
alphaspirit - Fotolia
Information security certification guide: Advanced level
Part three of this information security certification guide looks at vendor-neutral advanced security certifications for more experienced IT professionals.
Years of experience may be a requirement for some high-level cybersecurity positions, but it never hurts to get those years of experience validated with one or more advanced security certifications. And while midlevel certifications can help advance a cybersecurity career, advanced certifications may help propel a solid candidate to the next level.
This report comprehensively reviews the current state of advanced security certifications, highlighting the ones that are best for advancing an information security career path. This information security certification guide is a companion to three other articles that cover the vendor-specific information security certification landscape, vendor-neutral certification career paths and cloud security certifications in detail.
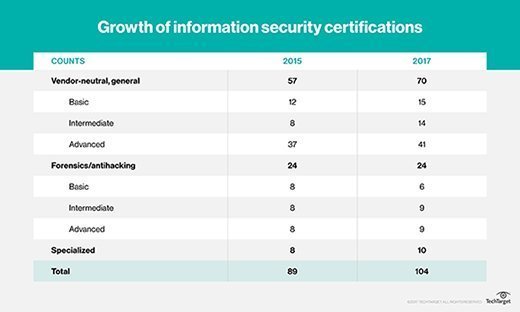
Several changes have been made for this updated information security certification guide series. The following table shows the number of certifications in the 2015 edition, as well as this 2018 edition. The overall numbers for vendor-neutral information security certifications have increased by about 14%. Several certifications have been discontinued, and 19 credentials have been added. Some certifications have been moved to categories to more accurately categorize them.
The information security certification space continues to evolve and expand, and some introductory certifications covered in the part of this series that are worth watching over the next few years include the CyberSec Responder by Logical Operations and the Cybersecurity Nexus CSX Practitioner by Information Systems Audit and Control Association (ISACA).
Some of the and notable intermediate information security certifications covered in the second part of this series include the CompTIA Cybersecurity Analyst certification and two EC-Council certs: EC-Council Certified Network Defender and EC-Council Certified Encryption Specialist. However, the list of advanced security certifications has remained largely unchanged from recent years.
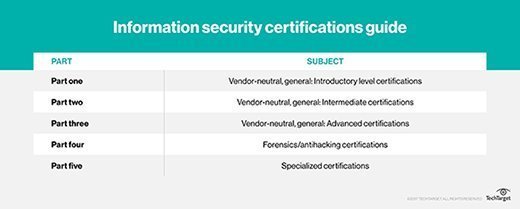
Part one of this information security certification guide series covers introductory certifications, and part two covers intermediate certifications. Part four includes certifications for forensics and antihacking, and part five covers more specialized cybersecurity certifications.
Editor's note: The credentials are listed in alphabetical order.
General Information Security Certifications: Advanced
CompTIA Advanced Security Practitioner
The CompTIA Advanced Security Practitioner (CASP) certification is one of a few advanced credentials that CompTIA offers. It has been accredited as a valid credential under U.S. Department of Defense Directive 8570.01-M, which is designed to prepare the information assurance -- government-speak for information security -- workforce to prevent and respond to attacks against the agency's and its contractors' information, information systems and information infrastructures.
This exam seeks to cover technical skills and the knowledge needed to conceptualize, design and implement secure solutions across complex enterprise environments. There are no prerequisites; however, CompTIA recommends that candidates have 10 years of IT administration experience, five of which involved hands-on technical security experience, before attempting the CASP exam.
Source: CompTIA Advanced Security Practitioner
Carnegie Melon Software Engineering Institute (SEI) CERT-Certified Computer Security Incident Handler
The Carnegie Mellon SEI CERT-Certified Computer Security Incident Handler (CERT-CCSIH) credential recognizes security professionals who are knowledgeable of and skilled in network monitoring and risk assessments, Vulnerability scanning, and other infrastructure protection techniques, as well as incident detection and incident response.
Candidates must have one or more years of recent experience in incident handling in a technical or management role, must submit a certification recommendation form signed by a current manager, and must pass one exam. The credential is valid for three years.
