
High Tech Crime Network Certified Computer Forensic Technician -- Advanced
CCFT -- Advanced is one of four computer forensic certifications that recognize law enforcement and private IT professionals seeking to certify their skills in forensic evidence acquisition and analysis.
Basic requirements include five years of experience; 80 hours of computer forensics training; involvement as lead forensic technician, supervisor or support team member in a minimum of 40 cases; involvement as a lead investigator in 20 cases; and documented experience from at least 15 investigated cases that focused on computer crimes.
Source: High Tech Crime Network Certified Computer Forensic Technician -- Advanced
Mile2 Certified Penetration Testing Consultant
The Certified Penetration Testing Consultant (CPTC) credential certifies security professionals capable of conducting penetration testing operations against large network infrastructures, such as enterprise networks, networking services providers and telecommunications providers. The focus is on the use of penetration testing tools and techniques against network infrastructure targets rather than individual systems, with coverage of network routing protocols.
Mile2 offers a four-day training course for the CPTC certification and candidates must pass an exam to receive it.
Source: Mile2 Certified Penetration Testing Consultant
GIAC Certified Forensics Analyst
The GIAC Certified Forensics Analyst (GCFA) certification, which is a component of the GIAC information security certification program, recognizes professionals with the required skills to collect and analyze data from Windows and Linux computers. Professionals with the GCFA have the ability to conduct formal incident investigations and take a lead role in responding to security incidents.
No training or prerequisites are required. Candidates must pass one exam, and the certification is valid for four years.
Source: GIAC Certified Forensics Analyst
GIAC Network Forensic Analyst
The GIAC Network Forensic Analyst (GNFA) credential, which is a component of the GIAC information security certification program, recognizes professionals who demonstrate the skills required to perform network forensic artifact analysis, including the ability to recognize abnormal network traffic and use a variety of device and system log examination tools, and who are highly familiar with wireless communication and encrypted protocols.
No training or prerequisites are required for the GNFA certification. Candidates must pass one exam, and the certification is valid for four years.
Source: GIAC Network Forensic Analyst
GIAC Reverse Engineering Malware
The GIAC Reverse Engineering Malware (GREM) certificate is awarded to technologists who are experts at protecting organizations from malicious code.
Successful candidates can be expected to understand how malicious code affects forensic investigations, incident response and Windows system administration. An individual with a GREM certification can be expected to thoroughly understand the process of reverse-engineering malware associated with Microsoft Windows and web browsers.
No training or prerequisites are required. Candidates must pass one exam, and the certification is valid for four years.
Source: GIAC Reverse Engineering Malware
EC-Council Licensed Penetration Tester
The Licensed Penetration Tester (LPT) certification recognizes security professionals who have demonstrated mastery of penetration testing skills, including the ability to analyze a network, identify where and how it could potentially be penetrated, and recommend appropriate corrective measures.
LPT-certified professionals are expected to adhere to a strict code of ethics, best practices and appropriate compliance requirements when performing penetration tests. Prerequisites include a current EC-Council ECSA certification or at least two years of penetration testing experience, submission of the LPT application, proof of a clean background check, a detailed resume, an agreement to abide by a code of ethics, and payment of an application fee.
Source: EC-Council Licensed Penetration Tester
ASIS International Professional Certified Investigator
The Professional Certified Investigator (PCI) credential is a high-level information security certification from the American Society for Industrial Security (ASIS), which is also home to the Certified Protection Professional and Physical Security Professional certifications.
The PCI certification recognizes security professionals who specialize in investigating cybercrimes. In addition to technical skills, this certification tests a candidates knowledge of the legal and evidentiary matters required to present investigations in a court of law, as well as case management, investigative procedures and case presentation.
This certificate requires five years of investigation experience, with at least two years in case management, a high school diploma -- or GED -- and a clean criminal record.
Source: ASIS International Professional Certified Investigator