Source: Carnegie Mellon SEI CERT-Certified Computer Security Incident Handler
ISACA Certified Information Security Manager
ISACA's Certified Information Security Manager (CISM) certification recognizes knowledge of information security for IT professionals responsible for handling security matters, issues and technologies. This management-focused certification should be of primary interest to IT professionals responsible for managing IT systems, networks, policies, practices and procedures to make sure organizational security policies meet governmental and regulatory requirements, conform to best security practices and principles, and meet or exceed requirements stated in an organization's security policy.
Candidates for CISM must have five or more years of information security work experience.
Source: ISACA Certified Information Security Manager
Mile2 Certified Information Systems Security Officer
This credential from Mile2 certifies individuals who can apply risk analysis, mitigation techniques, application security, secure networks and operations, and who can for business continuity and disaster recovery. A Certified Information Systems Security Officer (CISSO) can assess an IT infrastructure for today's threats and risks and design a security program to mitigate those risks.
The CISSO is Mile2's alternative to the (ISC)2 Certified Information Systems Security Professional certification. The CISSO credential has been approved by the National Security Agency (NSA) as meeting the security standards for NSTISSI-4011: National Training Standard for Information Systems Security (Infosec) and CNSSI-4012: National Information Assurance Training Standard for Senior Systems Managers.
Source: Mile2 Certified Information Systems Security Officer
(ISC)2 Certified Information Systems Security Professional
The Certified Information Systems Security Professional (CISSP) credential demonstrates knowledge of network and system security principles, safeguards and practices. It is of primary interest to full-time IT security professionals who work in internal security positions or who consult with third parties on security matters.
CISSP holders are expected to be capable of analyzing security requirements, auditing security practices and procedures, designing and implementing security policies, and managing and maintaining an ongoing and effective security infrastructure. CISSP candidates must have five years of experience in two or more of the eight domains of the CISSP Common Body of Knowledge. A four-year college degree or an approved certification may substitute for up to one year of the experience requirement.
(ISC)2 offers the Associate of (ISC)2 credential for candidates who pass the Certified Authorization Professional, Certified Cyber Forensics Professional, Certified Cloud Security Professional, CISSP, Certified Secure Software Lifecycle Professional, HealthCare Information Security and Privacy Practitioner, or Systems Security Certified Practitioner exams, but who do not yet meet the experience requirement.
Source: ISC² Certified Information Systems Security Professional
Mile2 Certified Penetration Testing Engineer
This Mile2 Certified Penetration Testing Engineer (CPTE) credential stresses currency on the latest exploits, vulnerabilities and system penetration techniques. It also focuses on business skills, identification of protection opportunities, testing justifications, and optimization of security controls to meet business needs and control risks and exposures.
The CPTE credential is structured around a five-day course that teaches students penetration testing methodologies and lets students perform a complete penetration test. The CPTE credential is accredited by the NSA Committee on National Security Systems 4011-4016, and it is on the FBI Cyber Security Certification Requirement approved list.
Source: Mile2 Certified Penetration Testing Engineer
ASIS International Certified Protection Professional
The Certified Protection Professional (CPP) certification from ASIS International, an organization for security professionals based in Alexandria, Va., certifies that the holder has demonstrated a thorough understanding of physical, human and information security principles and practices.
CPP requires extensive on-the-job experience -- nine years, or seven years with a college degree, three years of which must be in a position of direct responsibility for security functions -- as well as a profound knowledge of technical and procedural security topics and technologies. Only those who have worked with and around security for a lengthy portion of their careers are able to qualify for this credential.
Source: ASIS International Certified Protection Professional
SANS Institute Global Information Assurance Certification
The SANS Institute offers a number of advanced security certifications to recognize individuals who can demonstrate both knowledge of and the ability to manage and protect important information systems and networks.
Available advanced Global Information Assurance Certification (GIAC) options include the following:
- GIAC Certified Intrusion Analyst (GCIA)
- GIAC Certified Unix Security Administrator (GCUX)
- GIAC Certified Windows Security Administrator (GCWN)
- GIAC Certified Enterprise Defender
- GIAC Penetration Tester
- GIAC Web Application Penetration Tester
- GIAC Continuous Monitoring Certification
- GIAC Critical Controls Certification
- GIAC Security Leadership Certification
- GIAC Certified Project Manager
- GIAC Law of Data Security & Investigations
- GIAC Certified Perimeter Protection Analyst
- GIAC Systems and Network Auditor
- GIAC Mobile Device Security Analyst
- GIAC Advanced Smartphone Forensics
- GIAC Certified Web Application Defender
- GIAC Python Coder
- GIAC Secure Software Programmer -- .NET
- GIAC Secure Software Programmer -- Java
Highly advanced certifications include the following:
- GIAC Assessing and Auditing Wireless Networks
- GIAC Exploit Researcher and Advanced Penetration Tester
Note: Additional GIAC certifications are described in the Forensics: Advanced section of part four of this series.
Source: SANS Institute Global Information Assurance Certification
SANS Institute GIAC Security Expert
The GIAC Security Expert (GSE) track is the most senior-level certification in that program. To qualify for this certification, candidates must:
- achieve the GSE, GCIA and GIAC Certified Incident Handler (GCIH) certifications, earning GIAC Gold in at least two of them, or achieve the GCWN, GCUX, GCIH and GCIA certifications, earning GIAC Gold in one of them;
- pass a proctored multiple-choice exam; and
- successfully complete a two-day hands-on lab.
Source: GIAC Security Expert
(ISC)2 Information Systems Security Architecture Professional
The Information Systems Security Architecture Professional (ISSAP) certification offered by (ISC)2 is a concentration in information security architecture and stresses the following elements of the CISSP Common Body of Knowledge:
- access control systems and methodologies;
- communications and network security;
- cryptography;
- security architecture analysis;
- technology-related business continuity and disaster recovery ; and
- physical security considerations.
A minimum of two years of professional experience is required to obtain the ISSAP credential.
Source: (ISC)2 Information Systems Security Architecture Professional
(ISC)2 Information Systems Security Engineering Professional
The Information Systems Security Engineering Professional (ISSEP) is a CISSP concentration created in cooperation with the NSA. Two years of professional engineering experience is required to obtain the credential. The ISSEP stresses the following elements of the CISSP Common Body of Knowledge:
- systems security engineering;
- Certification and Accreditation and the Risk Management Framework;
- technical management; and
- U.S. government information assurance-related policies and issuances.
A minimum of two years of professional experience is required to obtain the credential.
Source: (ISC)2 Information Systems Security Engineering Professional
(ISC)2 Information Systems Security Management Professional
The Information Systems Security Management Professional (ISSMP) is a CISSP concentration that stresses the following elements of the CISSP Common Body of Knowledge:
- security leadership and management;
- security lifecycle management;
- security compliance management;
- contingency management; and
- law, ethics and incident management.
A minimum of two years of professional experience is required to obtain the ISSMP credential.
Source: (ISC)2 Information Systems Security Management Professional
ASIS International Physical Security Professional
Another high-level security certification from ASIS, this program focuses on matters relevant to maintaining the physical security and integrity of the premises, as well as access controls over the devices and components of an IT infrastructure. Key topics covered by the Physical Security Professional (PSP) include physical security assessment and selection and implementation of appropriate integrated physical security measures.
Requirements for the PSP credential include four years of experience in progressive physical security and a bachelor's degree or higher from an accredited institution of higher education, or a high school diploma -- or GED -- and six years of experience in progressive physical security.
Source: ASIS International Physical Security Professional
Security University Qualified Ethical Hacker
Security University's Qualified Ethical Hacker (Q/EH) certification combines coverage related to securing information systems and networks. Preparation for the Q/EH includes more than 30 hands-on, performance-based labs and a testing program to focus on the tactical skills necessary to conduct penetration testing, as well as security analysis.
Candidates must complete a five-day course, pass one examination and agree to comply with Security University's professional code of ethics.
Source: Security University Qualified Ethical Hacker
Security University Qualified Forensic Expert
Security University's Qualified Forensic Expert (Q/FE) certification focuses on the practical, tactical skills necessary to perform forensic tasks, such as preserving the chain of custody, digital forensic rights, computer forensics, determining the cause of attacks, recovering encrypted data, retrieving data from peripheral and mobile devices, and recovering data from media that has been intentionally damaged.
One exam is required to earn the Q/FE credential.
Source: Security University Qualified Forensic Expert
Security University Qualified Information Assurance Professional
Security University's Qualified Information Assurance Professional (Q/IAP) certification combines coverage of key information assurance topics, tools and technologies that assure that access to critical and often classified information has not been compromised. The Q/IAP) requires hands-on, lab-oriented learning and a skills validation testing program.
To obtain the Q/IAP certification, information assurance professionals must achieve 70% or higher on three Q/IAP exams and complete three practical tests on topics such as:
- access, authentication and public key infrastructure;
- network security policy and security-oriented architecture; and
- the security certification and accreditation process.
Classes are not required. After completing the Q/IAP practicals and successfully passing the associated exams, candidates must be endorsed by a peer in information assurance.
Source: Security University Qualified Information Assurance Professional
Security University Qualified Information Security Professional
Security University's Qualified Information Security Professional (Q/ISP) certification combines coverage of key information cybersecurity topics, tools and technologies with escalating hands-on labs and a performance-based testing program. Candidates may attend four Q/ISP certification classes on the following topics: ethical hacker, security analysis and penetration testing, forensics, and network defender.
To obtain the Q/ISP certification, cybersecurity professionals must complete the four Q/ISP certification classes and the associated certification exams. Alternatively, candidates may certify by taking the Q/ISP exam and successfully completing the required practical exercises.
Source: Security University Qualified Information Security Professional
Security University Qualified Network Defender
Security University's Qualified Network Defender (Q/ND) focuses on skills necessary to protect networks and systems, such as:
- network firewall and router monitoring;
- misconfigurations, data breaches and compromises;
- deep packet analysis -- intrusion defense systems and intrusion prevention systems;
- malware detection;
- reverse engineering;
- best practices for network defense;
- threat analysis and containment; and
- recovery strategies.
Candidates for the Q/ND certification must demonstrate that they possess the tactical skills necessary to secure a network, must agree to a professional code of ethics and must pass an extensive practical exam.
Source: Security University Qualified Network Defender
Security University Qualified Security Analyst Penetration Tester License
Security University's Qualified Security Analyst Penetration Tester License (Q/PTL) program combines key information with escalating hands-on labs that include best practices, step-by-step processes, hacking and penetration testing, security and audit assessment, corrective measures, and assessment and reporting. Security University's penetration testing process and methodology has been used to protect U.S. military networks, pharma networks and the travel industry.
Candidates for the Q/PTL certification must pass a lab practical. Candidates must also:
- achieve the Security University Qualified Ethical Hacker or EC-Council Certified Ethical Hacker credential;
- achieve the Security University Qualified Security Analyst or EC-Council Certified Security Analyst credential; and
- complete the Q/PTL training requirements, including submitting an application, submitting a resume, a criminal background check, a code of ethics agreement and a workshop.
No written exam is required, and the Q/PTL license does not expire.
Source: Security University Qualified Security Analyst Penetration Tester License
Security University Qualified Security Analyst Penetration Tester (non-degree)
Security University's Qualified Security Analyst Penetration Tester (Q/SA) certification focuses on key information and tactical skills. Tactical skills for the Q/SA include areas such as performing vulnerability analysis, penetration testing analysis, information gathering techniques, identifying and exploiting network weaknesses, legal issues, red team skills, writing reports, and more.
Certification candidates are expected to understand TCP/IP protocols.
Source: Security University Qualified Security Analyst Penetration Tester
Security University Qualified Software Security Expert
Security University's Qualified Software Security Expert (Q/SSE) certification covers key software security topics, tools and technologies with escalating hands-on labs and a performance-based testing program. To obtain the Q/SSE certification, security professionals must complete a five-day, three-part software security boot camp that includes topics such as:
- penetration testing;
- breaking and fixing web applications;
- breaking and fixing software;
- secure software programming;
- software security ethical hacking;
- software security testing best practices; and
- reverse engineering.
Candidates must pass an exam to qualify.
Source: Security University Qualified Software Security Expert








